FortiDDos DDoS Attack Mitigation Guide - Fortinet
FortiDDos DDoS Attack Mitigation Guide - Fortinet
FortiDDos DDoS Attack Mitigation Guide - Fortinet
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
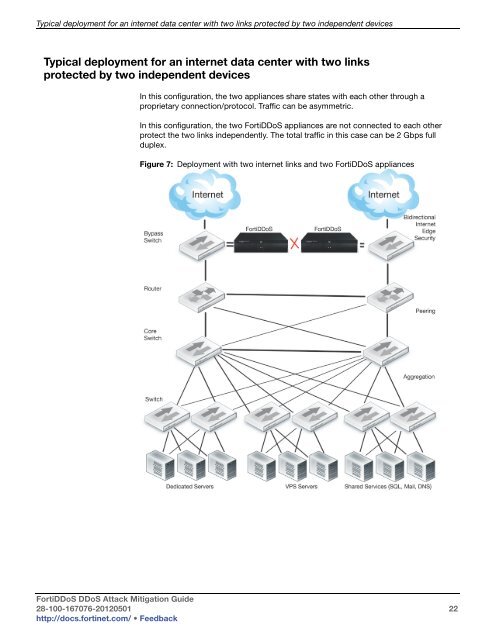
Typical deployment for an internet data center with two links protected by two independent devices<br />
Typical deployment for an internet data center with two links<br />
protected by two independent devices<br />
In this configuration, the two appliances share states with each other through a<br />
proprietary connection/protocol. Traffic can be asymmetric.<br />
In this configuration, the two Forti<strong>DDoS</strong> appliances are not connected to each other<br />
protect the two links independently. The total traffic in this case can be 2 Gbps full<br />
duplex.<br />
Figure 7: Deployment with two internet links and two Forti<strong>DDoS</strong> appliances<br />
Forti<strong>DDoS</strong> <strong>DDoS</strong> <strong>Attack</strong> <strong>Mitigation</strong> <strong>Guide</strong><br />
28-100-167076-20120501 22<br />
http://docs.fortinet.com/ • Feedback