Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
Cyber Security of SCADA Systems test bed - Senior Design - Iowa ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
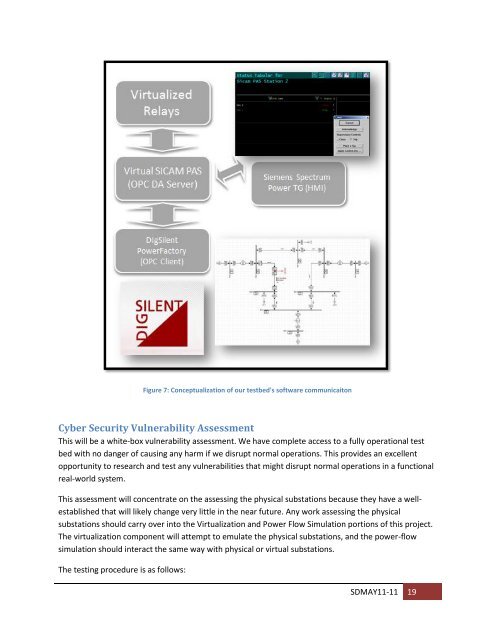
Figure 7: Conceptualization <strong>of</strong> our <strong>test</strong><strong>bed</strong>'s s<strong>of</strong>tware communicaiton<br />
<strong>Cyber</strong> <strong>Security</strong> Vulnerability Assessment<br />
This will be a white-box vulnerability assessment. We have complete access to a fully operational <strong>test</strong><br />
<strong>bed</strong> with no danger <strong>of</strong> causing any harm if we disrupt normal operations. This provides an excellent<br />
opportunity to research and <strong>test</strong> any vulnerabilities that might disrupt normal operations in a functional<br />
real-world system.<br />
This assessment will concentrate on the assessing the physical substations because they have a wellestablished<br />
that will likely change very little in the near future. Any work assessing the physical<br />
substations should carry over into the Virtualization and Power Flow Simulation portions <strong>of</strong> this project.<br />
The virtualization component will attempt to emulate the physical substations, and the power-flow<br />
simulation should interact the same way with physical or virtual substations.<br />
The <strong>test</strong>ing procedure is as follows:<br />
SDMAY11-11 19