Confidential peer-to-peer file-sharing using social-network sites
Confidential peer-to-peer file-sharing using social-network sites
Confidential peer-to-peer file-sharing using social-network sites
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
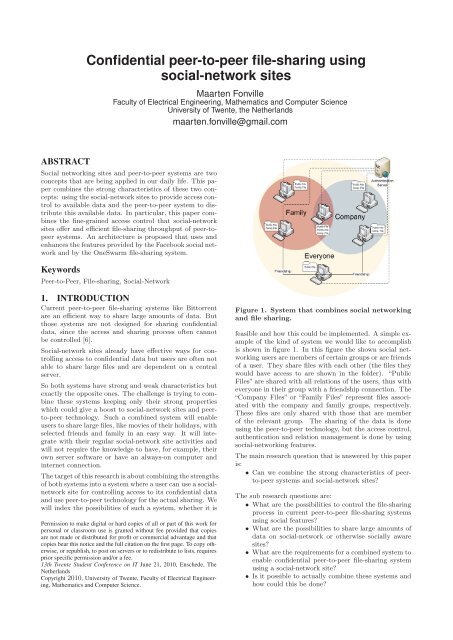
<strong>Confidential</strong> <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> <strong>using</strong><strong>social</strong>-<strong>network</strong> <strong>sites</strong>Maarten FonvilleFaculty of Electrical Engineering, Mathematics and Computer ScienceUniversity of Twente, the Netherlandsmaarten.fonville@gmail.comABSTRACTSocial <strong>network</strong>ing <strong>sites</strong> and <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> systems are twoconcepts that are being applied in our daily life. This papercombines the strong characteristics of these two concepts:<strong>using</strong> the <strong>social</strong>-<strong>network</strong> <strong>sites</strong> <strong>to</strong> provide access control<strong>to</strong> available data and the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system <strong>to</strong> distributethis available data. In particular, this paper combinesthe fine-grained access control that <strong>social</strong>-<strong>network</strong><strong>sites</strong> offer and efficient <strong>file</strong>-<strong>sharing</strong> throughput of <strong>peer</strong>-<strong>to</strong><strong>peer</strong>systems. An architecture is proposed that uses andenhances the features provided by the Facebook <strong>social</strong> <strong>network</strong>and by the OneSwarm <strong>file</strong>-<strong>sharing</strong> system.KeywordsPeer-<strong>to</strong>-Peer, File-<strong>sharing</strong>, Social-Network1. INTRODUCTIONCurrent <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> systems like Bit<strong>to</strong>rrentare an efficient way <strong>to</strong> share large amounts of data. Butthose systems are not designed for <strong>sharing</strong> confidentialdata, since the access and <strong>sharing</strong> process often cannotbe controlled [6].Social-<strong>network</strong> <strong>sites</strong> already have effective ways for controllingaccess <strong>to</strong> confidential data but users are often notable <strong>to</strong> share large <strong>file</strong>s and are dependent on a centralserver.So both systems have strong and weak characteristics butexactly the opposite ones. The challenge is trying <strong>to</strong> combinethese systems keeping only their strong propertieswhich could give a boost <strong>to</strong> <strong>social</strong>-<strong>network</strong> <strong>sites</strong> and <strong>peer</strong><strong>to</strong>-<strong>peer</strong>technology. Such a combined system will enableusers <strong>to</strong> share large <strong>file</strong>s, like movies of their holidays, withselected friends and family in an easy way. It will integratewith their regular <strong>social</strong>-<strong>network</strong> site activities andwill not require the knowledge <strong>to</strong> have, for example, theirownserversoftwareorhaveanalways-oncomputerandinternet connection.The target of this research is about combining the strengthsof both systems in<strong>to</strong> a system where a user can use a <strong>social</strong><strong>network</strong>site for controlling access <strong>to</strong> its confidential dataand use <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> technology for the actual <strong>sharing</strong>. Wewill index the possibilities of such a system, whether it isPermission <strong>to</strong> make digital or hard copies of all or part of this work forpersonal or classroom use is granted without fee provided that copiesare not made or distributed for profit or commercial advantage and thatcopies bear this notice and the full citation on the first page. To copy otherwise,or republish, <strong>to</strong> post on servers or <strong>to</strong> redistribute <strong>to</strong> lists, requiresprior specific permission and/or a fee.13th Twente Student Conference on IT June 21, 2010, Enschede, TheNetherlandsCopyright 2010, University of Twente, Faculty of Electrical Engineering,Mathematics and Computer Science.Figure 1. System that combines <strong>social</strong> <strong>network</strong>ingand <strong>file</strong> <strong>sharing</strong>.feasible and how this could be implemented. A simple exampleof the kind of system we would like <strong>to</strong> accomplishis shown in figure 1. In this figure the shown <strong>social</strong> <strong>network</strong>ingusers are members of certain groups or are friendsof a user. They share <strong>file</strong>s with each other (the <strong>file</strong>s theywould have access <strong>to</strong> are shown in the folder). “PublicFiles” are shared with all relations of the users, thus witheveryone in their group with a friendship connection. The“Company Files” or “Family Files” represent <strong>file</strong>s associatedwith the company and family groups, respectively.These <strong>file</strong>s are only shared with those that are memberof the relevant group. The <strong>sharing</strong> of the data is done<strong>using</strong> the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> technology, but the access control,authentication and relation management is done by <strong>using</strong><strong>social</strong>-<strong>network</strong>ing features.The main research question that is answered by this paperis:• Can we combine the strong characteristics of <strong>peer</strong><strong>to</strong>-<strong>peer</strong>systems and <strong>social</strong>-<strong>network</strong> <strong>sites</strong>?The sub research questions are:• What are the possibilities <strong>to</strong> control the <strong>file</strong>-<strong>sharing</strong>process in current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> systems<strong>using</strong> <strong>social</strong> features?• What are the possibilities <strong>to</strong> share large amounts ofdata on <strong>social</strong>-<strong>network</strong> or otherwise <strong>social</strong>ly aware<strong>sites</strong>?• What are the requirements for a combined system <strong>to</strong>enable confidential <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> system<strong>using</strong> a <strong>social</strong>-<strong>network</strong> site?• Is it possible <strong>to</strong> actually combine these systems andhow could this be done?
