Introduction to Unix and Networks
Introduction to Unix and Networks
Introduction to Unix and Networks
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Title: <strong>Introduction</strong> <strong>to</strong> <strong>Unix</strong> <strong>and</strong> <strong>Networks</strong><br />
Prerequisites: None<br />
Languages: None<br />
Time: 1hour<br />
Schedule: Chapter 2<br />
Requirements: Linux on a networ k<br />
$man unix<br />
core dump<br />
$<br />
Summar y:<br />
This is a shortintroduction <strong>to</strong> computing facilities based on Linux PCs with networ king connection.<br />
Learning Objectives:<br />
To practise the connect / login <strong>and</strong> logout procedures & remote access <strong>to</strong> the networ k<br />
To gain some familiar ity <strong>and</strong> confidence with simple <strong>Unix</strong> comm<strong>and</strong>s <strong>and</strong> the use of X-windows<br />
To contrast the File Manager <strong>and</strong> comm<strong>and</strong> line approach <strong>to</strong> file h<strong>and</strong>ling.<br />
Underst<strong>and</strong> the interrelationship between the var ious systems.<br />
To underst<strong>and</strong> how <strong>to</strong>transfer files around the networ k <strong>and</strong> access printers.<br />
To use an edi<strong>to</strong>r such as vi or emacs.<br />
Be confident in using basic Internet facilities.<br />
To dev elop simple C programs.<br />
Commercial Relevance:<br />
Until recently,any major database server orlarge host connected <strong>to</strong> the Internet would have run <strong>Unix</strong>,<br />
probably Sun/Solaris or HP/UX. Microsoft Windows has now begun <strong>to</strong> capture some of this sec<strong>to</strong>r. Another<br />
recent change is the emergence of Linux as a force within the commercial marketplace, especially for "backroom"<br />
systems.<br />
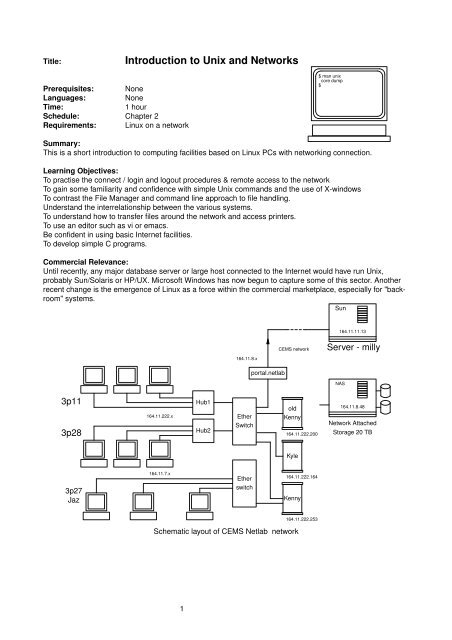
3p11<br />
3p28<br />
3p27<br />
Jaz<br />
164.11.222.x<br />
164.11.7.x<br />
Hub1<br />
Hub2<br />
164.11.8.x<br />
Ether<br />
Switch<br />
Ether<br />
switch<br />
por tal.netlab<br />
CEMS networ k<br />
old<br />
Kenny<br />
Kyle<br />
Kenny<br />
Schematic layout of CEMS Netlab networ k<br />
1<br />
164.11.222.200<br />
164.11.222.164<br />
164.11.222.253<br />
Sun<br />
164.11.11.13<br />
Ser ver - milly<br />
NAS<br />
164.11.8.48<br />
Networ k Attached<br />
S<strong>to</strong>rage 20 TB
The role of an operating system, such as <strong>Unix</strong> or Windows-XP, is<strong>to</strong>assist the user <strong>and</strong> protect the hardware.<br />
Operating systems are large, complex programs, orgroups of programs, designed <strong>to</strong> help application<br />
programs employ the resources of the computer more securely <strong>and</strong> efficiently. With multi-user systems, <strong>and</strong><br />
ev en single-user multi-tasking systems, the allocation, arbitration <strong>and</strong> control of shared resources is a<br />
pr imary function. When the computer is shared between a number of users, the problem of data security<br />
becomes paramount. More <strong>and</strong> more, the operating system provides convenient access <strong>to</strong> a networ k <strong>and</strong> the<br />
Inter net beyond. <strong>Unix</strong> remains an important commercial example, <strong>and</strong> has also attracted more enthusiasts<br />
with the introduction of the freely distributed Linux version.<br />
1. Logging on<br />
This wor ksheet requires you <strong>to</strong> wor k with Linux, so you may have <strong>to</strong>reboot the PC. Check <strong>to</strong>see if your PC<br />
needs <strong>to</strong> be turned on, or just rebooted if it is currently running Windows. Log on with your CEMS user id<br />
<strong>and</strong> netlab password which may bedifferent from that for the main networ k. Note that <strong>Unix</strong> respects the<br />
upper/lowercase distinction, so be careful entering the allocated password. The password scheme for Netlab<br />
Linux is separate from the main <strong>Unix</strong> <strong>and</strong> PC networ ks in the rest of the University. Yes, you could end up<br />
having <strong>to</strong> remember 4 distinct passwords! At the last count, I discovered that I was remembering 13 different<br />
passwords <strong>and</strong> identity codes. How ever, at UWE, you can set them all the same value if you wish.<br />
Although it would be nice <strong>to</strong> have a single password for all UWE facilities: librar y, email, ITS computing,<br />
CEMS computing, WiFi connection, remote login from home, web page administration, this has not yet been<br />
achieved <strong>and</strong> you will still need <strong>to</strong> remember several distinct passwords. You can set most of these <strong>to</strong> the<br />
same value if that suits you. But do not overlook the need for effective, appropr iate secur ity. Because the<br />
university takes a ver y ser ious view onplager ism (copying). Allowing others <strong>to</strong> get access <strong>to</strong> your personal<br />
files can lead you in<strong>to</strong> deep trouble with UWE. Certainly NEVER allow others the right <strong>to</strong> send emails from<br />
your account when you are not present.<br />
Changing a <strong>Unix</strong> password <strong>to</strong> some more personally memorable item is easy, but make sure you do<br />
remember your new password. For security reasons it is good practice <strong>to</strong> include a non-letter (number or<br />
punctuation) in the password <strong>to</strong> discourage "dictionary scanning". Car numbers are a good source, but don’t<br />
be daft <strong>and</strong> use your current number plate.<br />
Tr y guessing a friend’s password, <strong>and</strong> note down your strategies. Most malign hacking involves reading a<br />
password from a PostIT note stuck <strong>to</strong>anadmin terminal, or given over the phone.<br />
Av oid guessable items for your own password!<br />
We usually recommend that you do not change the original, unmemorable passwords immediately. Wait until<br />
you are more familiar with the UWE system. But this is the way you do it:<br />
rob@kenny> passwd<br />
Please enter your old password:<br />
Please enter your new password:<br />
Please enter your password again:<br />
Your password has now been changed.<br />
rob@kenny><br />
When you login (or start anew shell), the <strong>Unix</strong> operating system will try <strong>to</strong>execute setup instructions held in<br />
anumber of st<strong>and</strong>ard script files. Typically these instructions will initialize some environment var iables, such<br />
as PS1, PATH<strong>and</strong> TERM. Look in<strong>to</strong> the following files, note they are hidden fromls by the leading ".". You<br />
must usels -al or select [View] -> [Show Hidden Files] for the file browser.<br />
1 /etc/profile at login, by the initial shell<br />
2 ~/.bash_profile<br />
3 ~/bash_login<br />
4 ~/.profile<br />
~/.bashrc at each new shell start up<br />
~/bash_logout by initial shell at logout<br />
There are 3 files you really need <strong>to</strong> underst<strong>and</strong> when cus<strong>to</strong>mizing the bash shell: /etc/profile, ~/.bash_profile,<br />
<strong>and</strong> ~/.bashrc. Inspect /etc/profile (more /etc/profile which holds global initialization comm<strong>and</strong>s for<br />
ev ery user. Each user can have an personalised ~/.bash_profile which is executed only at login. It is NOT<br />
executed for each shell, only the login shell. However, ~/.bashrc is executed for each new shell except the<br />
2
login shell. It is recommened that you put all your special shell cus<strong>to</strong>mizations in<strong>to</strong> your .bashrc file, <strong>and</strong> set<br />
.bash_profile <strong>to</strong> call .bashrc with the comm<strong>and</strong>:source ~/.bashrc.<br />
The most important set-up action is <strong>to</strong> initialise thePATH variable. This tells the <strong>Unix</strong> shell where <strong>to</strong> find<br />
executable programs. Ifitisnot set up, noprograms can be found, or run. Quite tragic. Now look at its value<br />
for your session:<br />
# printenv PATH<br />
/usr/local/bin:/usr/bin:/bin:/usr/bin/X11:/usr/games:$HOME/bin<br />
#<br />
To add another direc<strong>to</strong>ry, such as your current one (indicated by the .), <strong>to</strong> the PATH,<br />
you could use the following:<br />
# export PATH=${PATH}:.<br />
look here<br />
# printenv PATH<br />
/usr/local/bin:/usr/bin:/bin:/usr/bin/X11:/usr/games:$HOME/bin:.<br />
