On the Use of Offensive Cyber Capabilities - Belfer Center for ...
On the Use of Offensive Cyber Capabilities - Belfer Center for ...
On the Use of Offensive Cyber Capabilities - Belfer Center for ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
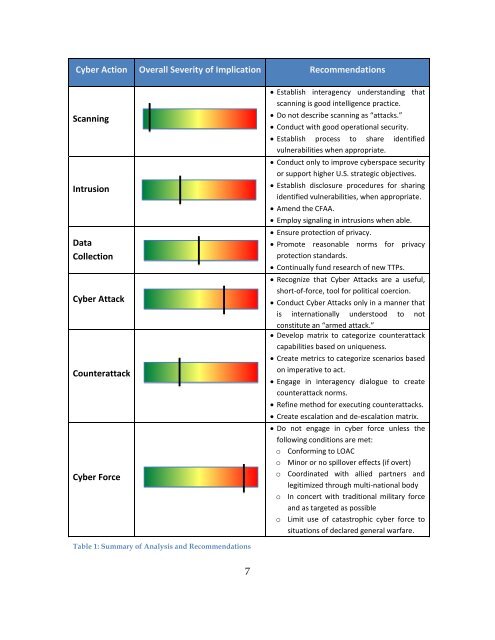
<strong>Cyber</strong> Action Overall Severity <strong>of</strong> Implication RecommendationsScanningIntrusionDataCollection<strong>Cyber</strong> AttackCounterattack<strong>Cyber</strong> Force Establish interagency understanding thatscanning is good intelligence practice. Do not describe scanning as “attacks.” Conduct with good operational security. Establish process to share identifiedvulnerabilities when appropriate. Conduct only to improve cyberspace securityor support higher U.S. strategic objectives. Establish disclosure procedures <strong>for</strong> sharingidentified vulnerabilities, when appropriate. Amend <strong>the</strong> CFAA. Employ signaling in intrusions when able. Ensure protection <strong>of</strong> privacy. Promote reasonable norms <strong>for</strong> privacyprotection standards. Continually fund research <strong>of</strong> new TTPs. Recognize that <strong>Cyber</strong> Attacks are a useful,short-<strong>of</strong>-<strong>for</strong>ce, tool <strong>for</strong> political coercion. Conduct <strong>Cyber</strong> Attacks only in a manner thatis internationally understood to notconstitute an “armed attack.” Develop matrix to categorize counterattackcapabilities based on uniqueness. Create metrics to categorize scenarios basedon imperative to act. Engage in interagency dialogue to createcounterattack norms. Refine method <strong>for</strong> executing counterattacks. Create escalation and de-escalation matrix. Do not engage in cyber <strong>for</strong>ce unless <strong>the</strong>following conditions are met:o Con<strong>for</strong>ming to LOACo Minor or no spillover effects (if overt)o Coordinated with allied partners andlegitimized through multi-national bodyo In concert with traditional military <strong>for</strong>ceand as targeted as possibleo Limit use <strong>of</strong> catastrophic cyber <strong>for</strong>ce tosituations <strong>of</strong> declared general warfare.Table 1: Summary <strong>of</strong> Analysis and Recommendations7