To index the possibilities of controlling the <strong>file</strong>-<strong>sharing</strong> processin current <strong>file</strong>-<strong>sharing</strong> systems and the <strong>sharing</strong> of largeamounts of data on <strong>social</strong>-<strong>network</strong> <strong>sites</strong>, we will do a combinedresearch study. A literature study is used <strong>to</strong> answerthe first three research questions. The fourth question isanswered by specifying and designing the desired architecture.This paper is organized as follows. In section two,the first sub question is answered, by studying current<strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> systems. Section three discussesdata-<strong>sharing</strong> on <strong>social</strong>-<strong>network</strong> <strong>sites</strong> and answers the researchquestion two. Section four lists the requirementsfor the desired combined system and answers the third researchquestion. The proposed architecture is describedin section five, where also the answer <strong>to</strong> the last researchquestion is provided. Section six concludes and providesrecommendations for future activities.2. SOCIAL-NETWORK FEATURES IN CUR-RENT PEER-TO-PEER FILE-SHARINGSYSTEMSVarious researchers try <strong>to</strong> improve current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong>systems. Challenges are often effective and efficient searching[38], reducing free-riding [14] and bootstrapping overlaysand managing those [21]. So some of our requirementshave already been studied in other papers or solved withincurrent <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> applications.2.1 Friends as <strong>peer</strong>sAt the moment there are several systems or studies thattry <strong>to</strong> embed a <strong>social</strong> layer within <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> systemssince there is a theoretical base that this can improve performance[13].MazeOne of those systems is Maze [7]. Maze builds an overlay intheir <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> <strong>network</strong> based on the interes<strong>to</strong>f the user. The software has algorithms <strong>to</strong> au<strong>to</strong>maticallyand dynamically detect these interests. With theseinterests it groups users <strong>to</strong>gether in<strong>to</strong> so-called ‘friend’groups. The identity of a friend is checked the first timeand confirmed via a central server (Ticket Grand Server)so that friends can be kept for a longer time, even if, forexample, their IP address does change. The idea is thatall the friends of a client also keep each other’s status, sothat if the central server goes down for some time, the <strong>network</strong>can still function because friends can give each otherconnection details of their friends and vouch for their identity.If a user wants <strong>to</strong> search for a certain <strong>file</strong>, it sends thesearch requests <strong>to</strong> its friends. Those friends answer <strong>to</strong> therequest with matching <strong>file</strong>s and give connection details oftheir own friends who also do have this <strong>file</strong>, <strong>to</strong> help thesearching party download from more sources, resulting ina faster download.Epidemic-Style management of Semantic OverlaysIn the Epidemic-Style Management of Semantic Overlays[34] study at the Vrije Universiteit Amsterdam a neighbourmechanism is proposed in which clients would becomeneighbours, based on a calculated proximity. If aclient would introduce a new <strong>file</strong> <strong>to</strong> the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>network</strong>,they would ‘gossip’ this <strong>to</strong> their neighbours, whowould gossip it <strong>to</strong> theirs until a certain distance. This gossipingconcept proved <strong>to</strong> be a very efficient way of findingthe needed <strong>file</strong>s and <strong>peer</strong>s. High hit ratios were achievedwhen the user wanted <strong>to</strong> request a <strong>file</strong> and his client alreadyhad heard of this <strong>file</strong> via the gossip, even when relativelysmall gossip broadcast distances are used.TRIBLERAnother system masking certain <strong>peer</strong>s as friends is TRI-BLER [28]. TRIBLER is based on Bit<strong>to</strong>rrent for the actual<strong>file</strong>-<strong>sharing</strong>, but adds another dimension with <strong>social</strong><strong>network</strong>ing<strong>to</strong> it. The clients are de-anonymized by a permanentidentity, which can be checked by a challenge andresponse system, and users rate their favorite <strong>file</strong>s. Basedon these favourite <strong>file</strong>s, users get so called ‘taste buddies’assigned with whom they form a group and they can explicitlyadd some of their real life friends. These groups,friends and a small number of random <strong>peer</strong>s, exchangewitheachotheronaregularintervalalis<strong>to</strong>fthese‘befriended’<strong>peer</strong>s and a list of their favourite <strong>file</strong>s. In thisway the <strong>network</strong> can keep updating itself with, for example,proper ‘taste buddy’ matches and suggestions <strong>to</strong> usersfor <strong>file</strong>s <strong>to</strong> download. Due <strong>to</strong> the fact that the systemcreates groups with non-anonymous <strong>peer</strong>s with which theuser shares interests, an altruistic behaviour is encouraged.This gives <strong>peer</strong>s an incentive <strong>to</strong> take part in collaborativedownloading, speeding up the download process for otherusers.OneSwarmAnother system <strong>using</strong> Bit<strong>to</strong>rent technology for <strong>file</strong>-<strong>sharing</strong>and <strong>using</strong> friendship between <strong>peer</strong>s is OneSwarm [19]. One-Swarm is completely backwards compatible with Bit<strong>to</strong>rrent,but gives the possibility for new features. A One-Swarm user creates an identity at a central ‘CommunityServer’ which manages a ‘swarm’. Since such an identity isnot exchanged between the community, servers of swarmsand community servers are not connected with each other,it is possible <strong>to</strong> have disjunct swarms. In the swarm theuser has a permanent identity which can be checked witha key system and keys can be exchanged via other systemslike Google Talk [16]. The identity has a list of friends thatare <strong>peer</strong>s trusted by the user. OneSwarm gives the possibility<strong>to</strong> connect, like the original Bit<strong>to</strong>rrent system, <strong>to</strong>any <strong>peer</strong>. But it also gives the user the choice <strong>to</strong> connec<strong>to</strong>nly <strong>to</strong> trusted <strong>peer</strong>s and ask, if necessary, these <strong>peer</strong>s <strong>to</strong>retrieve a download for the user. This enables the user<strong>to</strong> still download from <strong>peer</strong>s that are not his friends, andstill does not have <strong>to</strong> exchange data with untrusted <strong>peer</strong>s.OneSwarm has certain mechanisms build in which can obfuscatethe downloading and uploading via <strong>peer</strong>s and thefollowed route. This can be by adding, for example, randomintervals with the trusted download chain <strong>to</strong> preventtracking of the original source [27].A simple overview of the current authentication and <strong>file</strong><strong>sharing</strong>is shown in figure 2.2.2 Access control and authenticationPeer-<strong>to</strong>-<strong>peer</strong> systems were till now mostly developed withjust <strong>sharing</strong> <strong>file</strong>s as fast and efficiently as possible in mind.Connections would be between random <strong>peer</strong>s, often in amore or less anonymous way and not excluding any <strong>peer</strong>sat all, even if they were maybe not trustworthy. Some listslike Peerguardian [20] did exist, which were only created<strong>to</strong> prevent certain users from being tracked by corporationstrying <strong>to</strong> enforce copyright legislation. There was nofocus at all on <strong>using</strong> <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> systems for small private<strong>sharing</strong> in the form of <strong>sharing</strong> certain <strong>file</strong>s with onlya selected public.The by far most popular <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system at the momentis Bit<strong>to</strong>rrent [4], which has no form of access controlin the pro<strong>to</strong>col at all. But there do exist some Bit<strong>to</strong>rrentcommunities where trackers would only allow connectionsfrom users from a registered IP address. This is <strong>to</strong> createa small and exclusive community, which can enforce good