#<br />
Note the use of { } <strong>to</strong> define clearly what the var iable name is. Otherwise the $ prefix could extend in scope <strong>to</strong><br />
the end of the line. Alter natively, you could addexport PATH=${PATH}:. <strong>to</strong> your.bash initialization file.<br />
As an exper iment, tr y clear ing PATH, <strong>and</strong> see what results. But before you do it, make sure you know how <strong>to</strong><br />
reset it:<br />
COMMENTS<br />
# OLDPATH=$PATH save value in PATH<br />
# PATH="" clear PATH<br />
# emacs tr y <strong>to</strong> run an application<br />
-bash: emacs: No such file or direc<strong>to</strong>ry error from Linux !!<br />
# PATH=$OLDPATH res<strong>to</strong>re PATH’s value<br />
# emacs & all OK now again<br />
#<br />
When you are registered on a <strong>Unix</strong> system as a user, you are allocated a UID (user identity number). Also<br />
you can join groups of other users. Use the comm<strong>and</strong>swhoami <strong>and</strong>id <strong>to</strong> find out who you are. Once logged<br />
in, you maybeable <strong>to</strong>switch user identity usingsu, but at UWE this is a privileged comm<strong>and</strong>, limited <strong>to</strong><br />
administra<strong>to</strong>rs only.<br />
2. The <strong>Unix</strong> Filesystem<br />
There is a general pattern which all <strong>Unix</strong> file system hierarchies keep <strong>to</strong>, although it does var y abit when<br />
moving between HP/UX, Solaris, <strong>and</strong> all the Linuxes. When logged in, list the root direc<strong>to</strong>ry ofyour desk<strong>to</strong>p<br />
machine:<br />
# ls -al /<br />
bin/ etc/ initrd/ local/ proc/ sys/ tmp/ vmlinuz@<br />
boot/ floppy/ initrd.img@ mnt/ root/ tftpboot/ usr/<br />
dev/ home/ lib/ opt/ sbin/ tftpboot.tgz var/<br />
#<br />
The direc<strong>to</strong>ry patter n is best expressed in a tree diagram, each of the nodes also elaborate the hierarchy<br />
fur ther,until the files themselves are reached. Here is the <strong>to</strong>p level direc<strong>to</strong>r y tree:<br />
bin boot dev etc home local mnt proc sbin tmp usr var<br />
Take a look in each of the <strong>to</strong>p level subdirec<strong>to</strong>r ies <strong>and</strong> decide what kind of files, used for what purpose, are<br />
s<strong>to</strong>red there:cd /bin; ls -al<br />
3<br />
/
3. The network<br />
The UWE CEMS faculty has a main networ k, <strong>and</strong> an exper imental networ k called Netlab. The main networ k<br />
has some 17 subnets <strong>and</strong> 500 hosts (notably milly the main Sun multiprocessor), including all the staff<br />
rooms,student PC <strong>and</strong> <strong>Unix</strong> labs, <strong>and</strong> so becomes ver y complex. The much smaller exper imental networ k<br />
only covers 3p11, 3p27, 2p28, 2n24 <strong>and</strong> the local servers, notably kenny, asinthe preceding diagram.<br />
This networ k diagram only shows the interconnectivity of the var ious hosts accessible from the Netlab<br />
networ k. The main University networ k is really <strong>to</strong>o complex <strong>to</strong>bother with, but from the users’ point of viewit<br />
all acts like agigantic central switch, routing packets between all the subnets.<br />
The distribution <strong>and</strong> routing of data packets along local area networ ks (LAN) <strong>and</strong> out across the Internet is<br />
based on the TCP/IP pro<strong>to</strong>cols. These pro<strong>to</strong>cols specify data packet for mats, comm<strong>and</strong> codes, responses<br />
<strong>and</strong> conventions. They were originally devised as part ofthe US Department of Defense (DOD) computer<br />
communications research program <strong>and</strong> were intended <strong>to</strong> allow easy exchange of data within the US<br />
Research <strong>and</strong> Military community. They became the premier st<strong>and</strong>ard mainly because they wor ked well <strong>and</strong><br />
were readily available through the <strong>Unix</strong> operating system.<br />
The var ious networ k IP numbers are inserted on<strong>to</strong> the first diagram next <strong>to</strong>the hosts <strong>and</strong> LAN segments<br />
(subnets) <strong>to</strong> which they apply. The quad-dotted IP numbers are like telephone numbers, they allow you <strong>to</strong><br />
refer <strong>to</strong> subnets <strong>and</strong> individual connected devices, such as PCs, printers, routers. Each device is allocated a<br />
globally unique 32 bit address number, which is normally written in quadruple dotted notation. For my<br />
workstation, called olves<strong>to</strong>n, the IP number is written as 164.11.253.36. This is actually:<br />
10100100000010111111110100100100 in binary, summar ized in hex for mat as: A40BFD24 . You can see<br />
the advantage <strong>to</strong> having friendly names such as milly <strong>and</strong> kenny allocated <strong>to</strong> each computer!<br />
In 3p11 the host numbers are allocated <strong>to</strong> the PCs in this way:<br />
164.11.222.01,<br />
164.11.222.02,<br />
164.11.222.03, <strong>and</strong> so on.<br />
Note that the left h<strong>and</strong> "164.11" is the University domain address on the internet. The "222" is the subnet<br />
address for the Netlab LAN, <strong>and</strong> the righth<strong>and</strong>, least significant numbers such as "02" refer uniquely <strong>to</strong><br />
individual computers. Asalready explained, hosts are normally referred <strong>to</strong> by name, such as kenny or milly.<br />
The official name <strong>and</strong> IP number can be used interchangeably in most circumstances<br />
Find out the name <strong>and</strong> IP number of your current wor kstation by usinghostname -i orifconfig,<br />
(on XP useipconfig).<br />
Youcan trytesting for other hosts on the net by usingping. Ping also tells you how long it takes for a<br />
packet <strong>to</strong>reach its destination.<br />
rob@kenny> ping milly<br />
PING milly.cems.uwe.ac.uk (164.11.11.13): 56 octets data<br />
64 octets from 164.11.11.13: icmp_seq=0 ttl=253 time=0.6 ms<br />
64 octets from 164.11.11.13: icmp_seq=1 ttl=253 time=0.5 ms<br />
64 octets from 164.11.11.13: icmp_seq=2 ttl=253 time=0.5 ms<br />
64 octets from 164.11.11.13: icmp_seq=3 ttl=253 time=0.5 ms<br />
64 octets from 164.11.11.13: icmp_seq=4 ttl=253 time=0.6 ms<br />
64 octets from 164.11.11.13: icmp_seq=5 ttl=253 time=0.5 ms<br />
ˆC<br />
--- milly.cems.uwe.ac.uk ping statistics ---<br />
7packets transmitted, 6 packets received, 0% packet loss<br />
round-trip min/avg/max = 0.5/0.5/0.6 ms<br />
rob@kenny><br />
4. Logging out<br />
Use [CNTRL/ALT/DEL] <strong>and</strong> selectlogout for nor mal exit. Don’t turn off the power because then it takes<br />
longer for the next student <strong>to</strong> log on. Don’t forget <strong>to</strong> logout! There is a screen/key-lock facility if you want <strong>to</strong><br />
pop out <strong>to</strong> the loo.<br />
4
5. <strong>Unix</strong> basic comm<strong>and</strong>s<br />
All self-respecting computers have a program called the Operating System <strong>to</strong> organize the facilities, protect<br />
the hardware from ignorant/malicious programs <strong>and</strong> generally help the user <strong>to</strong> have a good time. <strong>Unix</strong> is one<br />
of the most stable Operating Systems currently available. Sun’s Solar is, HP/UX <strong>and</strong> Linux are three well<br />
known versions of <strong>Unix</strong>. Most of the fastest wor kstations have been designed <strong>to</strong> run <strong>Unix</strong> because of its<br />
facility <strong>to</strong> deal with multi-processor hardware. Windows has not yet demonstrated long-term success in this<br />
niche, itisalso some-what cramped by the 32-bit Pentium, whereas the newer 64-bit CPUs (Alpha, ARM,<br />
HP/PA, Itanium) are already running <strong>Unix</strong>.<br />
<strong>Unix</strong> is a <strong>to</strong>ol kit. There are hundreds of comm<strong>and</strong>s <strong>and</strong> <strong>to</strong>ols <strong>to</strong> help the knowledgeable programmer. Many<br />
of the original, cryptic comm<strong>and</strong> line <strong>to</strong>ols have now been repackaged for the X-windows <strong>and</strong> so are<br />
conveniently GUI-based. To s<strong>to</strong>p a <strong>Unix</strong> process (a running program) try using[CNTRL C]. This usually<br />
works, else you must identify its process number, using theps comm<strong>and</strong>, <strong>and</strong> use this withkill.<br />
