Application Layer Covert Channel Analysis and ... - Bill Buchanan
Application Layer Covert Channel Analysis and ... - Bill Buchanan
Application Layer Covert Channel Analysis and ... - Bill Buchanan
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
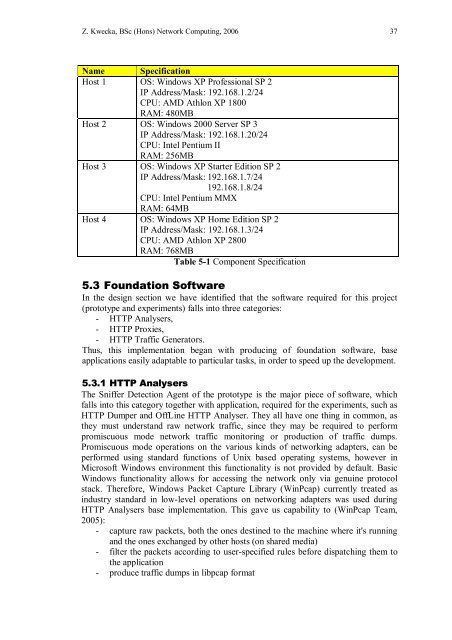
Z. Kwecka, BSc (Hons) Network Computing, 2006 37Name SpecificationHost 1 OS: Windows XP Professional SP 2IP Address/Mask: 192.168.1.2/24CPU: AMD Athlon XP 1800RAM: 480MBHost 2 OS: Windows 2000 Server SP 3IP Address/Mask: 192.168.1.20/24CPU: Intel Pentium IIRAM: 256MBHost 3 OS: Windows XP Starter Edition SP 2IP Address/Mask: 192.168.1.7/24192.168.1.8/24CPU: Intel Pentium MMXRAM: 64MBHost 4 OS: Windows XP Home Edition SP 2IP Address/Mask: 192.168.1.3/24CPU: AMD Athlon XP 2800RAM: 768MBTable 5-1 Component Specification5.3 Foundation SoftwareIn the design section we have identified that the software required for this project(prototype <strong>and</strong> experiments) falls into three categories:- HTTP Analysers,- HTTP Proxies,- HTTP Traffic Generators.Thus, this implementation began with producing of foundation software, baseapplications easily adaptable to particular tasks, in order to speed up the development.5.3.1 HTTP AnalysersThe Sniffer Detection Agent of the prototype is the major piece of software, whichfalls into this category together with application, required for the experiments, such asHTTP Dumper <strong>and</strong> OffLine HTTP Analyser. They all have one thing in common, asthey must underst<strong>and</strong> raw network traffic, since they may be required to performpromiscuous mode network traffic monitoring or production of traffic dumps.Promiscuous mode operations on the various kinds of networking adapters, can beperformed using st<strong>and</strong>ard functions of Unix based operating systems, however inMicrosoft Windows environment this functionality is not provided by default. BasicWindows functionality allows for accessing the network only via genuine protocolstack. Therefore, Windows Packet Capture Library (WinPcap) currently treated asindustry st<strong>and</strong>ard in low-level operations on networking adapters was used duringHTTP Analysers base implementation. This gave us capability to (WinPcap Team,2005):- capture raw packets, both the ones destined to the machine where it's running<strong>and</strong> the ones exchanged by other hosts (on shared media)- filter the packets according to user-specified rules before dispatching them tothe application- produce traffic dumps in libpcap format








![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)