Figure 2. Simple representation of current authenticationand <strong>file</strong>-<strong>sharing</strong> in OneSwarm, taken from[19] and slightly modified.<strong>sharing</strong> ratio’s and eliminate free-riding [3]. This accesscontrol is an all-or-nothing approach. The user has access<strong>to</strong> all <strong>file</strong>s tracked or no access <strong>to</strong> any <strong>file</strong> at all. Alsothe implementation is not straightforward. Manual linkshave <strong>to</strong> be made between a service for logging in (a webserver for example) and the tracker service on the serverside. And meanwhile at the client side the user has <strong>to</strong> login with, for example, a browser on the web page beforebeing able <strong>to</strong> use his <strong>to</strong>rrent application <strong>to</strong> connect <strong>to</strong> thetracker.There also exists an advanced piece of middleware calledAuthenticatr [31]. Authenticatr can connect <strong>to</strong> <strong>social</strong><strong>network</strong><strong>sites</strong> <strong>to</strong> retrieve a list of friends and their <strong>network</strong>location. Next, it creates extra layers in the <strong>network</strong> whichare an overlay of a <strong>network</strong> of friends based on the definedrelationships in these <strong>social</strong>-<strong>network</strong>s. This enables anyapplication which runs on <strong>to</strong>p of this middleware <strong>to</strong> berestricted <strong>to</strong> communicating with friends only. Thus, if a<strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> application is developed that runs on <strong>to</strong>p ofthis, it can be restricted <strong>to</strong> only have access <strong>to</strong> a <strong>file</strong> in acertain layer.At the moment the only application that can share onlycertain <strong>file</strong>s with certain other users is OneSwarm. In thisapplication the user can select within the application itselfper <strong>file</strong> if it wants <strong>to</strong> share it unlimited or with a certaindefined set of users. But there is no possibility <strong>to</strong> userelationship rules or external data sets for applying this <strong>to</strong><strong>file</strong>s in a simple way. However, there is a current weaknessin the system as described in the OneSwarm paper [19].The visibility of <strong>file</strong>s is done by keeping a certain hashsecret. If an attacker can guess this hash, the <strong>file</strong>s will stillbe downloadable. The details of such a possible attack aredescribed very extensively in the paper of the OneSwarmdevelopers.3. CURRENT DATA SHARING WITH SO-CIAL CONTEXTMost internet users do want <strong>to</strong> interact with friends whileon-line, <strong>to</strong> exchange messages and pictures or <strong>to</strong> collaborate[22]. At the moment there are <strong>social</strong>-<strong>network</strong> <strong>sites</strong> <strong>to</strong>exchange these messages or <strong>to</strong> upload pho<strong>to</strong>s, which givegranular control over <strong>sharing</strong> these things with friends. Tocollaborate, people often have <strong>to</strong> share <strong>file</strong>s like documentswith each other, for this certain <strong>to</strong>ols and <strong>sites</strong> have beendeveloped. Both types of systems are considered. And wewill discuss which features they offer and which they lack<strong>to</strong> share <strong>file</strong>s within a <strong>social</strong> context.3.1 Social-<strong>network</strong> <strong>sites</strong>All <strong>social</strong>-<strong>network</strong> <strong>sites</strong> give their users the possibility <strong>to</strong>share text information, such as status updates or commentswith each other and often called ‘posts’, since thisis their core functionality [5]. These ‘posts’ can have, forexample, web links <strong>to</strong> information that can be found somewhereelse on the internet, like a YouTube video. In allmajor <strong>social</strong>-<strong>network</strong>s one cannot control per post whocan see and read theme. Often if one can define a groupof people who are allowed <strong>to</strong> see his or her posts, it willbe applied <strong>to</strong> all posts and not <strong>to</strong> a single one. If weblinks are posted, they are usually not hosted on the <strong>social</strong><strong>network</strong> itself. So there is in general no possibility <strong>to</strong> useany authentication means <strong>to</strong> detect whether such a weblink is actually opened by a party that is authorized <strong>to</strong> doso or not.Most major <strong>social</strong>-<strong>network</strong>ing <strong>sites</strong> like Facebook [11] andMySpace [24] also allow the <strong>sharing</strong> of pictures by its users.Those are uploaded <strong>to</strong> the central server of the <strong>social</strong><strong>network</strong>site and the user can often control in detail whichfriends are allowed <strong>to</strong> see which picture and which onesnot. Often a very effective interface is available for definingcertain groups and rules <strong>to</strong> simplify this process. Some<strong>social</strong>-<strong>network</strong> <strong>sites</strong> also allow this for videos, but no other<strong>file</strong> types are allowed.Up <strong>to</strong> date is Facebook in number of users by far thelargest <strong>social</strong>-<strong>network</strong> [37]. Part of its popularity is credited<strong>to</strong> the unique possibility of ‘Facebook Applications’[12]. Applications allow third party developers <strong>to</strong> interactwith Facebook, taking advantage of the authentication,relationship and access control management. Two FacebookApplications have been developed for data-<strong>sharing</strong>between users, like the ‘My Documents’ Facebook Application[1] and the ‘SMES<strong>to</strong>rage’ Facebook Application [2].Both applications run on a central server, which hosts theFacebook Application itself. The user actually uploadsthe <strong>file</strong> first <strong>to</strong> this central server and later other users candownload this <strong>file</strong> from the central server. Since a centralserver is used for the s<strong>to</strong>rage, there is often a <strong>file</strong> sizelimit enforced and the central server is the bottleneck inthe <strong>file</strong> distribution which can negatively influence performance.This makes that these kind of solutions can beused <strong>to</strong> easily share a data document, but their applicationon <strong>sharing</strong> a personal movie can be difficult. Also anapplication exists that integrates with the Azureus Bit<strong>to</strong>rrentClient [18]. The application has only a little amoun<strong>to</strong>f features. In short, it only shows a status on the user’sFacebook page whether its Azureus Client is on-line andwhich <strong>file</strong>s it is <strong>sharing</strong> at each moment.Other major <strong>social</strong>-<strong>network</strong> <strong>sites</strong>, such as LinkedIn or MySpaceand others as listed in [37], are not able <strong>to</strong> provide allthe features offered currently by Facebook. So there is nosupport for features where third-parties are offering somekind of data <strong>sharing</strong> features on those <strong>sites</strong>.The conclusion is that apparently there are no <strong>social</strong>-<strong>network</strong><strong>sites</strong> that offer currently proper integration with <strong>peer</strong>-<strong>to</strong><strong>peer</strong><strong>file</strong>-<strong>sharing</strong>. While, if they would offer such a service,
enabling users <strong>to</strong> combine the strengths of <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong>and <strong>social</strong>-<strong>network</strong> <strong>sites</strong> <strong>to</strong> share large <strong>file</strong>s with selectedfriends, an advantage for the users could be gained.3.2 Data-<strong>sharing</strong> with applications & web<strong>sites</strong>There do exist some applications and web<strong>sites</strong> that offerthe feature of <strong>sharing</strong> data. These services can be split upin web<strong>sites</strong> designed <strong>to</strong> handle uploads for <strong>sharing</strong> withother people and <strong>to</strong>ols <strong>to</strong> synchronise your own <strong>file</strong>s overmultiple computers.A very typical example of an uploading website is Rapid-Share [32]. These kind of web <strong>sites</strong> offer the user the possibility<strong>to</strong> upload, via an applet or directly via the browser,a single <strong>file</strong>. This single <strong>file</strong> is not allowed <strong>to</strong> be <strong>to</strong>o large,so that their server’s resources are not becoming <strong>to</strong>o restrained.Because they have a central-server approachwhere everything is s<strong>to</strong>red, it is difficult for them <strong>to</strong> handlehuge amounts of large <strong>file</strong>s, in hard disk space and inbandwidth. To further restrict the amount of downloadingand <strong>to</strong> prevent their servers from overloading, thereis a limit for every IP address on the data that can bedownloaded every day. Moreover, before the downloadweb link is shown <strong>to</strong> the user, a waiting delay of aroundtwo minutes is used. Their business model is <strong>to</strong> removethese restrictions for registered users who pay a certainamount of money every month. Enabling them <strong>to</strong> investin their servers and bandwidth with the funds these paidusers generate. After the user has uploaded a <strong>file</strong>, he orshe will get an unique link <strong>to</strong> the download page of this<strong>file</strong>. Theuserisincontrolofwhohegivesthislink<strong>to</strong>by, for example, e-mail or publicly posting it on an internetforum. The only security support that is offered isanonymity. As long as other users are not able <strong>to</strong> guessthis unique web link, they cannot download the <strong>file</strong>. Assoon as they have this web link, they have full access.A typical example of the synchronization <strong>to</strong>ol type <strong>sharing</strong>is Dropbox [9]. Dropbox enables the user <strong>to</strong> au<strong>to</strong>maticallysynchronize <strong>file</strong>s between his or her computers. Thisis done by installing their client on these computers andcreating an account with their service. If the user changesa <strong>file</strong> on one computer, the client moni<strong>to</strong>rs this changed<strong>file</strong> and uploads it <strong>to</strong> Dropbox server, <strong>to</strong> the