ls direc<strong>to</strong>r y file listing,ls -al for more details<br />
ls list current direc<strong>to</strong>ry<br />
ls -al ~ detailed listing of home direc<strong>to</strong>ry<br />
ls / list <strong>to</strong>p level, root direc<strong>to</strong>ry<br />
ls -al Projects list contents of subdirec<strong>to</strong>ry, Projects<br />
ls /tmp/*.ps list names of all PostScr ipt file in /tmp<br />
cat ormore list contents of a text file<br />
mkdir ~/Newdir create a new subdirec<strong>to</strong>r y<br />
rmdir<br />
cd /tmp change current wor king direc<strong>to</strong>r y<br />
rm junkfile remove/delete a file<br />
cp oldfile newfile copy afile<br />
mv oldfile newfile move a file<br />
pwd pr int current wor king direc<strong>to</strong>r y<br />
hostname pr int host name,hostname -i for IPnumber<br />
ps list processes,ps -AF for all processes<br />
kill pid kill a process<br />
man kill Help from <strong>Unix</strong> about thekill comm<strong>and</strong><br />
xclock & display aclock, releasing the keyboard<br />
find ~ -name prog.c -print find a file<br />
grep -rs "marks" ~ locate any ofmyfiles referr ing <strong>to</strong> marks<br />
date<br />
wc file.txt letter, word & liner count<br />
whereis xeyes locate an executable<br />
file something test the file-type of a file called something<br />
So, boot up a PC in<strong>to</strong> Linux, start the X windowing system if necessary from the comm<strong>and</strong> line by typing:<br />
startx,then use the RMB <strong>to</strong> select shells->xterm from the main window panel. This allows you <strong>to</strong> startup<br />
comm<strong>and</strong> windows <strong>and</strong> type in comm<strong>and</strong>s <strong>to</strong> <strong>Unix</strong>. Try these example commamds:<br />
ps list your processes with PID number<br />
ps -FA<br />
hostname -i; hostname -d<br />
/sbin/ifconfig -a another way <strong>to</strong> find out your local IP number<br />
xeyes & star t xe y es inthe background, note the "&"<br />
ps<br />
kill xxx inser t the PID number for the xeyes process<br />
xeyes &<br />
kill ‘ps | gawk ’/xeyes/ {print $1}’‘ anice <strong>Unix</strong> pipe<br />
xhost +<br />
5
6. Printing<br />
xterm -T kenny -n kenny &<br />
change <strong>to</strong> new window<br />
ssh -X yourid@kenny<br />
Password: *******<br />
export DISPLAY=3p11-10.netlab.cems.uwe.ac.uk tell kenny your screen<br />
emacs &<br />
(find . -name "fred*" -print >> ~/foundit ) >& /dev/null &<br />
background search for a file called fred-something<br />
grep -rs "strncmp" /usr/include<br />
search for a function definition in header files<br />
ypcat passwd | grep -i "williams"<br />
using the <strong>Unix</strong> NIS/yp password file, locate a student<br />
When you want <strong>to</strong> print from a Linux system on the networ k, you can uselpstat <strong>to</strong> check printer<br />
availability,lpq <strong>to</strong> check the queue length, <strong>and</strong>lp <strong>to</strong> send a file <strong>to</strong> the chosen printer. The printers owned by<br />
ITS use the Pharos billing system which requires you <strong>to</strong> pay per sheet. A document <strong>to</strong> be printed is queued<br />
at the print station until you go <strong>and</strong> specially login at the station <strong>and</strong> release the print job. Uselprm <strong>to</strong><br />
remove your job waiting on a printer’s queue.<br />
rob@kenny> lpstat -p<br />
printer bw_plain is idle. enabled since Jan 01 00:00<br />
printer col_plain is idle. enabled since Jan 01 00:00<br />
printer netlab is idle. enabled since Jan 01 00:00<br />
printer staffcol is idle. enabled since Jan 01 00:00<br />
printer staffps is idle. enabled since Jan 01 00:00<br />
rob@kenny:~$<br />
rob@kenny> lp -dnetlab world.c<br />
request id is netlab-159 (1 file(s))<br />
rob@kenny><br />
rob@kenny> lpq -Pnetlab<br />
netlab is ready <strong>and</strong> printing<br />
Rank Owner Job File(s) Total Size<br />
active rob 160 client.c 8192 bytes<br />
rob@kenny><br />
The following is a useful comm<strong>and</strong> line for printing wide, commented source code. Look up the manual page<br />
(man enscript) <strong>and</strong> find out what each of the 7 flag options achieve . Note that it should all be typed in<strong>to</strong><br />
<strong>Unix</strong> on a single line. You could use this for your programming assignment listings.<br />
enscript -dnetlab -c -r --header=’$n|%W|Page $% of $=’ -n2<br />
-Dduplex:false -fCourier10 prog.c<br />
7. Remote access<br />
Students maybeable <strong>to</strong>login <strong>to</strong> the <strong>Unix</strong> hosts or wor kstations from anywhere, through broadb<strong>and</strong> or<br />
through dial up modems. Remote sessions via the Internet are routed, for security reasons, through a firewall<br />
host. To use this facility for inward remote login, you will have <strong>to</strong> register with the Help Desk <strong>and</strong> obtain an<br />
ssh password. I login from home using the secure shell (ssh) comm<strong>and</strong>:<br />
rob> ssh r-williams@gateway.uwe.ac.uk<br />
r-williams@gateway.uwe.ac.uk’s password:<br />
Then I telnet or ssh <strong>to</strong> milly <strong>to</strong> see my files, orssh <strong>to</strong> kenny for Netlab access. You cannot achieve much on<br />
the gateway machine itself, but it does run the ftp demon, so it can act as a forwarding station for off-site file<br />
transfers.<br />
6
The utilitynslookup can be useful when you are trying <strong>to</strong> find domain names or IP numbers. Check out the<br />
manual page for nslookup, <strong>and</strong> try:nslookup yahoo.co.uk. Itcan be useful when trying <strong>to</strong> set up a<br />
session from home <strong>to</strong> know some IP numbers.<br />
yahoo.co.uk 217.12.3.11<br />
blueyonder.co.uk 62.30.31.86<br />
google.co.uk 66.249.93.104<br />
milly 164.11.11.13<br />
kenny 164.11.222.253<br />
kyle 164.11.222.164<br />
nas 164.11.8.48<br />
The two applicationstelnet <strong>and</strong>ssh provide remote login capability. But if you want <strong>to</strong> transfer files<br />
between computers there are several alter natives which can be exploited, besides the flash stick, of course.<br />
8. Flash sticks<br />
•dual login <strong>and</strong> use desk<strong>to</strong>p cut & paste facilities <strong>to</strong> copy text across<br />
•ftp or sftp (file transfer pro<strong>to</strong>col)<br />
•NFS file expor t/sharing<br />
•web browser such as IE or Firefox using http <strong>and</strong> SAVE AS the file<br />
•email an attachment <strong>to</strong> yourself<br />
To use a flash stick, CDROM or floppy inaPCrunning <strong>Unix</strong>, you have <strong>to</strong> notify the computer that a newfile<br />
system is available by using themount comm<strong>and</strong>:<br />
7
Inser t your flash stick, <strong>and</strong> use themount /media/flash comm<strong>and</strong>. On my machine the mount point is<br />
/media/DISGO due <strong>to</strong> some problems with its file system. Then inspect the flash stick direc<strong>to</strong>r y using:ls<br />
-al /media/flash. Remember <strong>to</strong>umount /media/flash before removing it from the computer. The<br />
reason you have <strong>to</strong> tell the system when you intend <strong>to</strong> withdraw the memory stick isthat often the new data<br />
is held in RAM cache, <strong>and</strong> not immediately written <strong>to</strong> the flash memory. Thus you have <strong>to</strong> flush the cache<br />
before removing the stick. Watch the flash stick LED for activity. <strong>Unix</strong> also has thesync comm<strong>and</strong> <strong>to</strong> flush<br />
all buffers before turning off the power.<br />
In large networ ks, itiscommon for data <strong>and</strong> executable binaries <strong>to</strong> be distributed amongst several hosts.<br />
This is made possible by the Networ k Filing System (nfs) provided by Sun Microsystems. This allows a user<br />
<strong>to</strong> see remote files as if they were s<strong>to</strong>red on the local hard disk. Microsoft offers a similar facility known as<br />
"shares". To get an indication of the usage of the nfs cross-mounting facility use thedf -k utility, which<br />
gives more infor mation thanmount. Below ispar t of the df -k results for my wor kstation:<br />
rwilliam@olves<strong>to</strong>n [87] df -k<br />
Filesystem kbytes used avail capacity Mounted on<br />
/dev/hda2 34177192 3261124 30916068 10% /<br />
