Evaluation of Department of State Information Security Program ...
Evaluation of Department of State Information Security Program ...
Evaluation of Department of State Information Security Program ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
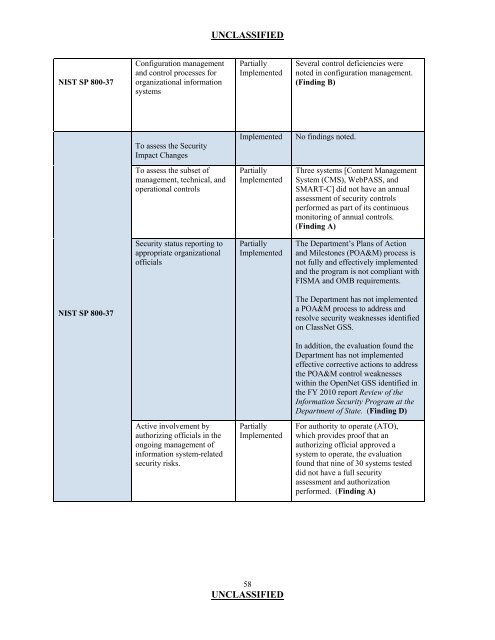
NIST SP 800-37<br />
NIST SP 800-37<br />
Configuration management<br />
and control processes for<br />
organizational information<br />
systems<br />
To assess the <strong>Security</strong><br />
Impact Changes<br />
UNCLASSIFIED<br />
Partially<br />
Implemented<br />
Several control deficiencies were<br />
noted in configuration management.<br />
(Finding B)<br />
Implemented No findings noted.<br />
To assess the subset <strong>of</strong> Partially Three systems [Content Management<br />
management, technical, and Implemented System (CMS), WebPASS, and<br />
operational controls SMART-C] did not have an annual<br />
assessment <strong>of</strong> security controls<br />
performed as part <strong>of</strong> its continuous<br />
monitoring <strong>of</strong> annual controls.<br />
(Finding A)<br />
<strong>Security</strong> status reporting to Partially The <strong>Department</strong>’s Plans <strong>of</strong> Action<br />
appropriate organizational Implemented and Milestones (POA&M) process is<br />
<strong>of</strong>ficials not fully and effectively implemented<br />
and the program is not compliant with<br />
FISMA and OMB requirements.<br />
The <strong>Department</strong> has not implemented<br />
a POA&M process to address and<br />
resolve security weaknesses identified<br />
on ClassNet GSS.<br />
In addition, the evaluation found the<br />
<strong>Department</strong> has not implemented<br />
effective corrective actions to address<br />
the POA&M control weaknesses<br />
within the OpenNet GSS identified in<br />
the FY 2010 report Review <strong>of</strong> the<br />
<strong>Information</strong> <strong>Security</strong> <strong>Program</strong> at the<br />
<strong>Department</strong> <strong>of</strong> <strong>State</strong>. (Finding D)<br />
Active involvement by Partially For authority to operate (ATO),<br />
authorizing <strong>of</strong>ficials in the Implemented which provides pro<strong>of</strong> that an<br />
ongoing management <strong>of</strong> authorizing <strong>of</strong>ficial approved a<br />
information system-related system to operate, the evaluation<br />
security risks. found that nine <strong>of</strong> 30 systems tested<br />
did not have a full security<br />
assessment and authorization<br />
performed. (Finding A)<br />
58<br />
UNCLASSIFIED