The Applications Handbook.pdf - Nexus Technologies Inc.
The Applications Handbook.pdf - Nexus Technologies Inc.
The Applications Handbook.pdf - Nexus Technologies Inc.
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
60 ■ <strong>The</strong> <strong>Applications</strong> <strong>Handbook</strong><br />
not occur until just before the application is due to launch, and<br />
sometimes not until after an application goes live.<br />
As a result, security flaws in the application source code (a significant<br />
bug, by any definition) aren’t discovered until the latest<br />
possible moment. <strong>The</strong> costs to fix these bugs at that point<br />
are sky high. Furthermore, pressures to go live often result in<br />
the aggressive backlogging of known security holes that seldom<br />
get filled.<br />
<strong>The</strong> right way to manage application security is to see it in<br />
terms of the complete lifecycle. Where the legacy view believes<br />
that security tasks are the responsibility of the security team,<br />
the modern approach is to make the entire application team<br />
accountable. Security vulnerabilities are like any other defect,<br />
and prevention and early detection are the watchwords.<br />
What does it mean to thread security throughout the application<br />
lifecycle? Consider the following ideal organizational<br />
approach:<br />
• Planning: Stakeholders assign a security-risk score to<br />
each candidate-application investment, based on factors<br />
such as audience (internal or external), data sensitivity,<br />
network and server placement (proximate to other confidential<br />
data?), and any regulatory standards for privacy<br />
or security. <strong>The</strong> risk level drives the necessary<br />
security requirements for the application.<br />
Security teams work with application teams to develop<br />
a standard risk-level matrix and a set of standard<br />
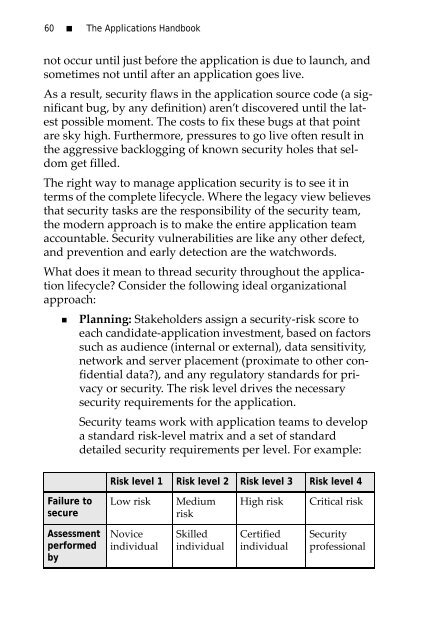
detailed security requirements per level. For example:<br />
Risk level 1 Risk level 2 Risk level 3 Risk level 4<br />
Failure to<br />
secure<br />
Low risk<br />
Medium<br />
risk<br />
High risk<br />
Critical risk<br />
Assessment<br />
performed<br />
by<br />
Novice<br />
individual<br />
Skilled<br />
individual<br />
Certified<br />
individual<br />
Security<br />
professional