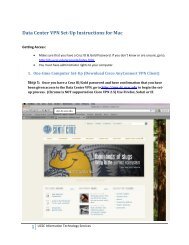
Technical requirements - Information Technology Services
Technical requirements - Information Technology Services
Technical requirements - Information Technology Services
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
scheduled as needed)<br />
6<br />
d<br />
6<br />
e<br />
SHAWN TO WORDSMITH<br />
Privileged Access (Application,<br />
Database, and System<br />
Administrators)<br />
1. Will adhere to service provider<br />
guidelines<br />
2. Will use secure access<br />
methods (SSH, VPN, or other<br />
approved method)<br />
3. Will include account and<br />
access information within<br />
quarterly report to data<br />
stewards (see 2e, above)<br />
LISA TO WORDSMITH remaining of<br />
6 with Eric Keisler<br />
Where Hosted Who supports the<br />
hosting What hosting functions are<br />
included<br />
Use Case: If System will be housed<br />
in the ITS Data Center or another<br />
ITSsupported facility, consider the<br />
following <br />
○ ITS Administrators will<br />
manage the systems<br />
(application, database,<br />
hardware and<br />
operating system)<br />
○ Includes monitoring of<br />
system health, and<br />
alert when<br />
performance targets<br />
degrade<br />
■ Confirm if<br />
nonITS<br />
service<br />
provider will<br />
receive alerts