Anomaly Detection for Monitoring
anomaly-detection-monitoring
anomaly-detection-monitoring
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
A Real Example of <strong>Anomaly</strong> <strong>Detection</strong><br />
Around the year 2008, Evan Miller published a paper describing<br />
real-time anomaly detection in operation at IMVU. 1 This was<br />
Baron’s first exposure to anomaly detection:<br />
At approximately 5 AM Friday, it first detects a problem [in the<br />
number of IMVU users who invited their Hotmail contacts to open<br />
an account], which persists most of the day. In fact, an external service<br />
provider had changed an interface early Friday morning,<br />
affecting some but not all of our users.<br />
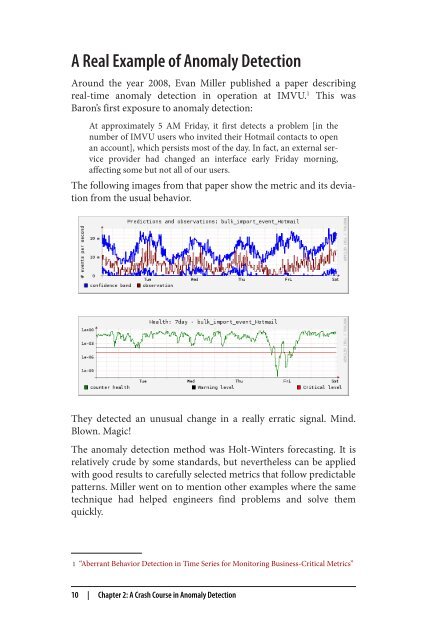
The following images from that paper show the metric and its deviation<br />
from the usual behavior.<br />
They detected an unusual change in a really erratic signal. Mind.<br />
Blown. Magic!<br />
The anomaly detection method was Holt-Winters <strong>for</strong>ecasting. It is<br />
relatively crude by some standards, but nevertheless can be applied<br />
with good results to carefully selected metrics that follow predictable<br />
patterns. Miller went on to mention other examples where the same<br />
technique had helped engineers find problems and solve them<br />
quickly.<br />
1 “Aberrant Behavior <strong>Detection</strong> in Time Series <strong>for</strong> <strong>Monitoring</strong> Business-Critical Metrics”<br />
10 | Chapter 2: A Crash Course in <strong>Anomaly</strong> <strong>Detection</strong>