Quick introduction to reverse engineering for beginners
Quick introduction to reverse engineering for beginners
Quick introduction to reverse engineering for beginners
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
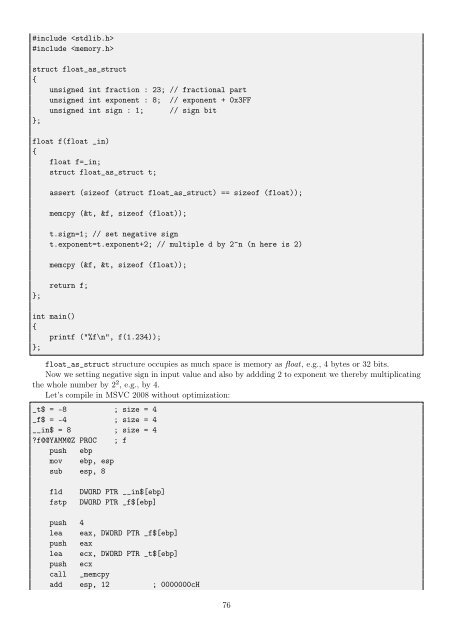
#include <br />
#include <br />
struct float_as_struct<br />
{<br />
unsigned int fraction : 23; // fractional part<br />
unsigned int exponent : 8; // exponent + 0x3FF<br />
unsigned int sign : 1; // sign bit<br />
};<br />
float f(float _in)<br />
{<br />
float f=_in;<br />
struct float_as_struct t;<br />
};<br />
assert (sizeof (struct float_as_struct) == sizeof (float));<br />
memcpy (&t, &f, sizeof (float));<br />
t.sign=1; // set negative sign<br />
t.exponent=t.exponent+2; // multiple d by 2^n (n here is 2)<br />
memcpy (&f, &t, sizeof (float));<br />
return f;<br />
int main()<br />
{<br />
printf ("%f\n", f(1.234));<br />
};<br />
float_as_struct structure occupies as much space is memory as float, e.g., 4 bytes or 32 bits.<br />
Now we setting negative sign in input value and also by addding 2 <strong>to</strong> exponent we thereby multiplicating<br />
the whole number by 2 2 , e.g., by 4.<br />
Let’s compile in MSVC 2008 without optimization:<br />
_t$ = -8 ; size = 4<br />
_f$ = -4 ; size = 4<br />
__in$ = 8 ; size = 4<br />
?f@@YAMM@Z PROC ; f<br />
push ebp<br />
mov ebp, esp<br />
sub esp, 8<br />
fld DWORD PTR __in$[ebp]<br />
fstp DWORD PTR _f$[ebp]<br />
push 4<br />
lea eax, DWORD PTR _f$[ebp]<br />
push eax<br />
lea ecx, DWORD PTR _t$[ebp]<br />
push ecx<br />
call _memcpy<br />
add esp, 12 ; 0000000cH<br />
76