user’s account.The other computers regularly poll the user’s accountat the Dropbox server <strong>to</strong> check for updated <strong>file</strong>s andif they find updated <strong>file</strong>s, they download these au<strong>to</strong>matically.The <strong>sharing</strong> can be done by setting extra Dropboxonlyattributes on a <strong>file</strong>. Within these attributes the usercan choose for <strong>sharing</strong> a <strong>file</strong> with another Dropbox user(of which they will manually have <strong>to</strong> enter the accountname) or can even share <strong>file</strong>s publicly. If the user doeschoose for the publicly accessible link, a RapidShare-likeservice can be created by a unique link that points <strong>to</strong> theshared <strong>file</strong>. When the user does choose the possibility for<strong>sharing</strong> only with another user, then this other user willsee this <strong>file</strong> in a special folder. Such special folders are alsoshown for all other users <strong>sharing</strong> <strong>file</strong>s with the user. Dropboxhas the same capacity issues as RapidShare, becausethey also use a fully central server approach. Normally,the amount of data that can be s<strong>to</strong>red by an account islimited. Moreover, paid upgrades are offered.Clearly both systems have weak points in their centralserver based approach. And especially the upload <strong>sites</strong> donot give any control over the access <strong>to</strong> the <strong>file</strong>s. The currentsystems cannot fulfill the requirements we are lookingfor.4. REQUIREMENTSThis section describes requirements that have <strong>to</strong> be supportedby the desired combined solution.4.1 Integration with current systemsOur first demand will be that the new proposed architecturewill be simple and straightforward <strong>to</strong> use, easy <strong>to</strong>implement and integrate with current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> solutionsand current <strong>social</strong>-<strong>network</strong> <strong>sites</strong>. It is important <strong>to</strong>emphasize that we don’t want <strong>to</strong> create another <strong>social</strong><strong>network</strong>site, but we want users <strong>to</strong> be able <strong>to</strong> use theircurrent <strong>social</strong>-<strong>network</strong>s. Sharing of <strong>file</strong>s and other datainformation must be as easy as <strong>sharing</strong>, for example, pictureswith the <strong>social</strong>-<strong>network</strong> site.For the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> downloading we should try <strong>to</strong> incorporatecurrent <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> technology, so that currentclients can be adopted <strong>to</strong> our new architecture with smallchanges, and that new advancements in <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> caneasily be integrated in our proposed architecture.4.2 Detailed control of <strong>sharing</strong>The new architecture should implement one of the mainfeatures most <strong>social</strong>-<strong>network</strong> <strong>sites</strong> offer: controlling whatis shared with whom [5]. Most <strong>social</strong>-<strong>network</strong> <strong>sites</strong> offerthis feature, for example, when uploading pictures. Theuser can control in detail who is allowed <strong>to</strong> view them.The new architecture should incorporate this in the samemanner for <strong>sharing</strong> <strong>file</strong>s, with logical rules differentiatingrelations as a (1) single friend, (2) all friends, (3) friend offriends, (4) certain <strong>network</strong>s or simply (5) everyone [36].4.3 Trusted <strong>sharing</strong>The new architecture shall use the identity of the users inthe process of access control, instead of <strong>using</strong> the concep<strong>to</strong>f anonymous <strong>peer</strong>s. We actually want that our proposedarchitecture uses the relations between users <strong>to</strong> improvethe operation of <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system. We want that ourusers should be able <strong>to</strong> use only trusted connections withothers users, knowing who their <strong>peer</strong>s are and having themauthenticated by e.g., a chain of trust [23]. By puttingusers in the context of their <strong>social</strong> group we are willing <strong>to</strong>reduce free-riding and encourage altruistic behaviour [28].This should be able <strong>to</strong> reduce the amount of malware andfake <strong>file</strong>s on the <strong>network</strong> [33].Thus the proposed system must be able <strong>to</strong> authenticateusers and support a chain of trust.4.4 Proper scalingThe new architecture must not have major regressions incomparison with current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>network</strong>s. The <strong>network</strong>should scale at least as well as current systems. Thatmeans as well with non-popular (e.g. scarcity of <strong>peer</strong>s), aspopular (e.g. overloaded trackers [33]) <strong>file</strong>s.The system must be able <strong>to</strong> deliver the <strong>file</strong>s <strong>to</strong> the userswho wish <strong>to</strong> download them and must support an acceptabledownload speed.5. PROPOSED ARCHITECTUREThis section describes the architecture that should be designedin such a way that the requirements specified inthe previous section are satisfied. The proposed architectureis combining that capabilities and features providedby selected <strong>social</strong> <strong>network</strong> <strong>sites</strong> and the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong><strong>sharing</strong> systems.5.1 Chosen current technologies
Figure 4. A Simple overview of the Facebook Applicationarchitecture. Taken from [30]Figure 3. The current privacy and access controlas offered by Facebook for pictures.To meet the requirements presented in the previous sectionit is important <strong>to</strong> select one <strong>social</strong> <strong>network</strong> system andone <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>sharing</strong> system described in section three.When analysing the integration with a <strong>social</strong>-<strong>network</strong>, Facebookseems <strong>to</strong> be by far the best choice. The amoun<strong>to</strong>f registered users is a couple of times larger then anyrunner-up with more than 400,000 [10] . Moreover, Facebookis one of the few <strong>social</strong>-<strong>network</strong>s that provides anAPI (Application Programming Interface) that gives thepossibility <strong>to</strong> deeply integrate with the user-interface of<strong>social</strong>-<strong>network</strong> website. Also a very convenient aspect isthat 70% of the current Facebook users is already <strong>using</strong>third-party ‘Facebook Applications’ and will probably notbe finding any trouble with adding, authorizing and <strong>using</strong>a new Facebook Application [10].Facebook also offers fine-grained settings for access control.Thus detailed control of <strong>sharing</strong> is possible with re<strong>using</strong>their interface of which an example is given in figure3. Facebook also offers so called ‘Facebook Networks’and ‘Friend Lists’ features. Both features allow users <strong>to</strong>associate certain friends and relationships with a group.Facebook users can become members of a ‘Facebook Network’if they have an approved e-mail address of a certaindomain that is associated with a ‘Facebook Network’. Anexample is that only people with @(*.)utwente.nl e-mailaddresses are eligible <strong>to</strong> become member of the ‘Universityof Twente’ ‘Facebook Network’. The ‘Friend Lists’ are definedby Facebook users themselves, an example would beadding all colleagues from work <strong>to</strong> one list. A friend canbe member of multiple <strong>network</strong>s, multiple lists or none atall.Implementing a Facebook Application will demand a centralserver (or servers, the load can be balanced of course)running a web server <strong>to</strong> serve the users of the applicationthe web pages for the application and a database <strong>to</strong>keep necessary information s<strong>to</strong>red. Also a scripting languagewill have <strong>to</strong> be used on the web pages <strong>to</strong> be able<strong>to</strong> communicate with Facebook. There is a wide choice oflanguages that can be chosen from for this [12]. A simpleoverview of how a Facebook Application does communicatewith Facebook itself and the user is shown in 4.From the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> pro<strong>to</strong>cols, Bit<strong>to</strong>rrent, with the One-Swarm extensions added, is the preferred choice. Bit<strong>to</strong>rrenthas proven <strong>to</strong> be a very good and efficient way fordistributing <strong>file</strong>s. OneSwarm uses and enhances Bit<strong>to</strong>rrentwith security and access control features.Since OneSwarm is based on the Azureus Bit<strong>to</strong>rrent Client,which is written in Java, OneSwarm is available for everymajor platform and can also be distributed as applets infor example a browser, giving it a lot of flexibility for theusers as a client. Also the interface of OneSwarm is at themoment already web based, making the integration withother web based services easier.5.2 ArchitectureNow we will describe the overview and functionality of ourproposed architecture for <strong>sharing</strong> data with <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong>on <strong>social</strong>-<strong>network</strong> <strong>sites</strong> based on OneSwarm and Facebook.5.2.1 OverviewWe will approach the <strong>social</strong>-<strong>network</strong> within OneSwarmas one ‘Community Server’, whose role with the One-Swarm process was described in section two. The FacebookApplication server will be connected <strong>to</strong> the One-Swarm server populating the relationship data with theinformation from Facebook. This will be done througha database where the information is s<strong>to</strong>red. At the momentOneSwarm has already support for defining groups.When integrating with Facebook, we will make the Facebook‘Networks’ and the Facebook ‘Friend Lists’ groupswithin OneSwarm.OneSwarm offers the choice between several back ends forits database. A new back end has <strong>to</strong> be written that willimplement a kind of middleware that will s<strong>to</strong>re part of thedata in an own database and can communicate with Facebookin, for example, FQL (Facebook Query Language)<strong>to</strong> retrieve relationship information.Figure 5. A basic overview of the proposed architecture.The user can start the OneSwarm client easily with for exampleJava Web Start [25]. This would give the user thepossibility <strong>to</strong> choose between starting the client au<strong>to</strong>maticallyduring boot if preferred, or <strong>to</strong> let it be started au<strong>to</strong>maticallywhen opening the Facebook Application pagein the web browser. The client will run in the background
