Checklist and audit trail for compliance with Data Protection Act ...
Checklist and audit trail for compliance with Data Protection Act ...
Checklist and audit trail for compliance with Data Protection Act ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
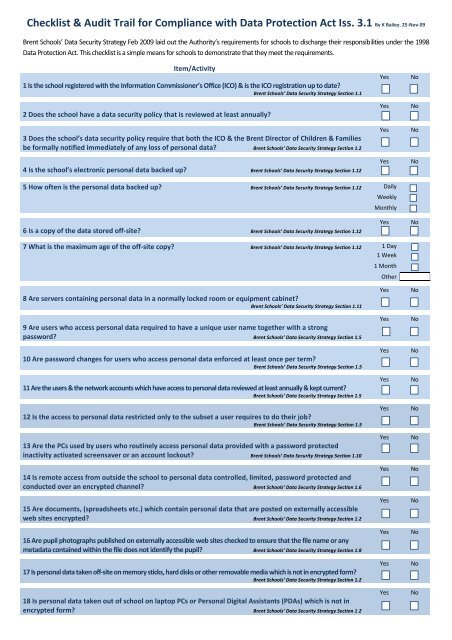
<strong>Checklist</strong> & Audit Trail <strong>for</strong> Compliance <strong>with</strong> <strong>Data</strong> <strong>Protection</strong> <strong>Act</strong> Iss. 3.1 By K Bailey, 25-Nov-09<br />
Brent Schools’ <strong>Data</strong> Security Strategy Feb 2009 laid out the Authority’s requirements <strong>for</strong> schools to discharge their responsibilities under the 1998<br />
<strong>Data</strong> <strong>Protection</strong> <strong>Act</strong>. This checklist is a simple means <strong>for</strong> schools to demonstrate that they meet the requirements.<br />
Item/<strong>Act</strong>ivity<br />
1 Is the school registered <strong>with</strong> the In<strong>for</strong>mation Commissioner’s Office (ICO) & is the ICO registration up to date?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.1<br />
2 Does the school have a data security policy that is reviewed at least annually?<br />
3 Does the school’s data security policy require that both the ICO & the Brent Director of Children & Families<br />
be <strong>for</strong>mally notified immediately of any loss of personal data? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.2<br />
4 Is the school’s electronic personal data backed up? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.12<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
No<br />
No<br />
No<br />
No<br />
5 How often is the personal data backed up? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.12 Daily<br />
Weekly<br />
Monthly<br />
6 Is a copy of the data stored off-site? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.12<br />
Yes<br />
No<br />
7 What is the maximum age of the off-site copy? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.12 1 Day<br />
1 Week<br />
1 Month<br />
Other<br />
8 Are servers containing personal data in a normally locked room or equipment cabinet?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.11<br />
9 Are users who access personal data required to have a unique user name together <strong>with</strong> a strong<br />
password? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.5<br />
10 Are password changes <strong>for</strong> users who access personal data en<strong>for</strong>ced at least once per term?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.5<br />
11Aretheusers &thenetworkaccounts which haveaccess topersonaldatareviewedatleast annually&keptcurrent?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.5<br />
12 Is the access to personal data restricted only to the subset a user requires to do their job?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.5<br />
13 Are the PCs used by users who routinely access personal data provided <strong>with</strong> a password protected<br />
inactivity activated screensaver or an account lockout? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.10<br />
14 Is remote access from outside the school to personal data controlled, limited, password protected <strong>and</strong><br />
conducted over an encrypted channel? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.6<br />
15 Are documents, (spreadsheets etc.) which contain personal data that are posted on externally accessible<br />
web sites encrypted? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.2<br />
16 Are pupil photographs published on externally accessible web sites checked to ensure that the file name or any<br />
metadata contained <strong>with</strong>in the file does not identify the pupil? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.8<br />
17 Is personal data taken off-site on memory sticks, hard disks or other removable media which is not in encrypted <strong>for</strong>m?<br />
Brent Schools’ <strong>Data</strong> Security Strategy Section 1.2<br />
18 Is personal data taken out of school on laptop PCs or Personal Digital Assistants (PDAs) which is not in<br />
encrypted <strong>for</strong>m? Brent Schools’ <strong>Data</strong> Security Strategy Section 1.2<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
Yes<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No<br />
No
<strong>Data</strong> <strong>Protection</strong> <strong>Act</strong> (DPA) 1998 Key Principles<br />
<strong>Data</strong> may only be used <strong>for</strong> the specific purposes <strong>for</strong> which it was collected.<br />
<strong>Data</strong> must not be disclosed to other parties <strong>with</strong>out the consent of the individual whom it is<br />
about, unless there is legislation or other overriding legitimate reason to share the<br />
in<strong>for</strong>mation (<strong>for</strong> example, the prevention or detection of crime). It is an offence <strong>for</strong> Other<br />
Parties to obtain this personal data <strong>with</strong>out authorisation.<br />
Individuals have a right of access to the in<strong>for</strong>mation held about them, subject to certain<br />
exceptions (<strong>for</strong> example, in<strong>for</strong>mation held <strong>for</strong> the prevention or detection of crime).<br />
Personal in<strong>for</strong>mation may be kept <strong>for</strong> no longer than is necessary.(Kept up to date)<br />
Personal in<strong>for</strong>mation may not be transmitted outside the European Economic Area unless the<br />
individual whom it is about has consented or adequate protection is in place, <strong>for</strong> example by<br />
the use of a prescribed <strong>for</strong>m of contract to govern the transmission of the data.<br />
Subject to some exceptions <strong>for</strong> organisations that only do very simple processing, <strong>and</strong> <strong>for</strong><br />
domestic use, all entities that process personal in<strong>for</strong>mation must register <strong>with</strong> the<br />
In<strong>for</strong>mation Commissioner's Office.<br />
Entities holding personal in<strong>for</strong>mation are required to have adequate security measures in<br />
place. Those include technical measures (such as firewalls) <strong>and</strong> organisational measures (such<br />
as staff training).<br />
Subjects have the right to have factually incorrect in<strong>for</strong>mation corrected (note: this does not<br />
extend to matters of opinion).<br />
Definitions<br />
Personal <strong>Data</strong> - Any data which can be used to identify a living person. This includes names,<br />
birthday <strong>and</strong> anniversary dates, addresses, telephone numbers, fax numbers, email addresses <strong>and</strong><br />
so on. It applies only to that data which is held, or intended to be held, on computers ('equipment<br />
operating automatically in response to instructions given <strong>for</strong> that purpose'), or held in a 'relevant<br />
filing system'. This includes paper filing systems.<br />
Strong Password – Password which is 8 characters minimum length, contains upper <strong>and</strong> lower<br />
case alphabetical characters <strong>and</strong> numbers or punctuation characters. It should not contain<br />
dictionary words, the owner’s date of birth or car registration number.<br />
Encryption – Process of trans<strong>for</strong>ming in<strong>for</strong>mation (referred to as plaintext) using an algorithm<br />
(called a cipher) to make it unreadable to anyone except those possessing special knowledge,<br />
usually referred to as a key.<br />
What Constitutes a Successful DPA Audit?<br />
Schools should have a data security policy that is relevant to the school <strong>and</strong> it should be<br />
reviewed regularly. If schools do not answer “yes” to all the questions posed in this<br />
checklist they are not fully compliant <strong>with</strong> Brent Schools’ <strong>Data</strong> Security Strategy.<br />
Issue 3.1 By K Bailey, 25-Nov-09