The Cyber Defense eMagazine August Edition for 2023
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
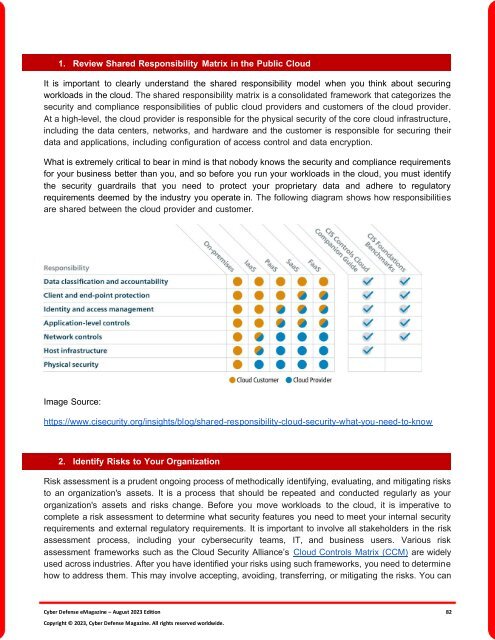
1. Review Shared Responsibility Matrix in the Public Cloud<br />
It is important to clearly understand the shared responsibility model when you think about securing<br />
workloads in the cloud. <strong>The</strong> shared responsibility matrix is a consolidated framework that categorizes the<br />
security and compliance responsibilities of public cloud providers and customers of the cloud provider.<br />
At a high-level, the cloud provider is responsible <strong>for</strong> the physical security of the core cloud infrastructure,<br />
including the data centers, networks, and hardware and the customer is responsible <strong>for</strong> securing their<br />
data and applications, including configuration of access control and data encryption.<br />
What is extremely critical to bear in mind is that nobody knows the security and compliance requirements<br />
<strong>for</strong> your business better than you, and so be<strong>for</strong>e you run your workloads in the cloud, you must identify<br />
the security guardrails that you need to protect your proprietary data and adhere to regulatory<br />
requirements deemed by the industry you operate in. <strong>The</strong> following diagram shows how responsibilities<br />
are shared between the cloud provider and customer.<br />
Image Source:<br />
https://www.cisecurity.org/insights/blog/shared-responsibility-cloud-security-what-you-need-to-know<br />
2. Identify Risks to Your Organization<br />
Risk assessment is a prudent ongoing process of methodically identifying, evaluating, and mitigating risks<br />
to an organization's assets. It is a process that should be repeated and conducted regularly as your<br />
organization's assets and risks change. Be<strong>for</strong>e you move workloads to the cloud, it is imperative to<br />
complete a risk assessment to determine what security features you need to meet your internal security<br />
requirements and external regulatory requirements. It is important to involve all stakeholders in the risk<br />
assessment process, including your cybersecurity teams, IT, and business users. Various risk<br />
assessment frameworks such as the Cloud Security Alliance’s Cloud Controls Matrix (CCM) are widely<br />
used across industries. After you have identified your risks using such frameworks, you need to determine<br />
how to address them. This may involve accepting, avoiding, transferring, or mitigating the risks. You can<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>August</strong> <strong>2023</strong> <strong>Edition</strong> 82<br />
Copyright © <strong>2023</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.