... WEP Key Rotation in AP2000
... WEP Key Rotation in AP2000
... WEP Key Rotation in AP2000
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
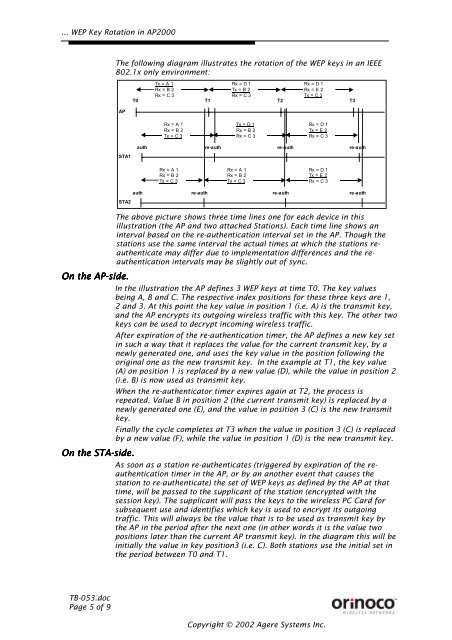
... <strong>WEP</strong> <strong>Key</strong> <strong>Rotation</strong> <strong>in</strong> <strong>AP2000</strong>The follow<strong>in</strong>g diagram illustrates the rotation of the <strong>WEP</strong> keys <strong>in</strong> an IEEE802.1x only environment:APTx = A 1Rx = B 2Rx = C 3Rx = D 1Tx = B 2Rx = C 3Rx = D 1Rx = E 2Tx = C 3T0 T1T2 T3Rx = A 1Rx = B 2Tx = C 3Tx = D 1Rx = B 2Rx = C 3Rx = D 1Tx = E 2Rx = C 3authre-authre-authre-authSTA1Rx = A 1Rx = B 2Tx = C 3Rx = A 1Rx = B 2Tx = C 3Rx = D 1Tx = E 2Rx = C 3authre-authre-authre-authSTA2On the AP-side.On the STA-side.The above picture shows three time l<strong>in</strong>es one for each device <strong>in</strong> thisillustration (the AP and two attached Stations). Each time l<strong>in</strong>e shows an<strong>in</strong>terval based on the re-authentication <strong>in</strong>terval set <strong>in</strong> the AP. Though thestations use the same <strong>in</strong>terval the actual times at which the stations reauthenticatemay differ due to implementation differences and the reauthentication<strong>in</strong>tervals may be slightly out of sync.In the illustration the AP def<strong>in</strong>es 3 <strong>WEP</strong> keys at time T0. The key valuesbe<strong>in</strong>g A, B and C. The respective <strong>in</strong>dex positions for these three keys are 1,2 and 3. At this po<strong>in</strong>t the key value <strong>in</strong> position 1 (i.e. A) is the transmit key,and the AP encrypts its outgo<strong>in</strong>g wireless traffic with this key. The other twokeys can be used to decrypt <strong>in</strong>com<strong>in</strong>g wireless traffic.After expiration of the re-authentication timer, the AP def<strong>in</strong>es a new key set<strong>in</strong> such a way that it replaces the value for the current transmit key, by anewly generated one, and uses the key value <strong>in</strong> the position follow<strong>in</strong>g theorig<strong>in</strong>al one as the new transmit key. In the example at T1, the key value(A) on position 1 is replaced by a new value (D), while the value <strong>in</strong> position 2(i.e. B) is now used as transmit key.When the re-authenticator timer expires aga<strong>in</strong> at T2, the process isrepeated. Value B <strong>in</strong> position 2 (the current transmit key) is replaced by anewly generated one (E), and the value <strong>in</strong> position 3 (C) is the new transmitkey.F<strong>in</strong>ally the cycle completes at T3 when the value <strong>in</strong> position 3 (C) is replacedby a new value (F), while the value <strong>in</strong> position 1 (D) is the new transmit key.As soon as a station re-authenticates (triggered by expiration of the reauthenticationtimer <strong>in</strong> the AP, or by an another event that causes thestation to re-authenticate) the set of <strong>WEP</strong> keys as def<strong>in</strong>ed by the AP at thattime, will be passed to the supplicant of the station (encrypted with thesession key). The supplicant will pass the keys to the wireless PC Card forsubsequent use and identifies which key is used to encrypt its outgo<strong>in</strong>gtraffic. This will always be the value that is to be used as transmit key bythe AP <strong>in</strong> the period after the next one (<strong>in</strong> other words it is the value twopositions later than the current AP transmit key). In the diagram this will be<strong>in</strong>itially the value <strong>in</strong> key position3 (i.e. C). Both stations use the <strong>in</strong>itial set <strong>in</strong>the period between T0 and T1.TB-053.docPage 5 of 9Copyright © 2002 Agere Systems Inc.