third Cyber Security Assessment Netherlands - NCSC
third Cyber Security Assessment Netherlands - NCSC
third Cyber Security Assessment Netherlands - NCSC
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Core assessment » 3 Threats: tools<br />
»<br />
»»»»»<br />
that botnets that are aimed at financial transactions can also steal<br />
a great deal of other data that can then pose a significant risk. In<br />
the case of Pobelka it appeared that sensitive data from businesses<br />
and governmental departments in the vital sectors, as well as large<br />
quantities of personal data, had been stolen.<br />
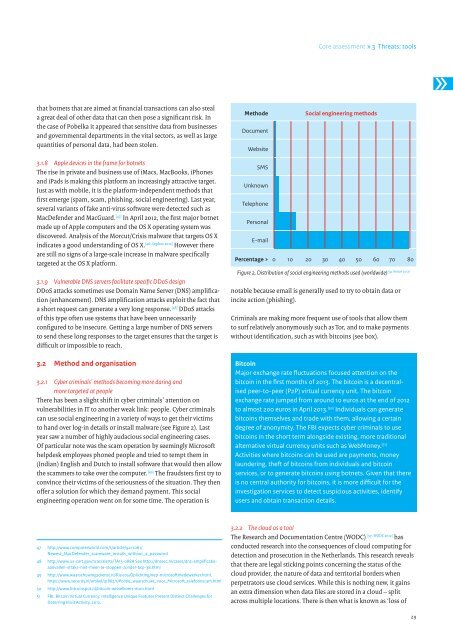
Methode<br />
Document<br />
Website<br />
Social engineering methods<br />
3.1.8 Apple devices in the frame for botnets<br />
The rise in private and business use of iMacs, MacBooks, iPhones<br />
and iPads is making this platform an increasingly attractive target.<br />
Just as with mobile, it is the platform-independent methods that<br />
first emerge (spam, scam, phishing, social engineering). Last year,<br />
several variants of fake anti-virus software were detected such as<br />
MacDefender and MacGuard. [47] In April 2012, the first major botnet<br />
made up of Apple computers and the OS X operating system was<br />
discovered. Analysis of the Morcut/Crisis malware that targets OS X<br />
indicates a good understanding of OS X. [46: Sophos 2012] However there<br />
are still no signs of a large-scale increase in malware specifically<br />
targeted at the OS X platform.<br />
3.1.9 Vulnerable DNS servers facilitate specific DDoS design<br />
DDoS attacks sometimes use Domain Name Server (DNS) amplification<br />
(enhancement). DNS amplification attacks exploit the fact that<br />
a short request can generate a very long response. [48] DDoS attacks<br />
of this type often use systems that have been unnecessarily<br />
configured to be insecure. Getting a large number of DNS servers<br />
to send these long responses to the target ensures that the target is<br />
difficult or impossible to reach.<br />
3.2 Method and organisation<br />
3.2.1 <strong>Cyber</strong> criminals’ methods becoming more daring and<br />
more targeted at people<br />
There has been a slight shift in cyber criminals’ attention on<br />
vulnerabilities in IT to another weak link: people. <strong>Cyber</strong> criminals<br />
can use social engineering in a variety of ways to get their victims<br />
to hand over log-in details or install malware (see Figure 2). Last<br />
year saw a number of highly audacious social engineering cases.<br />
Of particular note was the scam operation by seemingly Microsoft<br />
helpdesk employees phoned people and tried to tempt them in<br />
(Indian) English and Dutch to install software that would then allow<br />
the scammers to take over the computer. [49] The fraudsters first try to<br />
convince their victims of the seriousness of the situation. They then<br />
offer a solution for which they demand payment. This social<br />
engineering operation went on for some time. The operation is<br />
SMS<br />
Unknown<br />
Telephone<br />
Personal<br />
E-mail<br />
Percentage > 0 10 20 30 40 50 60 70 80<br />
[54: Verizon 2012]<br />
Figure 2. Distribution of social engineering methods used (worldwide)<br />
notable because email is generally used to try to obtain data or<br />
incite action (phishing).<br />
Criminals are making more frequent use of tools that allow them<br />
to surf relatively anonymously such as Tor, and to make payments<br />
without identification, such as with bitcoins (see box).<br />
Bitcoin<br />
Major exchange rate fluctuations focused attention on the<br />
bitcoin in the first months of 2013. The bitcoin is a decentralised<br />
peer-to-peer (P2P) virtual currency unit. The bitcoin<br />
exchange rate jumped from around 10 euros at the end of 2012<br />
to almost 200 euros in April 2013. [50] Individuals can generate<br />
bitcoins themselves and trade with them, allowing a certain<br />
degree of anonymity. The FBI expects cyber criminals to use<br />
bitcoins in the short term alongside existing, more traditional<br />
alternative virtual currency units such as WebMoney. [51]<br />
Activities where bitcoins can be used are payments, money<br />
laundering, theft of bitcoins from individuals and bitcoin<br />
services, or to generate bitcoins using botnets. Given that there<br />
is no central authority for bitcoins, it is more difficult for the<br />
investigation services to detect suspicious activities, identify<br />
users and obtain transaction details.<br />
47 http://www.computerworld.com/s/article/9217061/<br />
Newest_MacDefender_scareware_installs_without_a_password<br />
48 http://www.us-cert.gov/ncas/alerts/TA13-088A See http://dnssec.nl/cases/dns-amplificatieaanvallen-straks-niet-meer-te-stoppen-zonder-bcp-38.html<br />
49 http://www.waarschuwingsdienst.nl/Risicos/Oplichting/nep-microsoftmedewerker.html,<br />
https://www.security.nl/artikel/41862/1/Politie_waarschuwt_voor_Microsoft_telefoonscam.html<br />
50 http://www.bitcoinspot.nl/bitcoin-wisselkoers-euro.html<br />
51 FBI, Bitcoin Virtual Currency: Intelligence Unique Features Present Distinct Challenges for<br />
Deterring Illicit Activity, 2012.<br />
3.2.2 The cloud as a tool<br />
The Research and Documentation Centre (WODC) [57: WODC 2012] has<br />
conducted research into the consequences of cloud computing for<br />
detection and prosecution in the <strong>Netherlands</strong>. This research reveals<br />
that there are legal sticking points concerning the status of the<br />
cloud provider, the nature of data and territorial borders when<br />
perpetrators use cloud services. While this is nothing new, it gains<br />
an extra dimension when data files are stored in a cloud – split<br />
across multiple locations. There is then what is known as ‘loss of<br />
29