Security Protocols II: Syntax and Operational Semantics (Part 1)
Security Protocols II: Syntax and Operational Semantics (Part 1)
Security Protocols II: Syntax and Operational Semantics (Part 1)
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
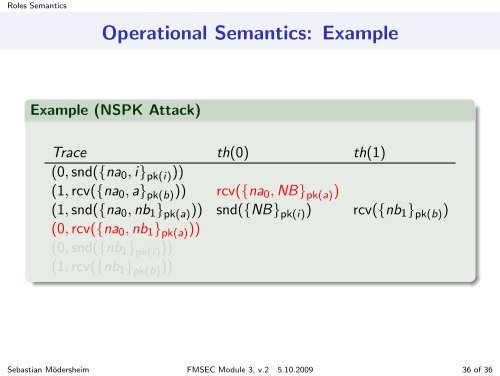
Roles <strong>Semantics</strong><strong>Operational</strong> <strong>Semantics</strong>: ExampleExample (NSPK Attack)Trace th(0) th(1)(0, snd({na 0 , i} pk(i) ))(1, rcv({na 0 , a} pk(b) )) rcv({na 0 , NB} pk(a) )(1, snd({na 0 , nb 1 } pk(a) )) snd({NB} pk(i) ) rcv({nb 1 } pk(b) )(0, rcv({na 0 , nb 1 } pk(a) ))(0, snd({nb 1 } pk(i) ))(1, rcv({nb 1 } pk(b) ))Sebastian Mödersheim FMSEC Module 3, v.2 5.10.2009 36 of 36