FortiDDos DDoS Attack Mitigation Guide - Fortinet
FortiDDos DDoS Attack Mitigation Guide - Fortinet
FortiDDos DDoS Attack Mitigation Guide - Fortinet
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>DDoS</strong> attack test conditions - a broad classification<br />
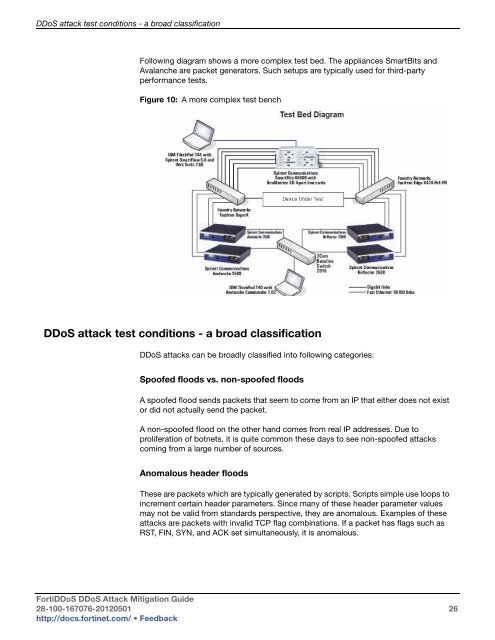
Following diagram shows a more complex test bed. The appliances SmartBits and<br />
Avalanche are packet generators. Such setups are typically used for third-party<br />
performance tests.<br />
Figure 10: A more complex test bench<br />
<strong>DDoS</strong> attack test conditions - a broad classification<br />
<strong>DDoS</strong> attacks can be broadly classified into following categories:<br />
Spoofed floods vs. non-spoofed floods<br />
A spoofed flood sends packets that seem to come from an IP that either does not exist<br />
or did not actually send the packet.<br />
A non-spoofed flood on the other hand comes from real IP addresses. Due to<br />
proliferation of botnets, it is quite common these days to see non-spoofed attacks<br />
coming from a large number of sources.<br />
Anomalous header floods<br />
These are packets which are typically generated by scripts. Scripts simple use loops to<br />
increment certain header parameters. Since many of these header parameter values<br />
may not be valid from standards perspective, they are anomalous. Examples of these<br />
attacks are packets with invalid TCP flag combinations. If a packet has flags such as<br />
RST, FIN, SYN, and ACK set simultaneously, it is anomalous.<br />
Forti<strong>DDoS</strong> <strong>DDoS</strong> <strong>Attack</strong> <strong>Mitigation</strong> <strong>Guide</strong><br />
28-100-167076-20120501 26<br />
http://docs.fortinet.com/ • Feedback