Figure 6. An example of suggestions the FacebookApplication could give on the Facebook homepage.<strong>to</strong> perform the actual <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>sharing</strong>. This way the<strong>sharing</strong> can be active even when not having the FacebookApplication web page itself opened, making the availabilityof <strong>peer</strong>s higher.The user can easily control the client via the FacebookApplication page in the web browser, see figure 5. Thiscan be done in a similar way as in Facebook. A user logsin on Facebook and opens the Facebook Application page.The user receives a web interface build up by this FacebookApplication and its own local client. The FacebookApplication s<strong>to</strong>res relevant information for the CommunityServer or itself in a database. The Community Serverdoes communicate and authenticates the clients that theruns on the local computer of the users and retrieves necessary(relationship) information from the database. Sointegration in the Facebook website can be achieved properlyand deliver a consistent interface with the rest of thewebsite. This enables users <strong>to</strong> easily adopt the applicationas any other feature they are used <strong>to</strong> on Facebook.The client will have the ability <strong>to</strong> share <strong>file</strong>s with otherusers. The process of <strong>file</strong> <strong>sharing</strong> is accomplished <strong>using</strong>the OneSwarm <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system. This process can beset up in the background. The client can see their own(completed) downloads. They can check which <strong>file</strong>s theirfriends share and provide web links <strong>to</strong> download these inthe background on the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system. The systemmay suggest even some popular downloads. An exampleof how this could look like is given in figure 6.The proposed architecture will combine the architecturesand features provided by the OneSwarm and Facebooksystems. The supported features are: (1) Access controland authentication, (2) Creating and Uploading, (3)Searching, (4) Downloading. In particular, the “Accesscontrol and authentication” and “Creating and Uploading”,features are enhanced versions of the similar featuresdeveloped by Facebook. The proposed architecture usesenhanced versions of the following features developed byOneSwarm: “Searching” and “Downloading”.The pro<strong>to</strong>col used by the OneSwarm <strong>to</strong> communicate itsCommunity Server has <strong>to</strong> be enhanced in order <strong>to</strong> supportthe advanced Facebook Application features that will bedescribed in the following subsections. This should berelatively easy since the OneSwarm pro<strong>to</strong>col is specified<strong>using</strong> XML (Extensible Markup Language).We should also extend the security of the <strong>file</strong>-<strong>sharing</strong>, sincean attacker could guess a specific hash that is used for<strong>sharing</strong> <strong>file</strong>s with a private group. It is described as weaknessin the current OneSwarm system by the developersthemselves. We propose generating a private and publicencryption key combination for shared <strong>file</strong>s <strong>to</strong> tackle thisFigure 7. Enhancement of the encryption mechanism.problem. This would be the most straightforward, sincewe have <strong>to</strong> restrict access <strong>to</strong> unique sets of <strong>file</strong>s.Since the access restrictions can vary for each set of <strong>file</strong>s,thekeyshave<strong>to</strong>begeneratedforeachset. Anexchangeofthe necessary keys <strong>to</strong> decrypt <strong>to</strong> authorized parties wouldenable those <strong>to</strong> actually decrypt the <strong>file</strong>s. A technologylike PGP (Pretty Good Privacy) [15] which can be used <strong>to</strong>encrypt and decrypt <strong>file</strong>s can be used. Other asymmetricencryption technologies, generating a public and privatekey pair, can also be used. A key will be generated perset of <strong>file</strong>s and the decryption key will be uploaded <strong>to</strong>the Community Server. The Community Server can thenprovide the decryption key only <strong>to</strong> the authorized clients(since those are authenticated and identified by the CommunityServer) according <strong>to</strong> the <strong>sharing</strong> rule-set as definedfor the <strong>file</strong>. This way physically being able <strong>to</strong> downloadthe data after successfully guessing the hash will still disablethe use of this data. The chosen technology for thekey pair does not influence the Community Server sinceit only has <strong>to</strong> s<strong>to</strong>re the key itself, which is small and normallyin text form. The encryption technology can bechosen by the clients itself, as long as the other client withwhom they exchange the <strong>file</strong>s also supports this technologyand the chosen encryption technology is known bythe decrypting client. An overview of the extension forthe earlier overview is given in figure 7. The user’s clientencrypts the <strong>file</strong>s and sends encrypted data via the <strong>peer</strong>-<strong>to</strong><strong>peer</strong>system. A key is uploaded <strong>to</strong> the Community Serverwhich s<strong>to</strong>res this key in the database. The key can bedownloaded by clients that are authorized <strong>to</strong> do so.5.2.2 Access control and AuthenticationThe main operation of this feature is the same as the onespecified and used by the Facebook system. This subsectiondiscusses the main enhancements on Facebook fromthe point of view of access control and authentication.The first time the user wants <strong>to</strong> utilize the <strong>file</strong>-<strong>sharing</strong> featureit will have <strong>to</strong> add the Facebook Application <strong>to</strong> itsFacebook pro<strong>file</strong>, see figure 8. This is an easy step thatmost Facebook users are used <strong>to</strong> do. Users can invite theirfriends <strong>to</strong> also add the Facebook Application, giving the
Figure 9. An example of a download request.Figure 8. A simple overview of the access controland authentication process.application the possibility <strong>to</strong> increase its user base quickly.After the Facebook Application has been added, the userwill receive the installation for the OneSwarm Java client.The client is written in Java and can be installed as, forexample, a Java Web Start Application. If the user subsequentlylogs in at the same web page, the web page shouldcheck for the client application, start it if necessary and,if it is not installed, offer installation of the client again.When the client is started for the first time by the user,the client will generate an asymmetric encryption key pairused for OneSwarm authentication. The key is published<strong>to</strong> the server, by our extended OneSwarm pro<strong>to</strong>col, whichwill s<strong>to</strong>re it in the database with a reference <strong>to</strong> the FacebookAccount. This database can be accessed later bythe Community Server <strong>to</strong> identify the user when <strong>using</strong> theapplication. A user can have multiple clients installed, allwith different keys. This capability is useful when the useris <strong>using</strong>, for example, more than one machine. All of thosekeys are connected <strong>to</strong> the user’s Facebook identity and areavailable as <strong>peer</strong>s in the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> process.When trying <strong>to</strong> download a <strong>file</strong> the client retrieves a list of<strong>peer</strong>s from the Community Server, containing users withwhom they have a relationship on Facebook, with theirthen on-line clients and authentication keys. For large‘Facebook Networks’ a choice could be <strong>to</strong> only return asubset of users instead of all.5.2.3 SearchingThe main operation of this feature is the same as the onespecified and used by the OneSwarm system. This subsectiondiscusses the main enhancements on OneSwarm fromthe point of view of searching information.OneSwarm itself allows searching on the <strong>network</strong> by meansof ‘flooding’. The search query