July 2006 Volume 9 Number 3 - CiteSeerX
July 2006 Volume 9 Number 3 - CiteSeerX
July 2006 Volume 9 Number 3 - CiteSeerX
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Solving this problem involved the following database development concepts: defining, constructing,<br />
manipulating, protecting and sharing databases. In this example, three students (students I, J and K) were in a<br />
group. Student K submitted his portfolio and students I and J assessed independently student K’s portfolio.<br />
Students I, J and K were allowed to construct their own fuzzy membership functions for the same evaluation<br />
concepts such as Completeness, Security and Flexibility to assess the portfolio. Following the workflow<br />
presented in Fig. 3, the assessment process was divided into the following steps.<br />
Defining the Fuzzy Constraints<br />
The instructor first explained each evaluation concept to the students. Students I, J and K defined membership<br />
functions for each evaluation concept. Each membership function was considered as a fuzzy constraint. After<br />
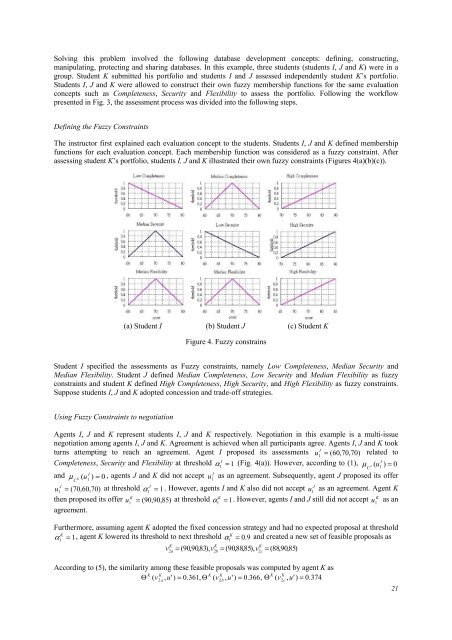
assessing student K’s portfolio, students I, J and K illustrated their own fuzzy constraints (Figures 4(a)(b)(c)).<br />
(a) Student I (b) Student J (c) Student K<br />
Figure 4. Fuzzy constrains<br />
Student I specified the assessments as Fuzzy constraints, namely Low Completeness, Median Security and<br />
Median Flexibility. Student J defined Median Completeness, Low Security and Median Flexibility as fuzzy<br />
constraints and student K defined High Completeness, High Security, and High Flexibility as fuzzy constraints.<br />
Suppose students I, J and K adopted concession and trade-off strategies.<br />
Using Fuzzy Constraints to negotiation<br />
Agents I, J and K represent students I, J and K respectively. Negotiation in this example is a multi-issue<br />
negotiation among agents I, J and K. Agreement is achieved when all participants agree. Agents I, J and K took<br />
I<br />
turns attempting to reach an agreement. Agent I proposed its assessments u 1 = ( 60,<br />
70,<br />
70)<br />
related to<br />
Completeness, Security and Flexibility at threshold 1 1 =<br />
I<br />
I<br />
α (Fig. 4(a)). However, according to (1), ( 1 ) = 0<br />
C u μ J<br />
I and ( 1 ) = 0 u<br />
I<br />
μ , agents J and K did not accept u1 as an agreement. Subsequently, agent J proposed its offer<br />
K<br />
C<br />
1 ( 70,<br />
60,<br />
70)<br />
=<br />
J<br />
J<br />
J<br />
u at threshold α 1 = 1.<br />
However, agents I and K also did not accept u1 as an agreement. Agent K<br />
then proposed its offer 1 ( 90,<br />
90,<br />
85)<br />
=<br />
K<br />
u at threshold 1 1 =<br />
K<br />
α . However, agents I and J still did not accept K<br />
u as an<br />
1<br />
agreement.<br />
Furthermore, assuming agent K adopted the fixed concession strategy and had no expected proposal at threshold<br />
K<br />
K<br />
α 1 = 1,<br />
agent K lowered its threshold to next threshold α 1 = 0.<br />
9 and created a new set of feasible proposals as<br />
K<br />
K<br />
K<br />
v = 90,<br />
90,<br />
83),<br />
v = ( 90,<br />
88,<br />
85),<br />
v = ( 88,<br />
90,<br />
85)<br />
2 a<br />
( 2b<br />
2c<br />
According to (5), the similarity among these feasible proposals was computed by agent K as<br />
K<br />
Θ<br />
K<br />
K K<br />
v , u'<br />
) = 0.<br />
361,<br />
Θ ( v , u'<br />
) = 0.<br />
366,<br />
Θ v , u'<br />
) = 0.<br />
374<br />
K K<br />
( 2 a<br />
2b<br />
( 2 c<br />
21