tmpfs 254096 0 254096 0% /dev/shm<br />
/dev/hda3 8770392 4 8770388 1% /shared<br />
tmpfs 10240 700 9540 7% /dev<br />
nas:/nas 1756463104 215384496 1541078608 13% /nas<br />
/dev/hdc 620876 620876 0 100% /media/cdrom0<br />
rwilliam@olves<strong>to</strong>n [88]<br />
Youcan see mention of the partitions on the local drives hda2 <strong>and</strong> hda3, also the remote mounted nas<br />
device which expor ts its file systems <strong>to</strong> all the local computers for access. This makes them appear the same<br />
as locally s<strong>to</strong>red files. Note also the last entry which shows a removeable CD (Burks) has also been mounted<br />
for access.Inlarge sites, files are distributed across many different computers. But more <strong>and</strong> more, user<br />
data files (home direc<strong>to</strong>ries) are held on a Networ k Attached S<strong>to</strong>rage (NAS) device which efficiently<br />
manages terabytes (T, 2 40 ,or10 12 )ofs<strong>to</strong>rage.<br />
9. <strong>Unix</strong> & MS Windows-XP in P,Q&NBlock<br />
There are several distinct subnets <strong>and</strong> computing labs set up in different lab blocks. You must get used <strong>to</strong><br />
their differences <strong>and</strong> individual quirks if you want <strong>to</strong> gain the maximum benefit from your time at university.<br />
Take a stroll around the campus site <strong>to</strong> locate the different labs.<br />
The ability for <strong>Unix</strong> <strong>to</strong> h<strong>and</strong>le data for Windows, using the SMB file server program means that a single host<br />
can s<strong>to</strong>re files for both <strong>Unix</strong> <strong>and</strong> XP. Atthe moment a large ( 1.7 TB) networ k s<strong>to</strong>rage array perfor ms that<br />
function.<br />
10. X11R6, X-windows<br />
<strong>Unix</strong> originally did not have a GUI interface. Itcould only be accessed from the comm<strong>and</strong> line, through a<br />
comm<strong>and</strong> line interface (CLI), normally called the Shell. Now itisnor mal <strong>to</strong> install the X-windows suite of<br />
programs on <strong>to</strong>p of <strong>Unix</strong> <strong>to</strong> provide full WIMP/GUI facilities. Itisimpor tant <strong>to</strong> underst<strong>and</strong> that X-windows<br />
suppor ts distr ibuted processing in addition <strong>to</strong> a graphical display facility.<br />
If when you login, <strong>Unix</strong> does not au<strong>to</strong>matically evoke the X11 GUI, you can often start itmanually with:<br />
startx.<br />
Nowadays, without X-windows, <strong>Unix</strong> looks ver y quiet <strong>and</strong> unexciting. This is the same situation you find when<br />
running a MicroSoft comm<strong>and</strong> prompt (C>) orDOS session. Occasionally you may have <strong>to</strong>log in<strong>to</strong> "vanilla"<br />
version of <strong>Unix</strong>. On Linux this is possible using the F1-F7 keys with [CNTL][ALT], but only one of these<br />
sessions can run X11, this is usually on F7. Try[CNTL][ALT]F2. Login <strong>to</strong> a parallel session <strong>and</strong> checkon<br />
your processes. You should be able <strong>to</strong> see processes from the previous processes. Logout <strong>and</strong> hit<br />
[CNTL][ALT]F7 <strong>to</strong> return <strong>to</strong>the X11 session. X-windows often involves 3 separate processes: an X Client<br />
application, a Screen Server, <strong>and</strong> X-window Manager. The client application is the user program that wants<br />
<strong>to</strong> displaysomething. The Screen Server runs the .... screen, rendering the display correctly under the<br />
control of X pro<strong>to</strong>col packets. Finally, the X-window Manager organises multiple window sessions on a single<br />
screen, taking events <strong>and</strong> directing them <strong>to</strong> the correct client processes. There are several alter native<br />
8
managers: twm, olwm, kwin,<br />
Pr int Ser ver<br />
client<br />
application<br />
Window<br />
manager<br />
Screen Server<br />
X-windows Client-Server couplets wor king across a networ k<br />
Note that the Client <strong>and</strong> Manager proceses do not need <strong>to</strong> be running on the local machine. Infact, it is<br />
common <strong>to</strong> distribute X applications around the networ k, in order <strong>to</strong> exploit the available processing <strong>and</strong><br />
s<strong>to</strong>rage facilities. With such a powerful <strong>and</strong> flexible system, there is a real danger of unwanted data arriving<br />
on your screen. The first level defence is <strong>to</strong> s<strong>to</strong>p all "foreign" hosts from sending data <strong>to</strong> your screen:<br />
$xhost -<br />
This s<strong>to</strong>ps all the fun! So normally you would open up <strong>to</strong> trusted remote machines or friends:<br />
$xhost +kenny +rwilliam +164.11.222.164<br />
With this arrangement, new windows can be opened on your machine from anyone running on kenny orkyle,<br />
or rwilliam from any machine.<br />
If you are running a client X application (in fact practically any <strong>Unix</strong> program) <strong>and</strong> wish <strong>to</strong> display remotely,<br />
the client process has <strong>to</strong> send X data acros the networ k <strong>to</strong> the selected target screen. This can be done be<br />
setting theDISPLAY environment var iable on the client machine:<br />
$export DISPLAY=target_machine:0.0<br />
The term target_machine can be either the IP or the domain name of the machine This will of course mean<br />
that all o/p will get redirected <strong>to</strong>the same remote machine, soanalter native is<strong>to</strong>use an X comm<strong>and</strong> line<br />
parameter when starting the application:<br />
$xeyes -display 164.11.253.36:0.0<br />
Following this introduction <strong>to</strong> parameters for X applications, there is also font control.<br />
$emacs -font -*-helvetica-*-r-*-*-*-120-*-*-*-*-*-* &<br />
The font name is <strong>to</strong>o complex <strong>to</strong>type in, even though only 3 of the fields are necessary. Use the font browser<br />
xfontsel <strong>to</strong> view the available fonts, copy the name specifier using the [select] but<strong>to</strong>n, <strong>and</strong> paste it back on<strong>to</strong><br />
the comm<strong>and</strong> line using the middle mouse but<strong>to</strong>n.<br />
$xfontsel &<br />
9
11. KDE desk<strong>to</strong>p environment<br />
The K Desk<strong>to</strong>p Environment, usually abbreviated <strong>to</strong> KDE, is one of several graphical desk<strong>to</strong>ps for Linux. The<br />
main alternative isGnome. Generally, desk<strong>to</strong>p GUIs offer everything you need <strong>to</strong> wor k with on a daily<br />
basis.But occasionally you still need <strong>to</strong> use the comm<strong>and</strong> line <strong>to</strong> obtain the required facility. The typical KDE<br />
desk<strong>to</strong>p consists of several par ts: Apanel at the bot<strong>to</strong>m of the screen, used <strong>to</strong> start applications <strong>and</strong> switch<br />
between desk<strong>to</strong>ps. Itcontains the K menu, a large icon which displays a menu ofapplications which start<br />
when LMB clicked. A taskbar, bydefault running across the bot<strong>to</strong>m of the screen, is used <strong>to</strong> manage<br />
currently running applications. Click onanapplication on the taskbar <strong>to</strong> switch <strong>to</strong> the application. The<br />
desk<strong>to</strong>p itself, can display icons for frequently used applications. KDE provides multiple desk<strong>to</strong>ps, each of<br />
which has its own windows. Click onthe numbered but<strong>to</strong>ns on the panel <strong>to</strong> switch between desk<strong>to</strong>ps.<br />
Applications can be started by:<br />
Selecting a desk<strong>to</strong>p icon,<br />
Selecting the name from the main KDE menu (bot<strong>to</strong>n left corner),<br />
Typing the name in<strong>to</strong> a comm<strong>and</strong> window, such as konsole or xterm.<br />
Typing the name in<strong>to</strong> the Tool Bar Application Launcher window,<br />
RMB click ondesk<strong>to</strong>p, select Run.<br />
KDE is constructed using the Qt X-windows widget librar y, <strong>and</strong> comes with many useful X applications, such<br />
as the browser Konqueror, Konsole terminal, Kpackage package manager <strong>and</strong> many more. Anon-line help<br />
