Quick introduction to reverse engineering for beginners
Quick introduction to reverse engineering for beginners
Quick introduction to reverse engineering for beginners
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
push edx<br />
mov eax, DWORD PTR _i$[ebp]<br />
push eax<br />
push OFFSET $SG2463<br />
call _printf<br />
add esp, 12 ; 0000000cH<br />
jmp SHORT $LN2@main<br />
$LN1@main:<br />
xor eax, eax<br />
mov esp, ebp<br />
pop ebp<br />
ret 0<br />
_main ENDP<br />
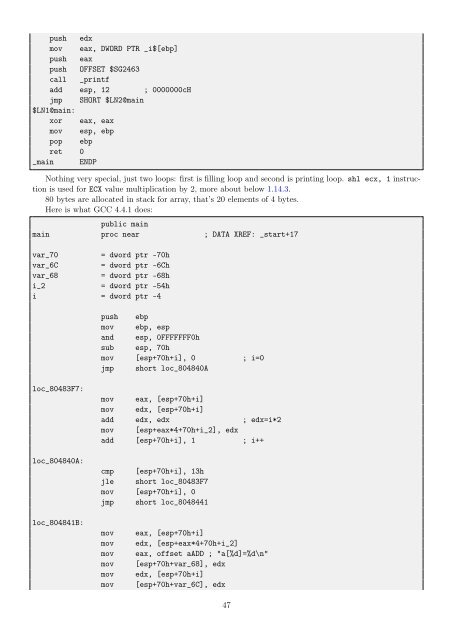
Nothing very special, just two loops: first is filling loop and second is printing loop. shl ecx, 1 instruction<br />
is used <strong>for</strong> ECX value multiplication by 2, more about below 1.14.3.<br />
80 bytes are allocated in stack <strong>for</strong> array, that’s 20 elements of 4 bytes.<br />
Here is what GCC 4.4.1 does:<br />
public main<br />
main proc near ; DATA XREF: _start+17<br />
var_70 = dword ptr -70h<br />
var_6C = dword ptr -6Ch<br />
var_68 = dword ptr -68h<br />
i_2 = dword ptr -54h<br />
i = dword ptr -4<br />
loc_80483F7:<br />
loc_804840A:<br />
loc_804841B:<br />
push ebp<br />
mov ebp, esp<br />
and esp, 0FFFFFFF0h<br />
sub esp, 70h<br />
mov [esp+70h+i], 0 ; i=0<br />
jmp short loc_804840A<br />
mov eax, [esp+70h+i]<br />
mov edx, [esp+70h+i]<br />
add edx, edx ; edx=i*2<br />
mov [esp+eax*4+70h+i_2], edx<br />
add [esp+70h+i], 1 ; i++<br />
cmp [esp+70h+i], 13h<br />
jle short loc_80483F7<br />
mov [esp+70h+i], 0<br />
jmp short loc_8048441<br />
mov eax, [esp+70h+i]<br />
mov edx, [esp+eax*4+70h+i_2]<br />
mov eax, offset aADD ; "a[%d]=%d\n"<br />
mov [esp+70h+var_68], edx<br />
mov edx, [esp+70h+i]<br />
mov [esp+70h+var_6C], edx<br />
47