is performed on neighbouring<strong>peer</strong>s, who will further continue the search request.Thus, searching can be done <strong>using</strong> the OneSwarm pro<strong>to</strong>colused for searching. Of course the interface for thesearching feature needs <strong>to</strong> be be presented via the FacebookApplication web page itself. This interface can bedesigned in the same way as the design of a default Face-book search feature.Because most users are not interested in selecting randomlyfrom available <strong>file</strong>s, but often interested in <strong>file</strong>s theyself noticed of via their friends that have shared interestsor having a common relationship <strong>to</strong> the <strong>file</strong> (like a vacationvideo where the user also <strong>to</strong>ok part in). With this wepropose a feature that might reduce the amount of searchingneeded. We can analyze the <strong>file</strong>s users are <strong>sharing</strong>and measure their popularity. These suggestions for theuser can be adjusted <strong>to</strong> the popularity of the user’s friendswithin the <strong>social</strong> <strong>network</strong>. Every user can get its own optimizedset of what is considered popular and of courseonly ‘popular’ things are shown for <strong>file</strong>s that are actuallyallowed <strong>to</strong> be discovered and downloaded by the user.A Facebook user has a so called Facebook ‘Wall’. This isa user’s own web page on Facebook where a user him orherself or a friend can post short text messages, pictures,web links and links <strong>to</strong> other Facebook pages. Other userscan respond <strong>to</strong> these posts with comments. Our FacebookApplication should offer the possibility <strong>to</strong> explicitly postabout <strong>file</strong>s. In this way a user can update their friendsabout <strong>file</strong>s they consider relevant, just like they can do atthe moment for, for example, pictures. Their friends dosee an aggregation of their friends’ posts in their Facebook‘News’ feed. This ‘News’ feed is a Facebook feature thatau<strong>to</strong>matically highlights the more interesting posts of auser’s friends.Users can invite their friends <strong>to</strong> download a certain <strong>file</strong>via the Facebook ‘Requests’ system. This is a direct privatemessage between Facebook users in which a link canbe embedded. Such a link is able <strong>to</strong> let the user takean action within Facebook Application directly. A ‘FacebookRequest’ our application could offer is, for example,‘Download this <strong>file</strong> now’. In this way one user sends a linksuggesting <strong>to</strong> download a <strong>file</strong> directly <strong>to</strong> one of its friends.If this friend does click the link, the downloading wouldstart directly within the Facebook Application. An exampleof how this feature could look like is given in figure9.5.2.4 Creating & UploadingThe main operation of this feature is the same as the onespecified and used by the Facebook system. This subsectiondiscusses the main enhancements on Facebook fromthe point of view of creating and uploading information.When the user opens the Facebook Application web page,it will see the web interface of the client embedded in theweb page of the Facebook Application itself, see figure
10. On this web page there is the possibility <strong>to</strong> ‘upload’new <strong>file</strong>s. Note that actually the new <strong>file</strong> is not uploadedbut it is shared, since no physical upload <strong>to</strong> the centralserver takes place. Files can be selected via a dialog <strong>to</strong> beshared. When <strong>file</strong>s have been selected, the client generatesan asymmetrical encryption key that will be used for thesecure <strong>sharing</strong>. Next step for the user will be selectingwith whom the <strong>file</strong>s have <strong>to</strong> be shared. For this a defaultFacebook <strong>sharing</strong> control interface can be used. After theselection of these <strong>sharing</strong> rules they will be saved on theserver and retrieved by the local client. One part of theencryption key will be uploaded <strong>to</strong> the Community Server,for decryption by authorized clients later on, and the metadataof the <strong>file</strong>s, for indexing by the server <strong>to</strong> be used in,for example, measuring the popularity of a <strong>file</strong>. A simpleoverview of this encryption process is displayed in figure10.Figure 10. A simple overview of the creating &uploading process.5.2.5 DownloadingThe main operation of this feature is the same as the onespecified and used by the OneSwarm system. This subsectiondiscusses the main enhancements on OneSwarm fromthe point of view of downloading information.When user has found a <strong>file</strong> via the one of the methodsas described in the “Searching” section, the actual downloadingbegins. For this <strong>to</strong> happen, the user clicks a linkthat is actually presented by the client application andalso handled by the client. The client will start the download.The user will see a web page with an overview ofhis downloads and can see the progress as presented by itsclient. An example of this is given in figure 11.The downloading is done with the standard OneSwarmpro<strong>to</strong>col which is based on Bit<strong>to</strong>rrent [8]. In the One-Swarm pro<strong>to</strong>col, the client first downloads the metadata inwhich it can find a list of block hashes needed <strong>to</strong> downloadthe actual blocks of data. In the Bit<strong>to</strong>rrent pro<strong>to</strong>col thismetadata is normally s<strong>to</strong>red in ‘.<strong>to</strong>rrent’ <strong>file</strong>s, but thoseare not used in the OneSwarm pro<strong>to</strong>col. More detailedinformation about differences between the OneSwarm andBit<strong>to</strong>rrent pro<strong>to</strong>col can be found in the OneSwarm paper[19].Next, instead of contacting the other <strong>peer</strong>s via a directconnection, as is in the Bit<strong>to</strong>rrent pro<strong>to</strong>col, OneSwarmtunnels the traffic through overlay paths created over thetrusted links [19]. Such an overlay path is interpreted as a<strong>peer</strong> within the Bit<strong>to</strong>rrent implementation that the One-Swarm client is based on. So different paths can actuallyconnect <strong>to</strong> the same endpoint, but are considered separate<strong>peer</strong>s within the application. An overview of this isgiven in figure 12. All clients are authenticated with theOneSwarm Community Server, which enables them <strong>to</strong> authorizeconnections with friends. The user is trying <strong>to</strong>download a <strong>file</strong> that Friend C is also trying <strong>to</strong> download.Since they are friends they can also exchange <strong>file</strong>-parts betweeneach other. The user is also friend with Friend Aand Friend B, which are both friends with a client that isnot a friend of the user. Still the user can download the<strong>file</strong> with a path over Friend A and B. Both are in fact locatedat the same endpoint, but the user’s client does notknowthat.FriendCisalsoafriendwithFriendBandisalso <strong>using</strong> the path over Friend B <strong>to</strong> download the <strong>file</strong>.Since the downloading is done with (an extended) Bit<strong>to</strong>rrentpro<strong>to</strong>col, it shares its features with it. So are the<strong>file</strong>s split in blocks. The blocks are hashed, and blocks aredownloaded from different <strong>peer</strong>s. Advanced tricks of theoriginal client (Azureus) of OneSwarm allow the detectionof congestion, which proves <strong>to</strong> be a very effective systemfor avoiding the congestion of single paths and shifting <strong>to</strong>alternative paths when needed. Also <strong>peer</strong> <strong>sharing</strong> incentivepolicies implemented by the Bit<strong>to</strong>rrent pro<strong>to</strong>col like‘tit-for-tat’ [8] are used. ‘Tit-for-tat’ is a mechanism thatmotivates a <strong>peer</strong> <strong>to</strong> upload <strong>to</strong> <strong>peer</strong>s that also upload <strong>to</strong>itself. This gives <strong>peer</strong>s an incentive <strong>to</strong> upload as muchas possible <strong>to</strong> increase their own download speed. Thisshould reduce the so-called ‘free-riding’ of clients, whichdo not upload and only download. The ‘tit-for-tat’ <strong>sharing</strong>mechanism is even more effective in OneSwarm than inthe usual Bit<strong>to</strong>rrent pro<strong>to</strong>col, because within OneSwarmthe <strong>peer</strong>’s identity is persistent, as where in Bit<strong>to</strong>rrent it isused for only one session, and previous and future downloadsdo also count in the <strong>sharing</strong> <strong>file</strong> ratio.After the downloading of the <strong>file</strong>, the client should checkwith the Community Server for a public encryption key <strong>to</strong>decrypt the <strong>file</strong>. If the user is actually authorized <strong>to</strong> seethe <strong>file</strong>, the server does hand the key over <strong>to</strong> the client,enabling the user <strong>to</strong> use the contents of the <strong>file</strong>.5.3 DiscussionOur proposed architecture is based on the earlier definedrequirements. Full integration with current systems wouldbe achieved. The proposed user interface that integrateswith Facebook appears as any other typical Facebook Application<strong>to</strong> the user. Room for improvement would bethat <strong>social</strong>-<strong>network</strong> <strong>sites</strong> like Facebook, but also otherFigure 11. An example of the download overviewweb page.
