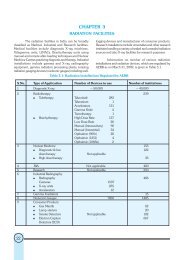
Security of Radioactive Sources in Radiation Facilities
Security of Radioactive Sources in Radiation Facilities
Security of Radioactive Sources in Radiation Facilities
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
(f)<br />
make sure that emergency response procedures are <strong>in</strong> place. In<br />
addition, identify the nearest medical facilities where personnel<br />
tra<strong>in</strong>ed and equipped to handle radiological emergencies are<br />
available.<br />
4.5.5 Availability <strong>of</strong> Emergency Response Plans<br />
Depend<strong>in</strong>g upon the magnitude and number <strong>of</strong> sources at a facility, specific<br />
emergency response procedures should be developed by the licencee. As a<br />
m<strong>in</strong>imum, these would normally <strong>in</strong>clude <strong>in</strong>form<strong>in</strong>g the local police and the<br />
Competent Authority <strong>in</strong> the event <strong>of</strong> a loss <strong>of</strong> the source and the <strong>in</strong>itial<br />
measures that would be made to recover lost or stolen sources. These<br />
emergency response procedures should be periodically exercised and<br />
evaluated.<br />
4.6 Additional Measures Required for <strong>Security</strong> Level A<br />
The performance objectives <strong>of</strong> security measures for <strong>Security</strong> Level A are to<br />
prevent unauthorised access and detect unauthorised access and acquisition<br />
<strong>of</strong> the source <strong>in</strong> a timely manner. These measures should be such as to delay<br />
acquisition until response is possible. Ideally, the access control to the source<br />
should <strong>in</strong>corporate at least two technical measures. However, it is recognised<br />
that dur<strong>in</strong>g normal use it may not be practicable to have all these measures <strong>in</strong><br />
place all the time. In any given situation, the quality <strong>of</strong> these security measures<br />
should be consistent with the DBT. Any unauthorised access to the source<br />
should be detected <strong>in</strong> a timely manner. The source should be accounted for<br />
on a daily basis.<br />
Depend<strong>in</strong>g on whether the radioactive source is <strong>in</strong> storage or <strong>in</strong> use, follow<strong>in</strong>g<br />
are the security measures that should be <strong>in</strong> place for <strong>Security</strong> Level A.<br />
4.6.1 Source <strong>in</strong> Storage<br />
To achieve the def<strong>in</strong>ed performance objective, the follow<strong>in</strong>g security<br />
provisions could be implemented:<br />
(a)<br />
(b)<br />
(c)<br />
(d)<br />
(e)<br />
A locked and fixed conta<strong>in</strong>er or a device hold<strong>in</strong>g the source<br />
A locked storage room, separat<strong>in</strong>g the conta<strong>in</strong>er from unauthorised<br />
personnel<br />
Access control to the storage room<br />
Detection <strong>of</strong> unauthorised access or removal <strong>of</strong> the source<br />
Ability to respond <strong>in</strong> a timely manner to such detection.<br />
For a mobile device conta<strong>in</strong><strong>in</strong>g a high activity source, the requirements could<br />
be:<br />
17