Using StrongSwan with smart cards Introduction Prerequisites
Using StrongSwan with smart cards Introduction Prerequisites
Using StrongSwan with smart cards Introduction Prerequisites
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
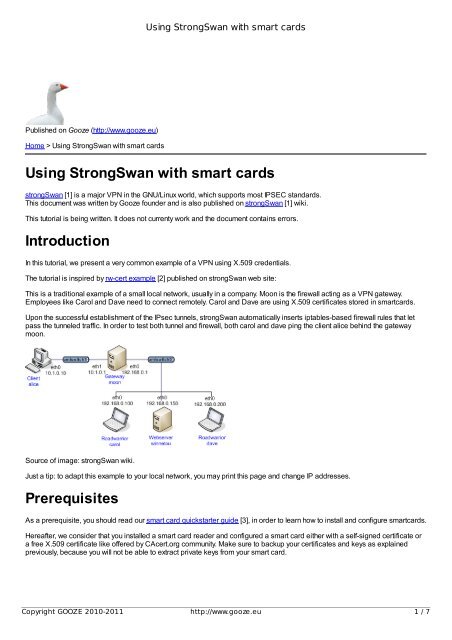
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>Published on Gooze (http://www.gooze.eu)Home > <strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong><strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>strongSwan [1] is a major VPN in the GNU/Linux world, which supports most IPSEC standards.This document was written by Gooze founder and is also published on strongSwan [1] wiki.This tutorial is being written. It does not currenty work and the document contains errors.<strong>Introduction</strong>In this tutorial, we present a very common example of a VPN using X.509 credentials.The tutorial is inspired by rw-cert example [2] published on strongSwan web site:This is a traditional example of a small local network, usually in a company. Moon is the firewall acting as a VPN gateway.Employees like Carol and Dave need to connect remotely. Carol and Dave are using X.509 certificates stored in <strong>smart</strong><strong>cards</strong>.Upon the successful establishment of the IPsec tunnels, strongSwan automatically inserts iptables-based firewall rules that letpass the tunneled traffic. In order to test both tunnel and firewall, both carol and dave ping the client alice behind the gatewaymoon.Source of image: strongSwan wiki.Just a tip: to adapt this example to your local network, you may print this page and change IP addresses.<strong>Prerequisites</strong>As a prerequisite, you should read our <strong>smart</strong> card quickstarter guide [3], in order to learn how to install and configure <strong>smart</strong><strong>cards</strong>.Hereafter, we consider that you installed a <strong>smart</strong> card reader and configured a <strong>smart</strong> card either <strong>with</strong> a self-signed certificate ora free X.509 certificate like offered by CAcert.org community. Make sure to backup your certificates and keys as explainedpreviously, because you will not be able to extract private keys from your <strong>smart</strong> card.Copyright GOOZE 2010-2011 http://www.gooze.eu 1 / 7
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>Installing strongSwan <strong>with</strong> <strong>smart</strong>card supportInstalling from binariesIn Debian based systems, strongswan is compiled <strong>with</strong> <strong>smart</strong>card support. To install strongSwan, type as root:$ apt-get install strongswan ipsecDisplay ipsec version typing this command:$ ipsec versionLinux strongSwan U4.3.2/K2.6.32-trunk-amd64Institute for Internet Technologies and ApplicationsUniversity of Applied Sciences Rapperswil, SwitzerlandSee 'ipsec --copyright' for copyright information.Our station is running strongSwan 4.3.2 on GNU/Linux kernel 2.6.32.Installing from sourcesIf your distribution does not offer strongSwan <strong>with</strong> <strong>smart</strong><strong>cards</strong>, you may need to compile strongSwan [1] from sources:$ ./configure < add your options there > --enable-pluto --enable-<strong>smart</strong>card$ make$ sudo make installA more complex configuration line would be:$ ./configure --enable-pluto --sysconfdir=/etc --prefix=/usr --libexecdir=/usr/lib \--enable-openssl \--enable-nm \--enable-agent \--enable-gcrypt \--enable-integrity-test \--enable-openssl \--enable-eap-gtc --enable-eap-md5 --enable-eap-mschapv2 --enable-eap-aka --enable-eap-aka-3gpp2 --enableeap-identity\--enable-<strong>smart</strong>card$ make$ sudo make installConfiguring gateway MoonAt first, we set up the gateway Moon using a traditional X.509 certificate.Edit /etc/ipsec.conf# /etc/ipsec.conf - strongSwan IPsec configuration fileconfig setupcrlcheckinterval=180strictcrlpolicy=noCopyright GOOZE 2010-2011 http://www.gooze.eu 2 / 7
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>First, you need to inform strongSwan to use the <strong>smart</strong>card reader.strongSwan supports <strong>smart</strong><strong>cards</strong> using only pluto backend.Charon backend does not support <strong>smart</strong><strong>cards</strong>.Edit /etc/ipsec.conf:config setupcrlcheckinterval=180strictcrlpolicy=nocharonstart=noplutostart=yespkcs11module = /usr/lib/opensc-pkcs11.sopkcs11keepstate=yesplutodebug = all # During testing you will need full-debugplutostderrlog = /var/log/pluto.logconn %defaultikelifetime=60mkeylife=20mrekeymargin=3mkeyingtries=1keyexchange=ikev1conn homeleft=%defaultrouteleftcert=%<strong>smart</strong>cardleftfirewall=yesright=192.168.0.1rightid=@moon.strongswan.orgrightsubnet=10.1.0.0/16auto=addIn most cases there is a single <strong>smart</strong>card reader or cryptotoken and only one RSA private key safely stored on the crypto device.The entry:leftcert=%<strong>smart</strong><strong>cards</strong>tands for the full notation:leftcert=%<strong>smart</strong>card#1This is sufficient where the first certificate/private key object enumerated by PKCS#11 module is used. If severalcertificate/private key objects are present then the nth object can be selected usingleftcert=%<strong>smart</strong>card#The ipsec list<strong>cards</strong> command gives an overview over all certifcate objects made available by the PKCS#11 module. CAcertificates are automatically available as trust anchors <strong>with</strong>out the need to copy them into the /etc/ipsec.d/cacerts/ directory first:$ ipsec list<strong>cards</strong>ipsec list<strong>cards</strong>000000 List of Smartcard Objects:Copyright GOOZE 2010-2011 http://www.gooze.eu 4 / 7
