The Cyber Defense eMagazine August Edition for 2023
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
Cyber Defense eMagazine August Edition for 2023 #CDM #CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
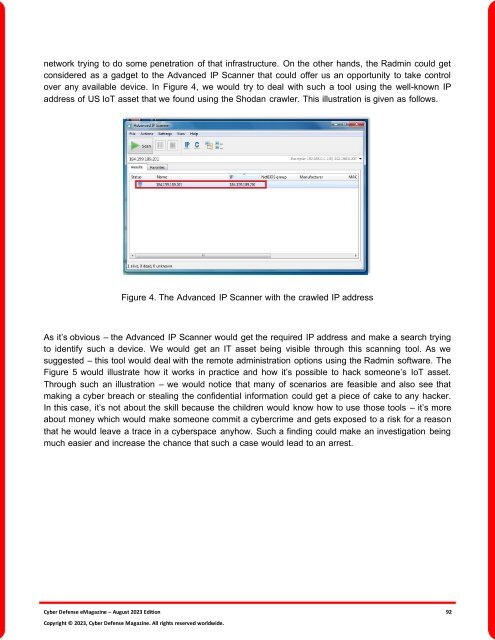
network trying to do some penetration of that infrastructure. On the other hands, the Radmin could get<br />
considered as a gadget to the Advanced IP Scanner that could offer us an opportunity to take control<br />
over any available device. In Figure 4, we would try to deal with such a tool using the well-known IP<br />
address of US IoT asset that we found using the Shodan crawler. This illustration is given as follows.<br />
Figure 4. <strong>The</strong> Advanced IP Scanner with the crawled IP address<br />
As it’s obvious – the Advanced IP Scanner would get the required IP address and make a search trying<br />
to identify such a device. We would get an IT asset being visible through this scanning tool. As we<br />
suggested – this tool would deal with the remote administration options using the Radmin software. <strong>The</strong><br />
Figure 5 would illustrate how it works in practice and how it’s possible to hack someone’s IoT asset.<br />
Through such an illustration – we would notice that many of scenarios are feasible and also see that<br />
making a cyber breach or stealing the confidential in<strong>for</strong>mation could get a piece of cake to any hacker.<br />
In this case, it’s not about the skill because the children would know how to use those tools – it’s more<br />
about money which would make someone commit a cybercrime and gets exposed to a risk <strong>for</strong> a reason<br />
that he would leave a trace in a cyberspace anyhow. Such a finding could make an investigation being<br />
much easier and increase the chance that such a case would lead to an arrest.<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>August</strong> <strong>2023</strong> <strong>Edition</strong> 92<br />
Copyright © <strong>2023</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.