- Page 1 and 2:
www.it-ebooks.info
- Page 4:
Contents at a GlanceAbout the Autho
- Page 8:
2CHAPTER 1: Getting Started with Ob
- Page 14:
CHAPTER 1: Getting Started with Obj
- Page 18:
CHAPTER 1: Getting Started with Obj
- Page 22:
CHAPTER 1: Getting Started with Obj
- Page 26:
CHAPTER 1: Getting Started with Obj
- Page 30:
CHAPTER 1: Getting Started with Obj
- Page 34:
CHAPTER 1: Getting Started with Obj
- Page 38:
CHAPTER 1: Getting Started with Obj
- Page 42:
CHAPTER 1: Getting Started with Obj
- Page 46:
CHAPTER 1: Getting Started with Obj
- Page 50:
Chapter 2Object-Oriented Programmin
- Page 54:
CHAPTER 2: Object-Oriented Programm
- Page 58:
CHAPTER 2: Object-Oriented Programm
- Page 62:
CHAPTER 2: Object-Oriented Programm
- Page 66:
CHAPTER 2: Object-Oriented Programm
- Page 70:
CHAPTER 2: Object-Oriented Programm
- Page 74:
CHAPTER 2: Object-Oriented Programm
- Page 78:
CHAPTER 2: Object-Oriented Programm
- Page 82:
CHAPTER 2: Object-Oriented Programm
- Page 86:
CHAPTER 2: Object-Oriented Programm
- Page 90:
44CHAPTER 3: Foundational APIsNote
- Page 94:
46CHAPTER 3: Foundational APIsThe -
- Page 98:
48CHAPTER 3: Foundational APIsNSMut
- Page 102:
50CHAPTER 3: Foundational APIsTable
- Page 106:
52CHAPTER 3: Foundational APIsTable
- Page 110:
54CHAPTER 3: Foundational APIsListi
- Page 114:
56CHAPTER 3: Foundational APIs}[the
- Page 118:
58CHAPTER 3: Foundational APIsTesti
- Page 122:
60CHAPTER 3: Foundational APIsTable
- Page 126:
62CHAPTER 3: Foundational APIsListi
- Page 130:
64CHAPTER 3: Foundational APIsa new
- Page 134:
66CHAPTER 3: Foundational APIsNote
- Page 138:
68CHAPTER 3: Foundational APIsThrea
- Page 142:
70CHAPTER 3: Foundational APIsprevi
- Page 146:
72CHAPTER 3: Foundational APIsUsing
- Page 150:
74CHAPTER 3: Foundational APIsplist
- Page 154:
76CHAPTER 4: Objective-C Language F
- Page 158:
78CHAPTER 4: Objective-C Language F
- Page 162:
80CHAPTER 4: Objective-C Language F
- Page 166:
82CHAPTER 4: Objective-C Language F
- Page 170:
84CHAPTER 4: Objective-C Language F
- Page 174: 86CHAPTER 4: Objective-C Language F
- Page 178: 88CHAPTER 4: Objective-C Language F
- Page 182: 90CHAPTER 4: Objective-C Language F
- Page 186: 92CHAPTER 4: Objective-C Language F
- Page 190: 94CHAPTER 4: Objective-C Language F
- Page 194: 96CHAPTER 4: Objective-C Language F
- Page 198: 98CHAPTER 4: Objective-C Language F
- Page 202: 100CHAPTER 4: Objective-C Language
- Page 206: 102CHAPTER 4: Objective-C Language
- Page 210: 104CHAPTER 4: Objective-C Language
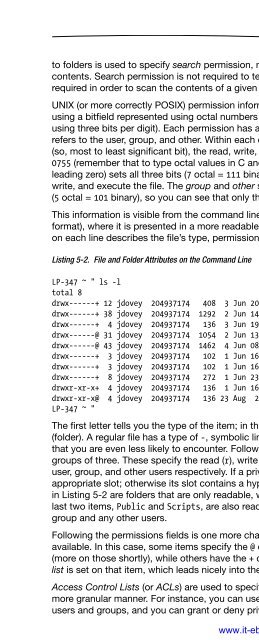
- Page 214: Chapter 5Using the FilesystemThe fi
- Page 218: CHAPTER 5: Using the Filesystem 109
- Page 222: CHAPTER 5: Using the Filesystem 111
- Page 228: 114CHAPTER 5: Using the Filesysteme
- Page 232: 116CHAPTER 5: Using the FilesystemA
- Page 236: 118CHAPTER 5: Using the Filesystemb
- Page 240: 120CHAPTER 5: Using the Filesystem-
- Page 244: 122CHAPTER 5: Using the Filesystem}
- Page 248: 124CHAPTER 5: Using the Filesystem/
- Page 252: 126CHAPTER 5: Using the FilesystemN
- Page 256: 128CHAPTER 5: Using the Filesystemh
- Page 260: 130CHAPTER 5: Using the FilesystemA