system is available from the <strong>to</strong>olbar as a life belt icon. This shows the KDE help files as well as the normal<br />
UNIX man pages. The Linux HOWTOs are also available on kenny at/usr/share/doc.<br />
12. <strong>Unix</strong> BASH shell<br />
A<strong>Unix</strong> shell, such as bash, sh, csh, ksh or tcsh, is a program which moni<strong>to</strong>rs the comm<strong>and</strong> line keyboard<br />
input, interprets the instructions <strong>and</strong> outputs results <strong>to</strong> the screen. It runs when you start acomm<strong>and</strong><br />
window (konsole or xterm). Because everybody’s prompt is different in this sheet we will try <strong>to</strong>use the old $<br />
sign as the <strong>Unix</strong> prompt. Note that you can change your line prompt if you want <strong>to</strong>, when using the bash<br />
shell:<br />
$<br />
$ export PS1="hi> "<br />
hi ><br />
The user interface program, or Comm<strong>and</strong> Line Interface (CLI) isknown as the shell. There are several<br />
alter native shells that the user can choose from:<br />
sh original Bourne shell, written by Steve Bour ne<br />
csh C shell written by Steve Joy<br />
ksh Kor n shell, often found on HP equipment<br />
tcsh tennex shell, my favour ite<br />
bash born again shell, used with Linux<br />
10
Just type inksh orbash <strong>to</strong> swap <strong>to</strong>another shell. You can return <strong>to</strong>the previous shell withexit. The<br />
bash shell is often found running on Linux <strong>and</strong> is like the old Bourne shell. It does things a bit differently <strong>to</strong><br />
the csh, so <strong>to</strong> change your bash screen prompt you need <strong>to</strong> type:PS1="here> ". Onthe ksh the same<br />
would be You may find a short prompt is preferable.<br />
Some shells offer helpful facilities for users, such as au<strong>to</strong> completion, comm<strong>and</strong> line editing <strong>and</strong><br />
comm<strong>and</strong> line his<strong>to</strong>ry. Iuse bash, tsh or ksh <strong>to</strong> get comm<strong>and</strong> line editing in the style of the emacs edi<strong>to</strong>r.<br />
his<strong>to</strong>r y au<strong>to</strong> editing<br />
list previous next completion<br />
bash his<strong>to</strong>ry ˆP ˆN TAB emacs<br />
tcsh his<strong>to</strong>ry ˆP ˆN TAB emacs<br />
csh his<strong>to</strong>ry !! TAB ed<br />
!-1 !emac<br />
!42<br />
!mkd<br />
sh TAB none<br />
ksh fc -l r<br />
his<strong>to</strong>r y fc -e emacs 1<br />
ksh -o emacs his<strong>to</strong>r y ˆP ˆN TAB(Linux) emacs<br />
The character erase key can sometimes get lost. It can often be bound <strong>to</strong> either [DEL} or [BS}, you can set<br />
erase <strong>to</strong> whatever you want:<br />
$ tset -e[BS]<br />
$erase set <strong>to</strong> Cntrl-H<br />
$<br />
Another feature of <strong>Unix</strong> is the PA TH. This "environment var iable" holds a list of direc<strong>to</strong>ries where<br />
programmes can be found.<br />
rob@kenny> printenv PATH<br />
/usr/local/bin:/usr/bin:/bin:/usr/X11R6/bin:/usr/games:/usr/local/<br />
jdk1.3.1_01/bin:/usr/local/mysql/bin:/usr/local/samba/bin:.:/opt/<br />
gnome/bin:/usr/share/texmf/bin:/usr/openwin/bin<br />
Adding another bin location <strong>to</strong> the PATHlist:<br />
rob@kenny> export PATH=${PATH}:/home/netlab/rob/bin<br />
rob@kenny> printenv PATH<br />
/usr/local/bin:/usr/bin:/bin:/usr/X11R6/bin:/usr/games:/usr/local/<br />
jdk1.3.1_01/bin:/usr/local/mysql/bin:/usr/local/samba/bin:.:/opt/<br />
gnome/bin:/usr/share/texmf/bin:/usr/openwin/bin:/home/netlab/rob/bin<br />
If you try<strong>to</strong>run a program <strong>and</strong> <strong>Unix</strong> gives the error "not found", it might mean that the program iss<strong>to</strong>red in a<br />
direc<strong>to</strong>r y which is not mentioned in the current PATHlist. If you already know where the executable is s<strong>to</strong>red<br />
on disk you can simply sort i<strong>to</strong>ut by typing in the full pathname, such as/usr/sbin/ping, oradding the<br />
direc<strong>to</strong>r y <strong>to</strong> your PATHlist,setenv PATH=${PATH}:/usr/sbin, Ifhow ever you have no idea where in the<br />
CEMS NFS networ k the code might reside - you have a bit of a problem! Removing an entry from the PATH<br />
is a bit more sophisticated, involving comm<strong>and</strong> piping <strong>and</strong> substitution which we will encounter again, later in<br />
this wor ksheet:<br />
$ printenv PATH<br />
/usr/bin:/bin:/usr/bin:/usr/local/bin:/usr/X11R6/bin/:/usr/games:/home/rob/bi<br />
$ export DISPLAY=‘echo $PATH | sed ’s#/usr/games:##g’‘<br />
$ printenv PATH<br />
/usr/bin:/bin:/usr/bin:/usr/local/bin:/usr/X11R6/bin/:/home/rob/bin:.<br />
Or you could just use the comm<strong>and</strong> line editing facilities <strong>to</strong> achieve the same amendment.<br />
11
At <strong>Unix</strong> log in, you used always <strong>to</strong>get an American joke, or "fortune cookie", but unfor tunately solemn Sun<br />
have removed this important facility from their Solaris distribution. They probably think that jokes are<br />
inappropr iate for software professionals <strong>and</strong> not wor th the risk of litigation should someone take offence.<br />
An important feature of all shells, including BASH, is their capacity <strong>to</strong> h<strong>and</strong>le short programs or scripts. This<br />
allows you <strong>to</strong> record instructions in a file <strong>and</strong> play them later; agreat asset for systems adminstra<strong>to</strong>rs. There<br />
are many uses for this which you will discover. Here is an example of searching for another PC which has<br />
been powered up on the LAN:<br />
$ hostname -i<br />
16.11.222.253<br />
$<br />
$ for ((i=1; i do<br />
> ping -c1 164.11.222.$i | grep "64 bytes from 164.11.222.$i"<br />
> done<br />
64 bytes from 164.11.222.11: icmp_seq=1 ttl=255 time=4.02 ms<br />
64 bytes from 164.11.222.12: icmp_seq=1 ttl=255 time=4.12 ms<br />
64 bytes from 164.11.222.13: icmp_seq=1 ttl=255 time=4.08 ms<br />
64 bytes from 164.11.222.33: icmp_seq=1 ttl=128 time=0.194 ms<br />
64 bytes from 164.11.222.36: icmp_seq=1 ttl=128 time=0.124 ms<br />
64 bytes from 164.11.222.100: icmp_seq=1 ttl=64 time=6.01 ms<br />
64 bytes from 164.11.222.164: icmp_seq=1 ttl=64 time=0.123 ms<br />
64 bytes from 164.11.222.166: icmp_seq=1 ttl=64 time=0.185 ms<br />
64 bytes from 164.11.222.200: icmp_seq=1 ttl=64 time=3.01 ms<br />
$<br />
The whole script can be recalled with a [CNTL P] <strong>and</strong> will re appear as<br />
$for ((i=10; i
13. <strong>Unix</strong> HELP facilities<br />
The traditional source of online infor mation<br />
for all <strong>Unix</strong> systems is the collection of<br />
manual pages. These are no<strong>to</strong>riously<br />
daunting for beginners. Try typingman<br />
mkdir for infor mation about how <strong>to</strong>make<br />
anew direc<strong>to</strong>r y. Ifyou only have a "subject"<br />
<strong>and</strong> need <strong>to</strong> locate relevant man pages you<br />
can use the keyword search:<br />
man -k subject.<br />
In fact, most programmers rarely read all<br />
the words in a man page, only scanning<br />
through for example code fragments.<br />
Occasionally however you do need <strong>to</strong><br />
spend time <strong>and</strong> read the obscure text,<br />
especially with reference <strong>to</strong> control flags<br />
<strong>and</strong> direc<strong>to</strong>ry names.<br />
Sun, <strong>to</strong> their credit, offer the Answer Books which are an excellent source of online infor mation about <strong>Unix</strong>,<br />
Solar is in particular. The Linux Documentation Project (TLDP) has a wonderful set of useful manuals <strong>and</strong><br />
also it maintains a set of shorter, practical notes called HOWTOs:<br />
or<br />
http://www.tldp.org/HOWTO/<br />
http://www.linuxhow<strong>to</strong>s.org<br />
The Student Help Desk may provide students with introduc<strong>to</strong>ry help sheets about a var iety of software,<br />
including <strong>Unix</strong> <strong>and</strong> PC <strong>to</strong>pics.<br />
The main source of up-<strong>to</strong>-date infor mation is the WWW. Computing students do spend a lot of time using<br />
Google,browsing for sites offer ing useful infor mation. Big companies, such as Intel, Microsoft, IBM <strong>and</strong> HP<br />
take some trouble <strong>to</strong> support their own products, but also offer general guides. Many universities, especially<br />
