The Cyber Defense eMagazine August Edition for 2023
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
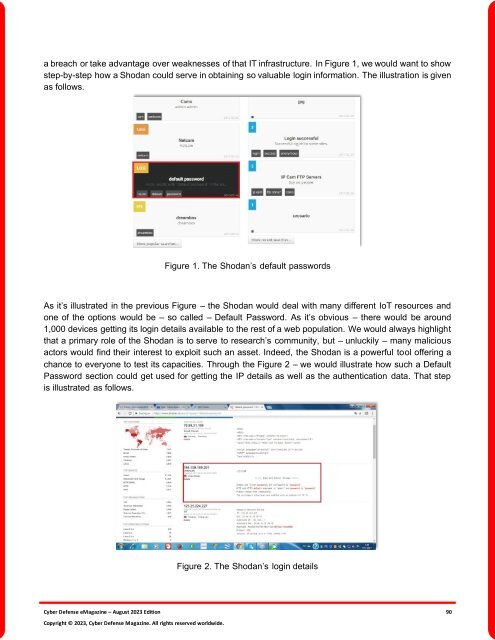
a breach or take advantage over weaknesses of that IT infrastructure. In Figure 1, we would want to show<br />
step-by-step how a Shodan could serve in obtaining so valuable login in<strong>for</strong>mation. <strong>The</strong> illustration is given<br />
as follows.<br />
Figure 1. <strong>The</strong> Shodan’s default passwords<br />
As it’s illustrated in the previous Figure – the Shodan would deal with many different IoT resources and<br />
one of the options would be – so called – Default Password. As it’s obvious – there would be around<br />
1,000 devices getting its login details available to the rest of a web population. We would always highlight<br />
that a primary role of the Shodan is to serve to research’s community, but – unluckily – many malicious<br />
actors would find their interest to exploit such an asset. Indeed, the Shodan is a powerful tool offering a<br />
chance to everyone to test its capacities. Through the Figure 2 – we would illustrate how such a Default<br />
Password section could get used <strong>for</strong> getting the IP details as well as the authentication data. That step<br />
is illustrated as follows.<br />
Figure 2. <strong>The</strong> Shodan’s login details<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>August</strong> <strong>2023</strong> <strong>Edition</strong> 90<br />
Copyright © <strong>2023</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.