Chapter 3 Time-to-live Covert Channels - CAIA
Chapter 3 Time-to-live Covert Channels - CAIA
Chapter 3 Time-to-live Covert Channels - CAIA
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
CHAPTER 3. TIME-TO-LIVE COVERT CHANNELS<br />
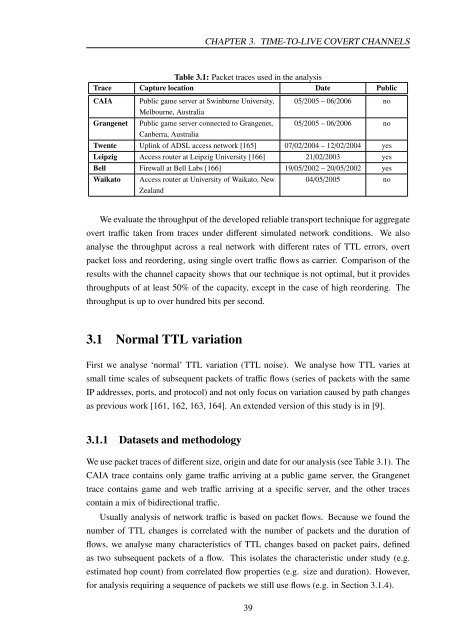
Table 3.1: Packet traces used in the analysis<br />
Trace Capture location Date Public<br />
<strong>CAIA</strong> Public game server at Swinburne University,<br />
Melbourne, Australia<br />
Grangenet Public game server connected <strong>to</strong> Grangenet,<br />
Canberra, Australia<br />
05/2005 – 06/2006 no<br />
05/2005 – 06/2006 no<br />
Twente Uplink of ADSL access network [165] 07/02/2004 – 12/02/2004 yes<br />
Leipzig Access router at Leipzig University [166] 21/02/2003 yes<br />
Bell Firewall at Bell Labs [166] 19/05/2002 – 20/05/2002 yes<br />
Waika<strong>to</strong> Access router at University of Waika<strong>to</strong>, New<br />
Zealand<br />
04/05/2005 no<br />
We evaluate the throughput of the developed reliable transport technique for aggregate<br />
overt traffic taken from traces under different simulated network conditions. We also<br />
analyse the throughput across a real network with different rates of TTL errors, overt<br />
packet loss and reordering, using single overt traffic flows as carrier. Comparison of the<br />
results with the channel capacity shows that our technique is not optimal, but it provides<br />
throughputs of at least 50% of the capacity, except in the case of high reordering. The<br />
throughput is up <strong>to</strong> over hundred bits per second.<br />
3.1 Normal TTL variation<br />
First we analyse ‘normal’ TTL variation (TTL noise). We analyse how TTL varies at<br />
small time scales of subsequent packets of traffic flows (series of packets with the same<br />
IP addresses, ports, and pro<strong>to</strong>col) and not only focus on variation caused by path changes<br />
as previous work [161, 162, 163, 164]. An extended version of this study is in [9].<br />
3.1.1 Datasets and methodology<br />
We use packet traces of different size, origin and date for our analysis (see Table 3.1). The<br />
<strong>CAIA</strong> trace contains only game traffic arriving at a public game server, the Grangenet<br />
trace contains game and web traffic arriving at a specific server, and the other traces<br />
contain a mix of bidirectional traffic.<br />
Usually analysis of network traffic is based on packet flows. Because we found the<br />
number of TTL changes is correlated with the number of packets and the duration of<br />
flows, we analyse many characteristics of TTL changes based on packet pairs, defined<br />
as two subsequent packets of a flow. This isolates the characteristic under study (e.g.<br />
estimated hop count) from correlated flow properties (e.g. size and duration). However,<br />
for analysis requiring a sequence of packets we still use flows (e.g. in Section 3.1.4).<br />
39