A Network Approach to E-identification
A Network Approach to E-identification
A Network Approach to E-identification
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
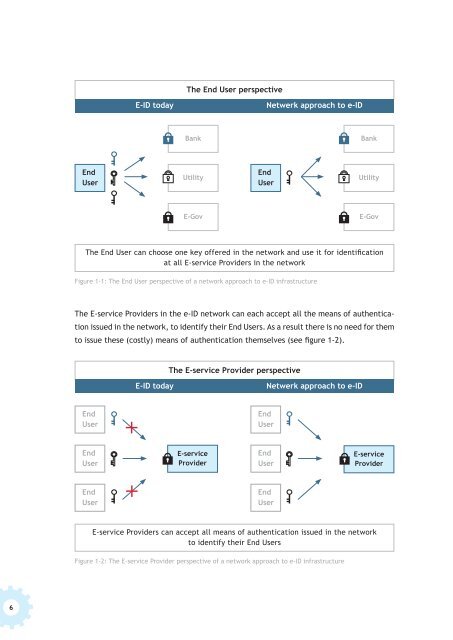
The End User perspective<br />
E-ID <strong>to</strong>day<br />
Netwerk approach <strong>to</strong> e-ID<br />
Bank<br />
Bank<br />
End<br />
User<br />
Utility<br />
End<br />
User<br />
Utility<br />
E-Gov<br />
E-Gov<br />
The End User can choose one key offered in the network and use it for <strong>identification</strong><br />
at all E-service Providers in the network<br />
Figure 1-1: The End User perspective of a network approach <strong>to</strong> e-ID infrastructure<br />
The E-service Providers in the e-ID network can each accept all the means of authentication<br />
issued in the network, <strong>to</strong> identify their End Users. As a result there is no need for them<br />
<strong>to</strong> issue these (costly) means of authentication themselves (see figure 1-2).<br />
The E-service Provider perspective<br />
E-ID <strong>to</strong>day<br />
Netwerk approach <strong>to</strong> e-ID<br />
End<br />
User<br />
End<br />
User<br />
End<br />
User<br />
E-service<br />
Provider<br />
End<br />
User<br />
E-service<br />
Provider<br />
End<br />
User<br />
End<br />
User<br />
E-service Providers can accept all means of authentication issued in the network<br />
<strong>to</strong> identify their End Users<br />
Figure 1-2: The E-service Provider perspective of a network approach <strong>to</strong> e-ID infrastructure<br />
6