- Page 264: 132CHAPTER 5: Using the Filesystemv
- Page 268: 134CHAPTER 5: Using the Filesystem-
- Page 272: 136CHAPTER 5: Using the FilesystemI
- Page 276:
138CHAPTER 5: Using the Filesystemf
- Page 280:
140CHAPTER 5: Using the Filesystem}
- Page 284:
142CHAPTER 5: Using the Filesystemc
- Page 288:
144CHAPTER 5: Using the FilesystemY
- Page 292:
146CHAPTER 5: Using the Filesystem-
- Page 296:
148CHAPTER 5: Using the FilesystemL
- Page 300:
150CHAPTER 5: Using the Filesysteml
- Page 304:
152CHAPTER 5: Using the Filesystem{
- Page 308:
154CHAPTER 5: Using the FilesystemT
- Page 312:
156CHAPTER 5: Using the Filesystemi
- Page 316:
Chapter 6Networking: Connections, D
- Page 320:
CHAPTER 6: Networking: Connections,
- Page 324:
CHAPTER 6: Networking: Connections,
- Page 328:
CHAPTER 6: Networking: Connections,
- Page 332:
CHAPTER 6: Networking: Connections,
- Page 336:
CHAPTER 6: Networking: Connections,
- Page 340:
CHAPTER 6: Networking: Connections,
- Page 344:
CHAPTER 6: Networking: Connections,
- Page 348:
CHAPTER 6: Networking: Connections,
- Page 352:
CHAPTER 6: Networking: Connections,
- Page 356:
CHAPTER 6: Networking: Connections,
- Page 360:
CHAPTER 6: Networking: Connections,
- Page 364:
CHAPTER 6: Networking: Connections,
- Page 368:
CHAPTER 6: Networking: Connections,
- Page 372:
CHAPTER 6: Networking: Connections,
- Page 376:
190CHAPTER 7: User Interfaces: The
- Page 380:
192CHAPTER 7: User Interfaces: The
- Page 384:
194CHAPTER 7: User Interfaces: The
- Page 388:
196CHAPTER 7: User Interfaces: The
- Page 392:
198CHAPTER 7: User Interfaces: The
- Page 396:
200CHAPTER 7: User Interfaces: The
- Page 400:
202CHAPTER 7: User Interfaces: The
- Page 404:
204CHAPTER 7: User Interfaces: The
- Page 408:
206CHAPTER 7: User Interfaces: The
- Page 412:
208CHAPTER 7: User Interfaces: The
- Page 416:
210CHAPTER 7: User Interfaces: The
- Page 420:
212CHAPTER 7: User Interfaces: The
- Page 424:
214CHAPTER 7: User Interfaces: The
- Page 428:
216CHAPTER 7: User Interfaces: The
- Page 432:
218CHAPTER 7: User Interfaces: The
- Page 436:
220CHAPTER 7: User Interfaces: The
- Page 440:
222CHAPTER 7: User Interfaces: The
- Page 444:
224CHAPTER 7: User Interfaces: The
- Page 448:
226CHAPTER 8: Data Management with
- Page 452:
228CHAPTER 8: Data Management with
- Page 456:
230CHAPTER 8: Data Management with
- Page 460:
232CHAPTER 8: Data Management with
- Page 464:
234CHAPTER 8: Data Management with
- Page 468:
236CHAPTER 8: Data Management with
- Page 472:
238CHAPTER 8: Data Management with
- Page 476:
240CHAPTER 8: Data Management with
- Page 480:
242CHAPTER 8: Data Management with
- Page 484:
244CHAPTER 8: Data Management with
- Page 488:
246CHAPTER 8: Data Management with
- Page 492:
248CHAPTER 8: Data Management with
- Page 496:
250CHAPTER 8: Data Management with
- Page 500:
252CHAPTER 8: Data Management with
- Page 504:
254CHAPTER 8: Data Management with
- Page 508:
256CHAPTER 8: Data Management with
- Page 512:
258CHAPTER 8: Data Management with
- Page 516:
260CHAPTER 8: Data Management with
- Page 520:
262CHAPTER 8: Data Management with
