APPLICATION PENETRATION TEST SUPER VEDA
APPLICATION PENETRATION TEST SUPER VEDA
APPLICATION PENETRATION TEST SUPER VEDA
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
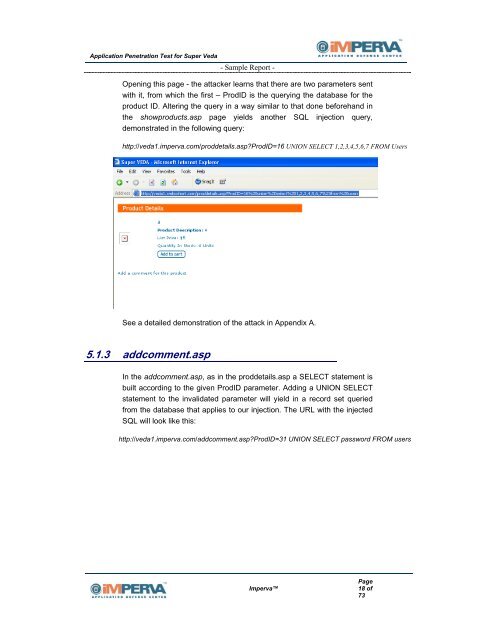
Application Penetration Test for Super Veda- Sample Report -Opening this page - the attacker learns that there are two parameters sentwith it, from which the first – ProdID is the querying the database for theproduct ID. Altering the query in a way similar to that done beforehand inthe showproducts.asp page yields another SQL injection query,demonstrated in the following query:http://veda1.imperva.com/proddetails.asp?ProdID=16 UNION SELECT 1,2,3,4,5,6,7 FROM UsersSee a detailed demonstration of the attack in Appendix A.5.1.3 addcomment.aspIn the addcomment.asp, as in the proddetails.asp a SELECT statement isbuilt according to the given ProdID parameter. Adding a UNION SELECTstatement to the invalidated parameter will yield in a record set queriedfrom the database that applies to our injection. The URL with the injectedSQL will look like this:http://veda1.imperva.com/addcomment.asp?ProdID=31 UNION SELECT password FROM usersImpervaPage18 of73