Security of Radioactive Sources in Radiation Facilities
Security of Radioactive Sources in Radiation Facilities
Security of Radioactive Sources in Radiation Facilities
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Security</strong><br />
Functions<br />
Detect<br />
Delay<br />
Response<br />
<strong>Security</strong><br />
management<br />
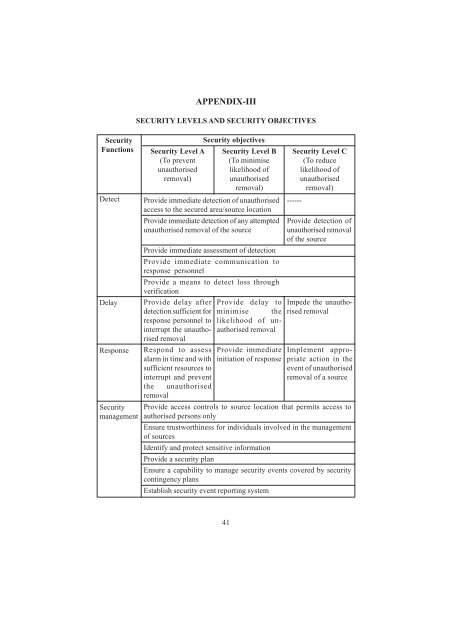
APPENDIX-III<br />
SECURITY LEVELS AND SECURITY OBJECTIVES<br />
<strong>Security</strong> Level A<br />
(To prevent<br />
unauthorised<br />
removal)<br />
<strong>Security</strong> objectives<br />
<strong>Security</strong> Level B<br />
(To m<strong>in</strong>imise<br />
likelihood <strong>of</strong><br />
unauthorised<br />
removal)<br />
Provide immediate detection <strong>of</strong> unauthorised<br />
access to the secured area/source location<br />
Provide immediate detection <strong>of</strong> any attempted<br />
unauthorised removal <strong>of</strong> the source<br />
Provide immediate assessment <strong>of</strong> detection<br />
Provide immediate communication to<br />
response personnel<br />
Provide a means to detect loss through<br />
verification<br />
Provide delay after Provide delay to<br />
detection sufficient for m<strong>in</strong>imise the<br />
response personnel to likelihood <strong>of</strong> unauthorised<br />
<strong>in</strong>terrupt the unauthorised<br />
removal<br />
removal<br />
Respond to assess<br />
alarm <strong>in</strong> time and with<br />
sufficient resources to<br />
<strong>in</strong>terrupt and prevent<br />
the unauthorised<br />
removal<br />
Provide immediate<br />
<strong>in</strong>itiation <strong>of</strong> response<br />
<strong>Security</strong> Level C<br />
(To reduce<br />
likelihood <strong>of</strong><br />
unauthorised<br />
removal)<br />
------<br />
Provide detection <strong>of</strong><br />
unauthorised removal<br />
<strong>of</strong> the source<br />
Impede the unauthorised<br />
removal<br />
Implement appropriate<br />
action <strong>in</strong> the<br />
event <strong>of</strong> unauthorised<br />
removal <strong>of</strong> a source<br />
Provide access controls to source location that permits access to<br />
authorised persons only<br />
Ensure trustworth<strong>in</strong>ess for <strong>in</strong>dividuals <strong>in</strong>volved <strong>in</strong> the management<br />
<strong>of</strong> sources<br />
Identify and protect sensitive <strong>in</strong>formation<br />
Provide a security plan<br />
Ensure a capability to manage security events covered by security<br />
cont<strong>in</strong>gency plans<br />
Establish security event report<strong>in</strong>g system<br />
41