Security Protocols II: Syntax and Operational Semantics (Part 1)
Security Protocols II: Syntax and Operational Semantics (Part 1)
Security Protocols II: Syntax and Operational Semantics (Part 1)
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
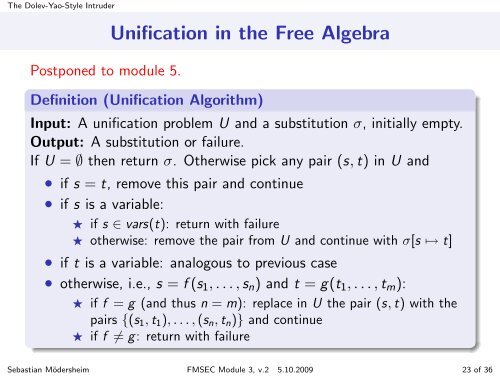
The Dolev-Yao-Style IntruderPostponed to module 5.Unification in the Free AlgebraDefinition (Unification Algorithm)Input: A unification problem U <strong>and</strong> a substitution σ, initially empty.Output: A substitution or failure.If U = ∅ then return σ. Otherwise pick any pair (s, t) in U <strong>and</strong>• if s = t, remove this pair <strong>and</strong> continue• if s is a variable:⋆ if s ∈ vars(t): return with failure⋆ otherwise: remove the pair from U <strong>and</strong> continue with σ[s ↦→ t]• if t is a variable: analogous to previous case• otherwise, i.e., s = f (s 1 , . . . , s n ) <strong>and</strong> t = g(t 1 , . . . , t m ):⋆ if f = g (<strong>and</strong> thus n = m): replace in U the pair (s, t) with thepairs {(s 1 , t 1 ), . . . , (s n , t n )} <strong>and</strong> continue⋆ if f ≠ g: return with failureSebastian Mödersheim FMSEC Module 3, v.2 5.10.2009 23 of 36