in the States are free with their course material. Try these now:<br />
http://www.ee.surrey.ac.uk/Teaching/<strong>Unix</strong>, from Surrey Uni.<br />
http://www.reading.ac.uk/ITS/Topic/<strong>Unix</strong>OS/UnSIntro01/, from Reading University<br />
http://8help.osu.edu/wks/unix_course/intro-1.html, from Ohio State Uni.<br />
http://par tmaps.org/era/unix/shell.html, focuses on the shell<br />
http://www-128.ibm.com/developerwor ks/linux/librar y/l-kdei, intro <strong>to</strong> KDE<br />
intro2unix.ps Fiamingo, DeBula & Condron, from<br />
ftp://www-wks.uts.ohio-state.edu/unix_course/<br />
(Be careful when using web material in your assignments. Read the guidelines on how <strong>to</strong>avoid the<br />
accusation of plagerism (copying))<br />
Sun additionally offer a set of online Help H<strong>and</strong>books. Click RMB (right mouse but<strong>to</strong>n) on the desk<strong>to</strong>p<br />
background <strong>and</strong> selectHelp<br />
13
But there is no substitute for a good text book when you are struggling <strong>to</strong> underst<strong>and</strong> <strong>and</strong> use new<br />
comm<strong>and</strong>s.Sodoget one as soon as possible.<br />
My personal favour ite is Paul Wang, but this currently out of print> Any suggestions for a decent substitute<br />
would be welcome.<br />
An <strong>Introduction</strong> <strong>to</strong> Berkeley <strong>Unix</strong>, Paul Wang, Wadsworth,<br />
Introducing <strong>Unix</strong> <strong>and</strong> Linux, Mike Joy, Stephen Jarvis, Michael Luck, Palgrave Books,<br />
Linux & <strong>Unix</strong> Programming Tools: a Primer, SSarwar, KAl-Saqabi Addison Wesley<br />
This LAST text at one time included 2 CDs with Linux M<strong>and</strong>rake 8.2. I do not know ifthis arrangement<br />
continues.<br />
What you need is an approachable text, not <strong>to</strong>o scary for beginners, but with sufficient infor mation <strong>and</strong><br />
technical detail <strong>to</strong> last the course.<br />
As a <strong>Unix</strong> beginner you may get in<strong>to</strong> difficulty, try the following sources of help:<br />
1. a friend who knows a bit more than you,<br />
2. Google for relevant advice,<br />
3. your lab course tu<strong>to</strong>r,<br />
4. a <strong>Unix</strong> student text book, essential purchase!<br />
5. online Help pages, from the root menu.<br />
6. the Computer Officers who lovingly tend the <strong>Unix</strong> networ k,<br />
7. the online <strong>Unix</strong> manual facility: man .....<br />
Forabit of his<strong>to</strong>ry you can browse the following sites:<br />
14
http://www.computinghis<strong>to</strong>r ymuseum.org/teaching/papers/research/<br />
http://www.bell-labs.com/his<strong>to</strong>r y/unix/<br />
http://www.levenez.com/unix/<br />
http://www.unix-systems.org/what_is_unix/his<strong>to</strong>r y_timeline.html<br />
14. Using Windows-XP <strong>to</strong> access <strong>Unix</strong><br />
1. Log in<strong>to</strong> a Windows-XP PC , start upacomm<strong>and</strong> prompt windows, displaying C> or similar. Then type in<br />
telnet orssh <strong>and</strong> the IP number of your local <strong>Unix</strong> server.<br />
2. A better alternative is<strong>to</strong>use the Xceed application. If you want <strong>to</strong> get through <strong>to</strong> <strong>Unix</strong> from a Windows PC,<br />
you may be able <strong>to</strong>run Xceed. Xceed offers full X-Window facilities, while telnet is limited <strong>to</strong> a simple<br />
comm<strong>and</strong> line interface. You will then have <strong>to</strong> use your <strong>Unix</strong> id <strong>and</strong> password <strong>to</strong> gain access <strong>to</strong> the <strong>Unix</strong><br />
ser ver.When this happens you may concurrently run XP-windows side by side with <strong>Unix</strong> sessions. This can<br />
be confusing, with the local XP session running processes actually on the PC, while the X-window isonly<br />
displaying data, passed through the networ k from the <strong>Unix</strong> host which is actually running the process.<br />
3. A more sophisticated alternative is<strong>to</strong>install Redhat Cygwin software on the Windows-XP machine. This<br />
provides a <strong>Unix</strong> emulation on<strong>to</strong>p of Windows, allowing <strong>Unix</strong> applications <strong>to</strong> run, including those requiring Xwindows.<br />
15
15. X Applications<br />
The X11R6 windowing system is a ver y complex arrangement. A ver y clear introduction is available in the<br />
Wikipaedia site:<br />
http://en.wikibooks.org/wiki/Guide_<strong>to</strong>_X11/<strong>Introduction</strong><br />
If the application program isspecifically written for X it could setup a new window onyour display. An<br />
advantage of a windowing system is the possibility of viewing output from several programs simultaneously,<br />
<strong>and</strong> copying text between the many windows.<br />
Cut & Paste between Windows The mouse allows you <strong>to</strong> copy text from window <strong>to</strong>window<br />
without retyping. Drag the cursor across the text that you wish <strong>to</strong> copy with the LMB<br />
held down. Release LMB. Position the mouse pointer at target location <strong>and</strong> click CMB <strong>to</strong><br />
paste in the text. This technique can be ver y useful in many situations, especially when<br />
you need <strong>to</strong> kill a process:<br />
Look in /usr/games. Try running /usr/games/kbounce &. You may position this by moving the pointer <strong>and</strong><br />
pressing the LMB once. Ifyou wish <strong>to</strong> use the original xterm window again you must start the Xapplication in<br />
the background by typing an & at the end of the comm<strong>and</strong> before hitting [CR].<br />
$ls /usr/games<br />
atlantik gnect gnotravex kbackgammon kgoldrunner kolf kshisen ktron<br />
banner gnibbles gnotski kbattleship kjumpingcube konquest ksirtet ktuberling<br />
blackjack gnobots2 gtali kblackbox klickety kpat ksmiletris kwin4<br />
fortune gnome-s<strong>to</strong>nes iagno kbounce klines kpoker ksnake kwin4proc<br />
gataxx gnometris kasteroids kenolaba kmahjongg kreversi ksokoban lskat<br />
glines gnomine ka<strong>to</strong>mic kfouleggs kmines ksame kspaceduel lskatproc<br />
$<br />
$ /usr/games/atlantik &<br />
$<br />
Youcan add the direc<strong>to</strong>ry /usr/openwin/demo <strong>to</strong> your PATH<strong>and</strong> then only need <strong>to</strong> type in the name of the<br />
program, <strong>and</strong> not its full path:<br />
$ xeyes&<br />
xe y es: comm<strong>and</strong> not found<br />
$<br />
$ setenvPATH/usr/openwin/demo:{$PATH}<br />
$ xeyes&<br />
$<br />
If everything goes pear-shaped, <strong>and</strong> you want <strong>to</strong> start again, first kill off all your processes by clicking on the<br />
console window <strong>and</strong> typing: kill -9 -1, (minus nine minus one) <strong>and</strong> st<strong>and</strong>ing back aseverything rapidly dies.<br />
Youwill need <strong>to</strong> login again after such a drastic retreat.<br />
Another direc<strong>to</strong>ry with X applications is /usr/bin/X11. This could also be added <strong>to</strong> your PATHlist. Type in<br />
Becho $PATH <strong>and</strong> see. Some applications are available from the desk<strong>to</strong>p by pressing RMB on the root<br />
window (background). The resulting menu offers further option categories: Programs, Graphics, Inter net,<br />
Packages, Languages. Look through the var ious alter natives. The web browser Netscape is a good place <strong>to</strong><br />
star t.<br />
16
Tr y some more X applications which are in /usr/bin/X11 or /usr/openwin/demo:<br />
xlogo &, <strong>to</strong>tally useless<br />
xe y es &, quite fun for 3 minutes<br />
xbiff &, useful<br />
hexcalc &, you thought you had escaped from hex!<br />
psycho &, desperate demonstration for salesmen<br />
xfontsel &, useful Xfont browser<br />
worm &, horr id<br />
xfig &, you need <strong>to</strong> study for this<br />
xedit &, Istill prefer emacs<br />
xloadimage, nice <strong>to</strong> see some high class images, look in /pub/gifs/....<br />
xmh &, mail h<strong>and</strong>ling prog<br />
xload &, keep a watch on the ethernet<br />
xman &, manual pages browser utility, could be useful<br />
roids &, shoot cosmic rocks before they collide with your space ship<br />
puzzle &, saves all those little bits of yellow not-quite-sliding plastic<br />
xtrek &, dubious benefit <strong>to</strong> mankind<br />