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>000000 Apr 09 08:52:05 2010, #1, count: 3000 slot: 5, session closed, logged out, has valid pin000 id: 7645d913d5b4****************324c23a7ebf4000 label: 'CAcert WoT User's Root CA ID'000 subject: 'CN=CAcert WoT User, E=****************, E=*****************'000 Apr 09 08:52:05 2010, #2, count: 1000 slot: 5, session closed, logged out, has no pin000 id: 6d0534d04a8b***************2e33571deec58000 label: 'StartCom Free Certificate Member's StartCom Ltd. ID'000 subject: 'D=1767**************6l5, O=Persona Not Validated, CN=StartCom Free Certificate Member,E=**************'As an alternative the certificate ID and/or the slot number defined by the PKCS#11 standard can be specified using the notationleftcert=%<strong>smart</strong>card:Thusleftcert=%<strong>smart</strong>card:50will look in all available slots for ID 0x50 starting <strong>with</strong> the first slot (usually slot 0) whereasleftcert=%<strong>smart</strong>card4:50As an alternative the certificate ID and/or the slot number defined by the PKCS#11 standard can be specified using the notationleftcert=%<strong>smart</strong>card < slot nr > : < key id in hex format >will directly check slot 4 (which is usually the first slot on the second reader/token when using the OpenSC library) for a key <strong>with</strong>ID 0x50.Entering the PIN codeSince the <strong>smart</strong>card signing operation needed to sign the hash <strong>with</strong> the RSA private key during IKE Main Mode is protected by aPIN code, the secret PIN must be made available to Pluto.For gateways that must be able to start IPsec tunnels automatically in unattended mode after a reboot, the secret PIN can bestored statically in ipsec.secrets: PIN %<strong>smart</strong>card "12345678"or <strong>with</strong> the general notation: PIN %<strong>smart</strong>card ""or alternatively: PIN %<strong>smart</strong>card: ""On a personal notebook computer that could get stolen, you wouldn't want to store your PIN in ipsec.secrets.Thus the alternative formCopyright GOOZE 2010-2011 http://www.gooze.eu 5 / 7
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>: PIN %<strong>smart</strong>card %promptwill prompt you for the PIN when you start up the first IPsec connection using the command$ ipsec up sunThe ipsec up command calls the whack function which in turn communicates <strong>with</strong> Pluto over a socket. Since the whack functioncall is executed from a command window, Pluto can prompt you for the PIN over this socket connection. Unfortunatelyroadwarrior connections which just wait passively for peers cannot be initiated via the command window:conn rwright=%anyrightrsasigkey=%certleft=%defaultrouteleftcert=%<strong>smart</strong>card1:50auto=addBut if there is a corresponding entry: PIN %<strong>smart</strong>card1:50 %promptin ipsec.secrets, then the standard command$ ipsec rereadsecretsor the alias$ ipsec secretscan be used to enter the PIN code for this connection interactively. The command$ ipsec list<strong>cards</strong>can be executed at any time to check the current status of the PIN code[s].PIN-pad equipped <strong>smart</strong>card readersSmartcard readers <strong>with</strong> an integrated PIN pad offer an increased security level because the PIN entry cannot be sniffed on thehost computer e.g. by a surrepticiously installed key logger. In order to tell pluto not to prompt for the PIN on the host itself, theentry: PIN %<strong>smart</strong>card:50 %pinpadcan be used in ipsec.secrets. Because the key pad does not cache the PIN in the <strong>smart</strong>card reader, it must be entered for everyPKCS #11 session login. By default pluto does a session logout after every RSA signature. In order to avoid the repeated entryof the PIN code during the periodic IKE main mode rekeyings, the following parameter can be set in the config setup section ofipsec.conf:config setuppkcs11keepstate=yesThe default setting ispkcs11keepstate=noCopyright GOOZE 2010-2011 http://www.gooze.eu 6 / 7
<strong>Using</strong> <strong>StrongSwan</strong> <strong>with</strong> <strong>smart</strong> <strong>cards</strong>LinksYou may read this very good totorial (in German):http://mopoinfo.vpn.uni-freiburg.de/node/103 [4]Copyright GOOZE.EU 2011.Source URL: http://www.gooze.eu/howto/using-strongswan-<strong>with</strong>-<strong>smart</strong>-<strong>cards</strong>Links:[1] http://www.strongswan.org/[2] http://www.strongswan.org/uml/testresults43/ikev2/rw-cert/[3] http://www.gooze.eu/howto/<strong>smart</strong>-card-quickstarter-guide[4] http://mopoinfo.vpn.uni-freiburg.de/node/103Copyright GOOZE 2010-2011 http://www.gooze.eu 7 / 7