A Network Approach to E-identification
A Network Approach to E-identification
A Network Approach to E-identification
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
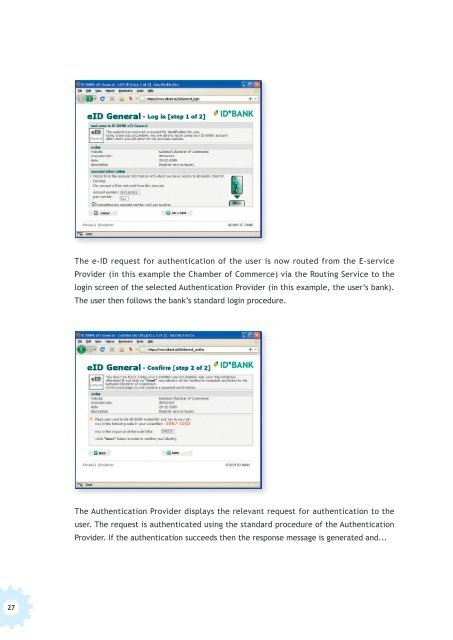
The e-ID request for authentication of the user is now routed from the E-service<br />
Provider (in this example the Chamber of Commerce) via the Routing Service <strong>to</strong> the<br />
login screen of the selected Authentication Provider (in this example, the user’s bank).<br />
The user then follows the bank’s standard login procedure.<br />
The Authentication Provider displays the relevant request for authentication <strong>to</strong> the<br />
user. The request is authenticated using the standard procedure of the Authentication<br />
Provider. If the authentication succeeds then the response message is generated and...<br />
27