xkill, kills off x applications!<br />
rob@milly [46] ps -FA | grep rob<br />
rob 9713 1 0 Feb 17 ?4:07emacs -fn fixed -geometry 79x26+0+0<br />
rob 10991 8324 0 11:17:36 pts/110:14ghostview /tmp/rob.ps<br />
rob 15241 10991 017:54:42 pts/110:03gs -sDEVICE=x11 -dNOPAUSE -dQUIET -dSAFER -<br />
rob 9810 9713 0 Feb 17 ?0:00/usr/local/bin/ispell -a -m -B<br />
rob 8323 9160 008:29:47 ?0:09xterm<br />
rob 9160 9158 0 Feb 17 pts/00:01-tcsh<br />
rob 8321 9160 008:29:39 pts/00:04twm<br />
rob 8324 8323 008:29:56 pts/110:01tcsh<br />
rob 13970 1 0 Feb 17 ?0:15xbiff<br />
rob 15296 8324 1 18:02:18 pts/110:00grep rob<br />
$ kill 13970<br />
The process number (PID) can be wiped <strong>and</strong> pasted in<strong>to</strong> position after the kill comm<strong>and</strong> <strong>to</strong> avoid typing in<br />
the number.<br />
$ ls<br />
prac1.pasprac2.pas<br />
$ pc pract1.pas<br />
$ ls<br />
prac1.pasprac2.pasa.out<br />
$ lpr -Pfx prac1.pas<br />
$ lpq -Pfx<br />
no entries<br />
$<br />
lprm - This removes all your print jobs from the queue if you decide <strong>to</strong><br />
save a few branches for later. nb: the negative sign / hyphen.<br />
mail Mail is a ver y useful <strong>Unix</strong> facility <strong>to</strong> send <strong>and</strong> receive messages, known as<br />
e-mail, throughout the networ k, or wor ld. At UWE an alternative mail system is<br />
used called simeon.<br />
cd direc<strong>to</strong>ry_path Change direc<strong>to</strong>ry allows you <strong>to</strong> move around the file<br />
system which is organized <strong>to</strong> look like the roots of a tree.<br />
cd / puts you at the ver y <strong>to</strong>p of the hierarchy, use ls <strong>to</strong> see.<br />
cd puts you back home again.<br />
17
cd .. moves you upwards <strong>to</strong>wards / (the file system root)<br />
Note that the tilde ~ character st<strong>and</strong>s for your home direc<strong>to</strong>ry, <strong>and</strong> if you want <strong>to</strong> refer <strong>to</strong> a friend’s home<br />
direc<strong>to</strong>r y you can prepend the tilde character <strong>to</strong> their login id:~j2smith<br />
16. Writing C Programs 0n <strong>Unix</strong><br />
To create a program you need an edi<strong>to</strong>r <strong>and</strong> a compiler. Use emacs as the edi<strong>to</strong>r <strong>and</strong> cc as the compiler.Fire<br />
up the edi<strong>to</strong>r, either from the desk-<strong>to</strong>p menu bytypingemacs on a shell comm<strong>and</strong> line within an xterm<br />
window. (If you find emacs <strong>to</strong>o scary/complex, Sun offer the alternative ofasimple text edi<strong>to</strong>r from the desk<strong>to</strong>p<br />
menu)<br />
cc first.c -o first This compiles a c program s<strong>to</strong>red in the file first.c <strong>and</strong><br />
produces an output file called first in your current direc<strong>to</strong>ry. Ifyou do not<br />
put in the -o first option, the output file will be named a.out by default.<br />
Star t up emacs, ifitisnot already running, <strong>and</strong> try atraditional first<br />
program inthe C language:<br />
main()<br />
{<br />
}<br />
printf("Hello world ! \n");<br />
** Emacs: wor ld.c<br />
The emacs comm<strong>and</strong>s which you need are:<br />
The <strong>Unix</strong> comm<strong>and</strong>s which you need are:<br />
ˆXˆW first.csaves emacs buffer in<strong>to</strong> a disc file called first.c<br />
ˆXˆC exits from emacs back <strong>to</strong><strong>Unix</strong> comm<strong>and</strong> level<br />
$ gcc first.c -o first compiles the C source file<br />
$ first runs the translated version of your program<br />
Av oid thea.out disaster by always using the friendly: -o<br />
There is a ver y good on-line web-based C tu<strong>to</strong>rial offered by Brian Brown.<br />
Youcan down-load it yourself or access a local copy at:<br />
http://www.cems.uwe.ac.uk/~irjohnso/coursenotes/uqc146/cprogram/<br />
18
If you have nev er used EMACS, aset of self teaching tu<strong>to</strong>rials is provided, get in<strong>to</strong> emacs <strong>and</strong> type: esc X<br />
help-with-tu<strong>to</strong>r ial<br />
To enter a program inUNIX use the EMACS edi<strong>to</strong>r <strong>and</strong> then use the appropriate compiler <strong>to</strong> translate the<br />
source code in<strong>to</strong> machine executable for mat ready <strong>to</strong> run.<br />
Cisevoked with cc ..... (the ..... is where the file name goes)<br />
or gcc ....<br />
Here is a C sorting program <strong>to</strong>try out. Note that it uses a function calledbsort which uses a librar y function<br />
calledstrcmp(). What do you think bsort does? What then is strncmp()? Use the man pages <strong>to</strong> help you.<br />
Be careful how you name your sort program. What if you unfor tunately happen <strong>to</strong> call it "sort"? Try typing<br />
sort on the comm<strong>and</strong> line before you compile your program. Get it? <strong>Unix</strong> already has a program called sort!<br />
So beware.Usewhich sort <strong>to</strong> find out which version of sort isbeing chosen <strong>to</strong> run.<br />
#include <br />
int bsort(char* pc[ ], int n ) {<br />
int gap, i, j;<br />
char* pctemp;<br />
for (gap = n/2; gap > 0; gap /= 2)<br />
for (i = gap; i < n; i++)<br />
for(j = i-gap; j>= 0; j -= gap) {<br />
if (strcmp(pc[j], pc[j+gap])
17. Web page<br />
First make sure that you have a subdirec<strong>to</strong>r y called public_html in your home direc<strong>to</strong>ry. Ifnot, insert one with:<br />
makdir ~/public_html. Then change the access permissions:chmod 755 ~/public_html.<br />
At this point you can take acopy ofsome valid html <strong>to</strong> get your home page started. Try using this framework:<br />
<br />
My personal page<br />
<br />
<br />
My Personal web page<br />
<br />
<br />
Stuff about me<br />
<br />
Or get this one in a web browser :<br />
http://www.cems.uwe.ac.uk/~cduffy<br />
Now select [View] -> [Document source] <strong>and</strong> you will see the html source code which the browser interprets<br />
<strong>to</strong> generate the previous screen. Edit the html for your own use <strong>and</strong> save it asmy_page.html in the<br />
public_html subdirec<strong>to</strong>ry inyour home direc<strong>to</strong>ry. Then make sure that the file permissions are set for others<br />
<strong>to</strong> READ-ONLY, chmod 644. Now check that it renders successfully in a web browser. The URL will be:<br />
http://kenny/~your_login_id<br />
20
This page will not yet be available for viewing outside the UWE domain.<br />
<br />
<br />
Craig Duffy’s home page <br />
<br />
<br />
Craig Duffy’s Home Page<br />
<br />
<br />
<br />
<br />
Send email <strong>to</strong> me.<br />
My machine is: staff<br />
<br />
<br />
<br />
<br />
Course h<strong>and</strong>outs <strong>and</strong> details<br />
Application Programming in Visual C++ Assignment 2 Computer <strong>Networks</strong> <strong>and</strong> Operating Systems UQC109S2 Embedded Systems Programming year 2 UQC113S2 Advanced Operating Systems Programming UQC152H3 Real time <strong>and</strong> Embedded Systems Programming Final year UQC122S3 Embedded Control Systems Programming Masters UEE072HM <strong>Introduction</strong> <strong>to</strong> Operating Systems UQC155S2 Application Programming in C++ UQC157S3 Software Design <strong>and</strong> C++ UFS003C2 System On Chip course Individual project (Computing) UQC120D3 ****** Project Viva Timetable June 1-2 2006 ******
Some More Readings:<br />
’Essential EMACS’ help sheet is available, followed bythe more detailed GNU emacs manual.<br />
Another lengthy wor ksheet on using EMACS is also available.<br />
There are many brilliant books on <strong>Unix</strong> for students <strong>and</strong> exper ts, you must get one as<br />
soon as possible <strong>to</strong> help you through this course. Try either of the following:<br />
’An <strong>Introduction</strong> <strong>to</strong> <strong>Unix</strong>’ by Duffy C. Char twell Bratt, 2nd Ed<br />
’An <strong>Introduction</strong> <strong>to</strong> Berkeley <strong>Unix</strong>’ by Wang P. Wadsworth<br />
’Getting Started with UNIX <strong>and</strong> X’ by Andreasson T. &Skansholm J. Addison-Wesley, 1993<br />
22
THE ESSENTIAL EMACS<br />
To enter EMACS (gmacs) screen edi<strong>to</strong>r type: emacs<br />
When using X windows type: emacs &<br />
NOTES: i) The CONTROL key is represented by ˆ,use like the shift key<br />
ii) The ESCAPE key is represented by {ESC}.<br />
