Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
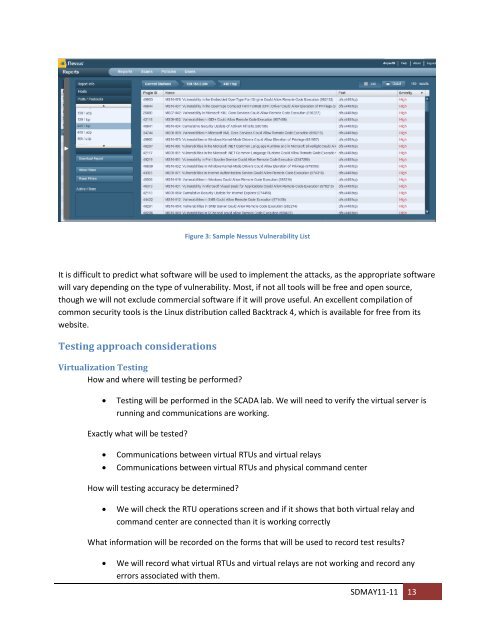
Figure 3: Sample Nessus Vulnerability List<br />
It is difficult to predict what s<strong>of</strong>tware will be used to implement the attacks, as the appropriate s<strong>of</strong>tware<br />
will vary depending on the type <strong>of</strong> vulnerability. Most, if not all tools will be free and open source,<br />
though we will not exclude commercial s<strong>of</strong>tware if it will prove useful. An excellent compilation <strong>of</strong><br />
common security tools is the Linux distribution called Backtrack 4, which is available for free from its<br />
website.<br />
Testing approach considerations<br />
Virtualization Testing<br />
How and where will <strong>test</strong>ing be performed?<br />
Testing will be performed in the <strong>SCADA</strong> lab. We will need to verify the virtual server is<br />
running and communications are working.<br />
Exactly what will be <strong>test</strong>ed?<br />
Communications between virtual RTUs and virtual relays<br />
Communications between virtual RTUs and physical command center<br />
How will <strong>test</strong>ing accuracy be determined?<br />
We will check the RTU operations screen and if it shows that both virtual relay and<br />
command center are connected than it is working correctly<br />
What information will be recorded on the forms that will be used to record <strong>test</strong> results?<br />
We will record what virtual RTUs and virtual relays are not working and record any<br />
errors associated with them.<br />
SDMAY11-11 13