HP Virtual Connect for the Cisco Network Administrator
HP Virtual Connect for the Cisco Network Administrator
HP Virtual Connect for the Cisco Network Administrator
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
34<br />
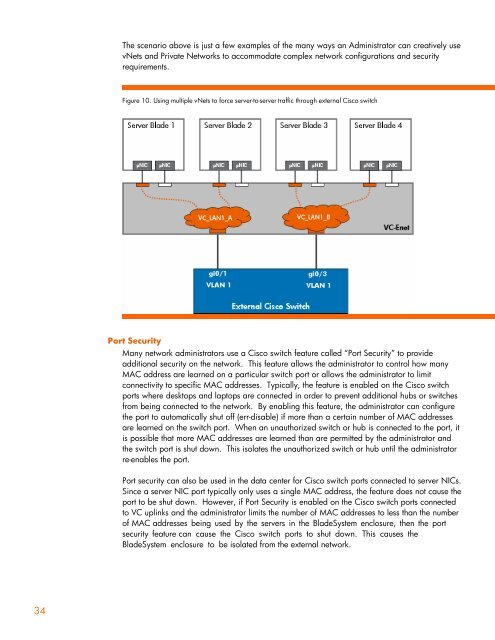
The scenario above is just a few examples of <strong>the</strong> many ways an <strong>Administrator</strong> can creatively use<br />
vNets and Private <strong>Network</strong>s to accommodate complex network configurations and security<br />
requirements.<br />
Figure 10. Using multiple vNets to <strong>for</strong>ce server-to-server traffic through external <strong>Cisco</strong> switch<br />
Port Security<br />
Many network administrators use a <strong>Cisco</strong> switch feature called “Port Security” to provide<br />
additional security on <strong>the</strong> network. This feature allows <strong>the</strong> administrator to control how many<br />
MAC address are learned on a particular switch port or allows <strong>the</strong> administrator to limit<br />
connectivity to specific MAC addresses. Typically, <strong>the</strong> feature is enabled on <strong>the</strong> <strong>Cisco</strong> switch<br />
ports where desktops and laptops are connected in order to prevent additional hubs or switches<br />
from being connected to <strong>the</strong> network. By enabling this feature, <strong>the</strong> administrator can configure<br />
<strong>the</strong> port to automatically shut off (err-disable) if more than a certain number of MAC addresses<br />
are learned on <strong>the</strong> switch port. When an unauthorized switch or hub is connected to <strong>the</strong> port, it<br />
is possible that more MAC addresses are learned than are permitted by <strong>the</strong> administrator and<br />
<strong>the</strong> switch port is shut down. This isolates <strong>the</strong> unauthorized switch or hub until <strong>the</strong> administrator<br />
re-enables <strong>the</strong> port.<br />
Port security can also be used in <strong>the</strong> data center <strong>for</strong> <strong>Cisco</strong> switch ports connected to server NICs.<br />
Since a server NIC port typically only uses a single MAC address, <strong>the</strong> feature does not cause <strong>the</strong><br />
port to be shut down. However, if Port Security is enabled on <strong>the</strong> <strong>Cisco</strong> switch ports connected<br />
to VC uplinks and <strong>the</strong> administrator limits <strong>the</strong> number of MAC addresses to less than <strong>the</strong> number<br />
of MAC addresses being used by <strong>the</strong> servers in <strong>the</strong> BladeSystem enclosure, <strong>the</strong>n <strong>the</strong> port<br />
security feature can cause <strong>the</strong> <strong>Cisco</strong> switch ports to shut down. This causes <strong>the</strong><br />
BladeSystem enclosure to be isolated from <strong>the</strong> external network.