Figure 12. An overview of a user’s client downloadingvia <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> (P2P).<strong>sites</strong>, would embed the installation of the new FacebookApplication via the existing <strong>social</strong> <strong>network</strong>ing web <strong>sites</strong>.This would remove the step for users having <strong>to</strong> add andauthorize the proposed new Facebook Application. Alsothe <strong>social</strong>-<strong>network</strong> <strong>sites</strong> that do not offer support for anythird-party applications, which are all with the exceptionof Facebook, could offer this <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> service.The proposed client integrates with current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong>technology based on OneSwarm & Bit<strong>to</strong>rrent. A vastamount of Bit<strong>to</strong>rrent clients could easily be extended justlike OneSwarm <strong>to</strong> work with our architecture. A nice featurewould be that the download services of the clientwould already be offered by, for example, the browser oroperating system. In that case the website only has <strong>to</strong>interact with this client service and does not have <strong>to</strong> bebothered with checking if the client software is running onthe user’s computer. Such a service for a browser couldprobably be compared with the newer geo-location featuresin HTML5 [35], where the browser is able <strong>to</strong> gatherdata from a local service [17] or application and hand i<strong>to</strong>ver <strong>to</strong> the website.The proposed architecture gives fine-grained control <strong>to</strong> theuser about who is able <strong>to</strong> access which <strong>file</strong>s. The currentweakness in the system is the attack as was described bythe developers of OneSwarm. The current solution thatencrypts the <strong>file</strong> with a private key and handing the publickey over <strong>to</strong> authorized downloading parties does takecare of this problem, but might introduce a dependencyon requiring complexity and capabilities. A better solutionwould be <strong>to</strong> take care of this weakness somehow inthe <strong>sharing</strong> system itself.The proposed architecture gives the user the possibility <strong>to</strong>only use trusted web links. The proposed client of the userwill only exchange data directly with known and trusted<strong>peer</strong>s, but still it has the possibility <strong>to</strong> access <strong>file</strong>s that areshared by <strong>peer</strong>s they do not trust themselves but have achain of trust with. Since actual <strong>sharing</strong> always appears<strong>to</strong> be with direct friends within the <strong>social</strong>-<strong>network</strong>, freeridingcan probably be reduced <strong>to</strong> a minimum since usersare aware of their <strong>social</strong> group.The proposed architecture would scale quite well. According<strong>to</strong> the research done in TRIBLER [28] by crawling a<strong>social</strong>-<strong>network</strong> site, users of <strong>social</strong>-<strong>network</strong> <strong>sites</strong> have onaverage around 250 friends and 9.000 friends-of-friends.Facebook has next <strong>to</strong> other <strong>social</strong>-<strong>network</strong> <strong>sites</strong> also the‘Networks’ feature that people are often a member of.Which means that an average user has a lot of trusted<strong>peer</strong>s <strong>to</strong> connect <strong>to</strong>, and via these <strong>peer</strong>s a lot of different<strong>peer</strong>s can be reached <strong>to</strong>o. The crea<strong>to</strong>rs of OneSwarmdid crawl last.fm [19], which a <strong>social</strong>-<strong>network</strong> site focusedon music by aggregating all songs played by their users.Last.fm is a much less dense <strong>network</strong> than Facebook, buteven there the researchers did find out that most usersare connected within seven steps from other users andreal disjunct groups are almost non existent. Thus Facebook,with a much higher amount of users, maintainedrelationships and the existence of ‘Networks’, will give theusersalwaysapossibilityofapath<strong>to</strong>thedatatheywant.Also it is considered that at least some interests are sharedwith friends which greatly increases the probabilities thatfriends already have the requested <strong>file</strong>s. In [13] they wereable <strong>to</strong> achieve 65% hits by just optimizing the overlay of<strong>peer</strong>s. The scaling on the central server for the FacebookApplication and Community server will also do fine. Thereare at the moment already some very popular FacebookApplications with millions of users, and those are scalableeven while running sometimes heavy applications. Our applicationwon’t be that heavy since a lot of the web pageswill be rendered by Facebook itself and the local client.And within the <strong>file</strong>-<strong>sharing</strong> process and PGP key distributionthe server is sending only little amounts of (control)data. The scaling of the <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> process is, according<strong>to</strong> the OneSwarm study over the trusted paths, also quiteeffective. It might not be as effective as not <strong>using</strong> paths,but could outperform [19] Bit<strong>to</strong>rrent on an anonymizer<strong>network</strong>, which uses a random set of <strong>peer</strong>s as proxy <strong>to</strong>anonymize connections <strong>to</strong> end-points, like Tor [29].6. CONCLUSIONS & FUTURE WORKTo conclude our research we will look back at our subquestions. We did find out that possibilities <strong>to</strong> control the<strong>file</strong>-<strong>sharing</strong> in current <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> applications with <strong>social</strong>features is quite limited. Though quite some systemswith friends as <strong>peer</strong>s were developed only one system didcombine this successfully with access control. This is One-Swarm.Social-<strong>network</strong> <strong>sites</strong> or otherwise <strong>social</strong> aware <strong>sites</strong> did no<strong>to</strong>ffer any <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> at the moment. Onlycentral server based solutions were available, often limitingusers in their possibilities <strong>to</strong> share easily large <strong>file</strong>s.We made a list of requirements for a combined system,this list was composed of:• Integration with current systems• Detailed control of <strong>sharing</strong>• Trusted <strong>sharing</strong>• Proper scalingWe researched whether it was possible at all <strong>to</strong> combine<strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>file</strong>-<strong>sharing</strong> systems and <strong>social</strong>-<strong>network</strong> <strong>sites</strong>fulfilling these requirements, which did lead us <strong>to</strong> the answerof our main research question.This question was “Can we combine the strong characteristicsof <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> systems and <strong>social</strong>-<strong>network</strong> <strong>sites</strong>?”and can be answered positively. In our study we found outthat it is possible <strong>to</strong> combine both systems in<strong>to</strong> a systemthat gives users the possibility <strong>to</strong> share large amounts ofpossibly confidential data in an effective way that can beaccessed and authenticated <strong>using</strong> a <strong>social</strong>-<strong>network</strong> site.Future work would include actually building this system.For this, the OneSwarm software should be expanded <strong>to</strong>integrate with the friends system with Facebook. Contacthas been established by the author of this paper with theOneSwarm developers. From this communication could
