A Network Approach to E-identification
A Network Approach to E-identification
A Network Approach to E-identification
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
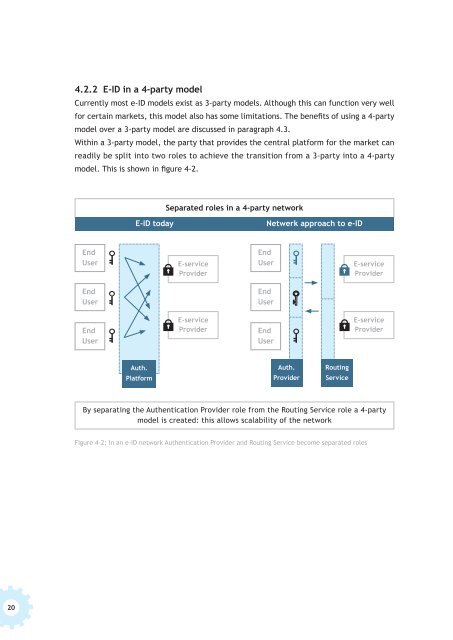
4.2.2 E-ID in a 4-party model<br />
Currently most e-ID models exist as 3-party models. Although this can function very well<br />
for certain markets, this model also has some limitations. The benefits of using a 4-party<br />
model over a 3-party model are discussed in paragraph 4.3.<br />
Within a 3-party model, the party that provides the central platform for the market can<br />
readily be split in<strong>to</strong> two roles <strong>to</strong> achieve the transition from a 3-party in<strong>to</strong> a 4-party<br />
model. This is shown in figure 4-2.<br />
Separated roles in a 4-party network<br />
E-ID <strong>to</strong>day<br />
Netwerk approach <strong>to</strong> e-ID<br />
End<br />
User<br />
E-service<br />
Provider<br />
End<br />
User<br />
E-service<br />
Provider<br />
End<br />
User<br />
End<br />
User<br />
End<br />
User<br />
E-service<br />
Provider<br />
End<br />
User<br />
E-service<br />
Provider<br />
Auth.<br />
Platform<br />
Auth.<br />
Provider<br />
Routing<br />
Service<br />
By separating the Authentication Provider role from the Routing Service role a 4-party<br />
model is created: this allows scalability of the network<br />
Figure 4-2: In an e-ID network Authentication Provider and Routing Service become separated roles<br />
20