- Page 1 and 2: On the Use of OffensiveCyber Capabi
- Page 3 and 4: Table of ContentsAcknowledgements .
- Page 5: Executive SummaryThe defining chara
- Page 9 and 10: I. IntroductionThough conflict inev
- Page 11 and 12: Unfortunately, we believe that ther
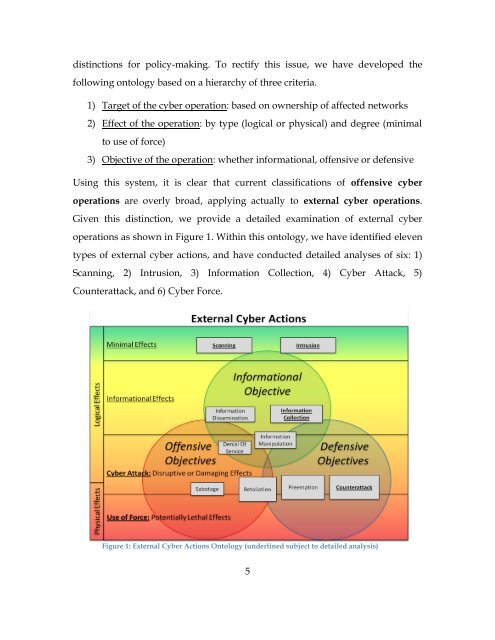
- Page 13 and 14: To the maximum extent possible we u
- Page 15 and 16: these cyberspace operations “comp
- Page 17 and 18: Principles Driving the Ontological
- Page 19 and 20: Cyber activity can have both logica
- Page 21 and 22: cyberspace and complicates sound na
- Page 23 and 24: cyber action, but we do find them t
- Page 25 and 26: Cyber Pre-emption: External cyber o
- Page 27 and 28: threatening external action or enta
- Page 29 and 30: Figure 5: Framework for Cyber Polic
- Page 31 and 32: effects of external cyber operation
- Page 33 and 34: International LawInternational cons
- Page 35 and 36: There is also an interaction betwee
- Page 37 and 38: TemporalCommanders desire the abili
- Page 39 and 40: InternationalMultilateral action is
- Page 41 and 42: Potential changes to the “laws of
- Page 43 and 44: Scanning:IV. Cyber Actions with Min
- Page 45 and 46: The 4 th Amendment protects against
- Page 47 and 48: operational intelligence collection
- Page 49 and 50: security vulnerabilities are identi
- Page 51 and 52: 1) Establish an interagency underst
- Page 53 and 54: individual’s agency must be justi
- Page 55 and 56: Finally section (f) exempts only la
- Page 57 and 58:
argue it is not intended to limits
- Page 59 and 60:
intrusion methods are required to e
- Page 61 and 62:
SystemicDespite the first order eff
- Page 63 and 64:
is possible. The capabilities used
- Page 65 and 66:
d. Section (f) should be expanded t
- Page 67 and 68:
indicates a will to keep the inform
- Page 69 and 70:
protections for privacy. However, t
- Page 71 and 72:
information on U.S. persons collect
- Page 73 and 74:
Example ScenarioThe following scena
- Page 75 and 76:
the awkward position: if it is unkn
- Page 77 and 78:
less severe than attack are largely
- Page 79 and 80:
treaties. This second set of duties
- Page 81 and 82:
persons. Beyond the limitations pla
- Page 83 and 84:
instead of force, when cyber attack
- Page 85 and 86:
collection effort to generate all t
- Page 87 and 88:
and incentivize technology companie
- Page 89 and 90:
operational capabilities for employ
- Page 91 and 92:
2) To ensure the operational capabi
- Page 93 and 94:
and are entirely permissible ethica
- Page 95 and 96:
equires an external component. The
- Page 97 and 98:
any one branch’s overreach. (We h
- Page 99 and 100:
particularly from limiting espionag
- Page 101 and 102:
more destructive/disruptive. Though
- Page 103 and 104:
to reach an interagency understandi
- Page 105 and 106:
counterattacks to serve as a deterr
- Page 107 and 108:
however, may require a significant
- Page 109 and 110:
There is a possibility of a backlas
- Page 111 and 112:
2) The foreign external cyber opera
- Page 113 and 114:
For the purpose of this work, a pre
- Page 115 and 116:
Although the ethical considerations
- Page 117 and 118:
ight to “life, liberty and securi
- Page 119 and 120:
would be hard to overstate. 131 Thi
- Page 121 and 122:
ConsequentialDomesticAs mentioned i
- Page 123 and 124:
extent to which the executive branc
- Page 125 and 126:
public as new U.S. military technol
- Page 127 and 128:
IC believes that the HVT is using 3
- Page 129 and 130:
Policy Recommendations1) Use of cyb
- Page 131 and 132:
identified by our ontology, spannin
- Page 133 and 134:
Appendix 1: Summary of Recommendati
- Page 135 and 136:
c. Amended (a)(2) (a), (b), and (c)
- Page 137 and 138:
gained) and necessity (only the min
- Page 139 and 140:
2) If overt, cyber force should be
- Page 141 and 142:
Cyber Intrusion: Unauthorized acces
- Page 143 and 144:
BibliographyAllison, G. T., & Black
- Page 145 and 146:
Etzioni, A. (2011). Cybersecurity i
- Page 147 and 148:
Jacobellis v. Ohio, 11 (United Stat
- Page 149 and 150:
Nye, Jr., J. S. (2004). Soft Power.
- Page 151 and 152:
United Nations. (1948, December 10)
- Page 153:
152