The ESCAPE key must be released before the comm<strong>and</strong> character is pressed.<br />
iii) The BACKSPACE key is represented by {bs}.<br />
------------------------------------------------------------------------------<br />
Ba ckwar ds Forwa r ds<br />
ˆB Char ˆF<br />
MO VE: {ESC} B Word {ESC } F cur sor moves on same l ine<br />
ˆA Line ˆE<br />
Upwar ds Dow n wa rds<br />
ˆP Line ˆN cur sor moves <strong>to</strong> new l ine<br />
{ESC }V Screen ˆV cur sor moves <strong>to</strong> new screen<br />
{ESC } < File {ESC } > cur sor moves <strong>to</strong> file end<br />
-----------------------------------------------------------------------------<br />
Ba ckwar ds Forwa r ds<br />
{bs} Char ˆD del ete cha rac ter<br />
DE L ETE : {ESC } {bs} Word {ESC }D del ete wor d<br />
Line ˆK del ete <strong>to</strong> end of l ine<br />
Block ˆ@ . .ˆWmar k star t of block wi th ˆ@or ˆsp<br />
mo ve the cur sor <strong>to</strong> block end ,<br />
de l et e bl ock wi th ˆW<br />
-----------------------------------------------------------------------------<br />
YA N KBACK : ˆY res <strong>to</strong>r eswor d/l ine /bl ock<br />
pr eviou s ly del eted<br />
{esc }Y rol ls bac k through yan k queue<br />
-----------------------------------------------------------------------------<br />
FI LEHANDL ING :<br />
ˆXˆW . ..filename . . :file you r text inaname d di sc file<br />
ˆXˆF . ..filename . . :ge t aname d file int o EMA CS for edi t ing<br />
ˆXˆS :save you r fileont o di sc <strong>and</strong> con t inue ed iting<br />
ˆX I ...filename . . : inse r t ano the r di sc file at cur sor pos i tion<br />
-----------------------------------------------------------------------------<br />
ON L INE HELP :<br />
ˆH ˆH :hel p al ter nat ive s , ˆG <strong>to</strong> ret urn<br />
------------------------------------------------------------------------------<br />
UN I XTEMP ORARYESCA P E fo r non -X peop l e:<br />
ˆX C or ˆZ :temp o ra r ily drops out of EMA CS int o anew she l l,<br />
re tur n wi th ˆDor fg, used when comp i ling ,<br />
------------------------------------------------------------------------------<br />
ASSOR TED :<br />
ˆG :abo r t the cur ren t comm <strong>and</strong><br />
ˆL :re fresh the screen<br />
ˆX2 :sp l it screen i nt o two windows ,<br />
comm u te betwe e n wi ndows with ˆXO (ot her )<br />
{ESC } Xshe l l :conver ts the window int o a comma n d shel l ,<br />
ve r y use ful !<br />
{ESC } Xaut o-fi l l :se t wp l inewrapp i ng<br />
{ESC } 75 ˆX f :se t righ t ma r gi n <strong>to</strong> col umn 75<br />
------------------------------------------------------------------------------<br />
EX I T:<br />
ˆXˆC :ex i t fromEMA CS<br />
------------------------------------------------------------------------------<br />
23
ON-LINE UNIX MANUAL PAGES.<br />
Use the man comm<strong>and</strong> <strong>to</strong> get infor mation on UNIX things:<br />
$man pc<br />
$man man what?????<br />
$man sort<br />
sor t(1) sor t(1)<br />
NAME<br />
sor t -sor t files<br />
SYNTAX<br />
sor t [options] [+pos1 [-pos2]]....[-o output] [-T direc<strong>to</strong>ry]<br />
[file...]<br />
OPTIONS<br />
The default is <strong>to</strong> sort anentire line. When more than one<br />
key is specified, sort executes the keys inthe order they<br />
are given.<br />
-b ignores leading blanks, spaces, <strong>and</strong> tabs in field<br />
compar isons. +pos1 should be specified with the -b<br />
option.<br />
-c checks if the input file is sorted according <strong>to</strong> the<br />
order ing rules. This does not produce any output<br />
unless the file is out of sort.<br />
-d specifies only letters, digits <strong>and</strong> blanks are <strong>to</strong> be<br />
significant.<br />
-f folds upper case letters on<strong>to</strong> lower case.<br />
-i ignores the characters outside the ASCII range<br />
040-0176 in nonnumer ic compar isons.<br />
24
THE ESSENTIAL Vi<br />
To enter the vi screen edi<strong>to</strong>r, go<strong>to</strong>anxter m window <strong>and</strong> type: vi<br />
NOTES: i) The CONTROL key is represented by ˆ,use like the shift key<br />
ii) The ESCAPE key is represented by {ESC}.<br />
The ESCAPE key must be released before the comm<strong>and</strong> character is pressed.<br />
iii) The BACKSPACE key is represented by {bs}.<br />
The vi text edi<strong>to</strong>r has two modes. Itcan either be in text insert or comm<strong>and</strong> mode. Note that vi puts tilde<br />
characters down the lefth<strong>and</strong> side of the test window <strong>to</strong>mar k the position of empty lines in the text buffer.<br />
When vi starts up it is in Comm<strong>and</strong> Mode, soyou need <strong>to</strong> just pressibefore entering text.<br />
If you want <strong>to</strong> append text <strong>to</strong> an existing buffer, useainstead ofibefore entering text.<br />
Te xt<br />
inser t<br />
mode<br />
esc<br />
i<br />
Comm<strong>and</strong><br />
mode<br />
Yo u stee r the cur sor abou t in Comma n d mo d e by key i ng one of sev era l spec i al cha r s:<br />
------------------------------------------------------------------------------<br />
Ba ckwar ds Forwa r ds<br />
h Char l or use arrow key s<br />
MO VE: e Word b cur sor moves on same l ine<br />
Upwar ds Dow n wa rds<br />
k Line j or use arrow key s<br />
-----------------------------------------------------------------------------<br />
Ba ckwar ds Forwa r ds<br />
x Char de l et e charac ter<br />
DE L ETE : Word dw del ete wor d<br />
Line dd de lete cur ren t line<br />
d$ de lete <strong>to</strong> end of l ine<br />
Block ma . ...d’ a ma r k start of block ,<br />
mo ve the cur sor <strong>to</strong> block end , <strong>and</strong> de lete<br />
-----------------------------------------------------------------------------<br />
In Comma n d mo d e you can enter Tex t Mo d e us i ng :<br />
Re t ur n <strong>to</strong> Comma n d Mo d e from Tex t Mo d e :<br />
i - inse r t tex t before the cur ren t cu rso r po s ition<br />
I - inse r t tex t at the beg inni ngofthe cur ren t line<br />
a - append tex t af ter the cur ren t cu rso r po s ition<br />
A - append tex t at the end of the cur ren t line<br />
o - open s anew l ine for inpu t be l ow t he cur ren t line .<br />
O - open s anew l ine for inpu t abo ve the cur ren t line .<br />
es c - ret urn <strong>to</strong> comma n d mo d e<br />
-----------------------------------------------------------------------------<br />
BLOC K MO V ING ma mar k star t of "a" block<br />
y’a takes a copy o f block f rom ’a <strong>to</strong> cur ren t<br />
-----------------------------------------------------------------------------<br />
SEARCH<br />
/wor d sear che s fo r wo r d<br />
-----------------------------------------------------------------------------<br />
YA N KBACK :<br />
Y copy l ine int o yank bac k bu f fe r<br />
yw copy cur ren t wo r d int o yank bac k bu f fe r<br />
25
y$ copy rema i nde r of l ine int o yank bac k bu f fe r<br />
yˆ copy start of l ine <strong>to</strong> cur ren t in<strong>to</strong> yan kba ck buf fer<br />
p yan ks bac k de l et ed i temafter cur sor<br />
P yan ks bac k de l et ed i tembefor e cu rso r<br />
-----------------------------------------------------------------------------<br />
FI LEHANDL ING :<br />
:w filename . . :file you r text inaname d di sc file<br />
:r filename . . :ge t aname d file int o EMA CS for edi t ing<br />
:s :save you r fileont o di sc <strong>and</strong> con t inue ed iting<br />
------------------------------------------------------------------------------<br />
UN I XTEMP ORARYESCA P E fo r non -X peop l e:<br />
sh : temp o ra r ily drops out of vi int o anew she l l,<br />
re tur n <strong>to</strong> vi by typ i ng "ex i t"<br />
------------------------------------------------------------------------------<br />
ASSOR TED :<br />
es c :abo r t the cur ren t comm <strong>and</strong><br />
/wor d :sea r ch for wor d<br />
------------------------------------------------------------------------------<br />
EX I T:<br />
:ZZ :save fi le <strong>and</strong> exi t from v i<br />
:q :qui t<br />
:q! :qu i t, wha tev er<br />
------------------------------------------------------------------------------<br />
Icer tainly prefer emacs <strong>to</strong> vi, but there remain some who think emacs makes life way <strong>to</strong>o easy for serious<br />
programmers: vi is for real. Try enter ing your CV in<strong>to</strong> vi, then type it in again <strong>to</strong> emacs. Ithink the latter will be<br />
aless painful exper ience.<br />
26