e deduced that the integration of OneSwarm with a <strong>social</strong><strong>network</strong>ing site such as Facebook, is received by theOneSwarm developers as positive. In order <strong>to</strong> realize thisintegration, also a detailed pro<strong>to</strong>col has <strong>to</strong> be specifiedthat interconnects the new client and the new FacebookApplication. Moreover, the the new Facebook Applicationwill have <strong>to</strong> be specified in detail and programmed.Other future work could be related <strong>to</strong> a study on definingwhether the proposed architecture and features could alsobe applied for new concepts in the area of <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong><strong>social</strong>-<strong>network</strong>s [23] like PeerSoN [26]. This is a kind of<strong>social</strong>-<strong>network</strong> that s<strong>to</strong>res all its information in a <strong>peer</strong>-<strong>to</strong><strong>peer</strong>manner, removing the need of s<strong>to</strong>ring all data on onecentral server.7. REFERENCES[1] My Documents. Facebook Application, March 2010.Retrieved March 23, 2010, fromhttp://www.facebook.com/apps/application.php?id=8256642130.[2] SMES<strong>to</strong>rage -File Sharing. Facebook Application,March 2010. Retrieved March 23, 2010, fromhttp://www.facebook.com/apps/application.php?id=20750461633.[3] N. Andrade, M. Mowbray, A. Lima, G. Wagner, andM. Ripeanu. Influences on cooperation in bit<strong>to</strong>rrentcommunities. page 115, 2005.[4] S. Androutsellis-Theo<strong>to</strong>kis and D. Spinellis. Asurvey of <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> content distributiontechnologies. ACM Computing Surveys (CSUR),36(4):371, 2004.[5] D. M. Boyd and N. B. Ellison. Social <strong>network</strong> <strong>sites</strong>:Definition, his<strong>to</strong>ry, and scholarship. JOURNAL OFCOMPUTER MEDIATEDCOMMUNICATION-ELECTRONIC EDITION-,13(1):210, 2007.[6] E. Brands and G. Karagiannis. Taxonomy of P2PApplications. 2009.[7] H. Chen, X. Li, and J. Han. Maze: a <strong>social</strong><strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>network</strong>. 2004.[8] B. Cohen. Incentives build robustness in BitTorrent.6, 2003.[9] Dropbox. Dropbox - Online backup, <strong>file</strong> sync and<strong>sharing</strong> made easy., 2010. Retrieved May 14, 2010,from https://www.dropbox.com.[10] Facebook. Facebook. Website, September 2009.Retrieved May 14, 2010, fromhttp://www.facebook.com/press/info.php?statistics.[11] Facebook. Facebook, 2010. Retrieved May 14, 2010,from http://www.facebook.com.[12] Facebook. Facebook Developers, 2010. RetrievedMay 14, 2010, from http://developers.facebook.com.[13] A. Fast, D. Jensen, and B. N. Levine. Creating<strong>social</strong> <strong>network</strong>s <strong>to</strong> improve <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>network</strong>ing.pages 568–573, 2005.[14] M. Feldman and J. Chuang. Overcoming free-ridingbehavior in <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> systems. ACM SIGecomExchanges, 5(4):50, 2005.[15] S. Garfinkel. PGP: pretty good privacy. O’reilly,1995.[16] Google. Google Talk, 2010. Retrieved May 14, 2010,from http://www.google.com/talk.[17] GPSGate.com. GPS Tracking and Vehicle Trakcing:GpsGate Client, 2010. Retrieved June 6th 2010,from http://gpsgate.com/index.php?id=73.[18] M. House-vording. Azureus Plugin for FacebookIntegration. 2008.[19] T. Isdal, M. Piatek, A. Krishnamurthy, andT. Anderson. Privacy-preserving P2P data <strong>sharing</strong>with OneSwarm. Technical report, 2009.[20] P. Labs. PeerGuardian 2, 2010. Retrieved May 14,2010, from http://phoenixlabs.org/pg2.[21] E. K. Lua, J. Crowcroft, M. Pias, R. Sharma, andS. Lim. A survey and comparison of <strong>peer</strong>-<strong>to</strong>-<strong>peer</strong>overlay <strong>network</strong> schemes. IEEE CommunicationsSurveys & Tu<strong>to</strong>rials, 7(2):72–93, 2005.[22] M. Madden and S. Fox. Riding the waves of “Web2.0.”. Backgrounder, Pew Internet and AmericanLife Project, 23(1), 2007.[23] G. Mezzour, A. Perrig, V. Gligor, andP. Papadimitra<strong>to</strong>s. Privacy-Preserving RelationshipPath Discovery in Social Networks. Cryp<strong>to</strong>logy andNetwork Security, pages 189–208, 2009.[24] MySpace. MySpace, 2010. Retrieved May 21, 2010,from http://www.myspace.com.[25] R. Osbaldes<strong>to</strong>n and G. Bauer. Unofficial Java WebStart/JNLP FAQ, 2010. Retrieved May 28, 2010,from http://lopica.sourceforge.net/faq.html.[26] PeerSoN. PeerSoN - Peer-<strong>to</strong>-Peer Social Networking,2010. Retrieved May 21, 2010, fromhttp://www.<strong>peer</strong>son.net.[27] M. Piatek, T. Kohno, and A. Krishnamurthy.Challenges and directions for moni<strong>to</strong>ring P2P <strong>file</strong><strong>sharing</strong> <strong>network</strong>s–or–Why my printer received aDMCA takedown notice. 2008.[28] J. A. Pouwelse, P. Garbacki, J. Wang, A. Bakker,J. Yang, A. Iosup, D. H. Epema, M. Reinders, M. R.Van Steen, and H. J. Sips. Tribler: A <strong>social</strong>-based<strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> system. Concurrency and Computation,20(2):127, 2008.[29] T. T. Project. Tor: anonymity online, 2010.Retrieved June 6th 2010, fromhttp://www.<strong>to</strong>rproject.org/.[30] Quaji. Quaji: Facebook CSRF attack. RetrievedJune 6th 2010, fromhttp://blog.quaji.com/2009/08/facebook-csrfattack-full-disclosure.html.[31] A. V. Ramachandran and N. Feamster.Authenticated out-of-band communication over<strong>social</strong> links. pages 61–66, 2008.[32] Rapidshare. RapidShare: 1-CLICK Web hosting -Easy Fileshosting, 2010. Retrieved May 14, 2010,from http://rapidshare.com.[33] J. Roozenburg. Secure decentralized swarmdiscovery in tribler. <strong>network</strong>s, 59:16–48, 2006.[34] S. Voulgaris and M. Van Steen. Epidemic-stylemanagement of semantic overlays for content-basedsearching. Euro-Par 2005 Parallel Processing, pages1143–1152, 2005.[35] W3C. Geolocation API Specification. RetrievedJune 6th 2010, fromhttp://www.w3.org/TR/geolocation-API/.[36] T. Whalen, D. Smetters, and E. F. Churchill. Userexperiences with <strong>sharing</strong> and access control. page1522, 2006.[37] Wikipedia. List of <strong>social</strong> <strong>network</strong>ing web<strong>sites</strong>, 2010.Retrieved May 14, 2010, fromhttp://en.wikipedia.org/wiki/List of <strong>social</strong> <strong>network</strong>ing web<strong>sites</strong>.[38] B. Yang and H. Garcia-Molina. Efficient search in<strong>peer</strong>-<strong>to</strong>-<strong>peer</strong> <strong>network</strong>s. 2002.