- Page 524:
264CHAPTER 8: Data Management with
- Page 528:
266CHAPTER 8: Data Management with
- Page 532:
268CHAPTER 8: Data Management with
- Page 536:
270CHAPTER 9: Writing an Applicatio
- Page 540:
272CHAPTER 9: Writing an Applicatio
- Page 544:
274CHAPTER 9: Writing an Applicatio
- Page 548:
276CHAPTER 9: Writing an Applicatio
- Page 552:
278CHAPTER 9: Writing an Applicatio
- Page 556:
280CHAPTER 9: Writing an Applicatio
- Page 560:
282CHAPTER 9: Writing an Applicatio
- Page 564:
284CHAPTER 9: Writing an Applicatio
- Page 568:
286CHAPTER 9: Writing an Applicatio
- Page 572:
288CHAPTER 9: Writing an Applicatio
- Page 576:
290CHAPTER 9: Writing an Applicatio
- Page 580:
292CHAPTER 9: Writing an Applicatio
- Page 584:
294CHAPTER 9: Writing an Applicatio
- Page 588:
296CHAPTER 9: Writing an Applicatio
- Page 592:
298CHAPTER 9: Writing an Applicatio
- Page 596:
300CHAPTER 9: Writing an Applicatio
- Page 600:
302CHAPTER 9: Writing an Applicatio
- Page 604:
304CHAPTER 9: Writing an Applicatio
- Page 608:
306CHAPTER 9: Writing an Applicatio
- Page 612:
308CHAPTER 9: Writing an Applicatio
- Page 616:
310CHAPTER 9: Writing an Applicatio
- Page 620:
312CHAPTER 9: Writing an Applicatio
- Page 624:
314CHAPTER 9: Writing an Applicatio
- Page 628:
316CHAPTER 9: Writing an Applicatio
- Page 632:
318CHAPTER 9: Writing an Applicatio
- Page 636:
320CHAPTER 9: Writing an Applicatio
- Page 640:
322CHAPTER 9: Writing an Applicatio
- Page 644:
324CHAPTER 9: Writing an Applicatio
- Page 648:
326CHAPTER 9: Writing an Applicatio
- Page 652:
328CHAPTER 9: Writing an Applicatio
- Page 656:
330CHAPTER 9: Writing an Applicatio
- Page 660:
332CHAPTER 9: Writing an Applicatio
- Page 664:
334CHAPTER 9: Writing an Applicatio
- Page 668:
336CHAPTER 9: Writing an Applicatio
- Page 672:
338CHAPTER 9: Writing an Applicatio
- Page 676:
340CHAPTER 9: Writing an Applicatio
- Page 680:
342CHAPTER 9: Writing an Applicatio
- Page 684:
344CHAPTER 9: Writing an Applicatio
- Page 688:
346CHAPTER 9: Writing an Applicatio
- Page 692:
348CHAPTER 9: Writing an Applicatio
- Page 696:
350CHAPTER 9: Writing an Applicatio
- Page 700:
Chapter 10Après Code: Distributing
- Page 704:
CHAPTER 10: Après Code: Distributi
- Page 708:
CHAPTER 10: Après Code: Distributi
- Page 712:
CHAPTER 10: Après Code: Distributi
- Page 716:
CHAPTER 10: Après Code: Distributi
- Page 720:
CHAPTER 10: Après Code: Distributi
- Page 724:
CHAPTER 10: Après Code: Distributi
- Page 728:
CHAPTER 10: Après Code: Distributi
- Page 732:
CHAPTER 10: Après Code: Distributi
- Page 736:
372IndexApplication writing (cont.)
- Page 740:
374IndexCocoa URL loading system (c
- Page 744:
376IndexFoundational APIs (cont.)NS
- Page 748:
378Index■ OObjective-C programmin
- Page 752:
380IndexStrong and weak references,
- Page 756:
Beginning Objective-CJames DoveyAsh
- Page 760:
For the bookends of the process: Cl
- Page 764:
viiiContentsLoops21Objective-C Addi
- Page 768:
xContentsSearching with Spotlight14
- Page 772:
xiiContentsAdding and Removing Peop
- Page 776:
About the AuthorsJim Dovey has been
- Page 780:
AcknowledgmentsNone of this would h