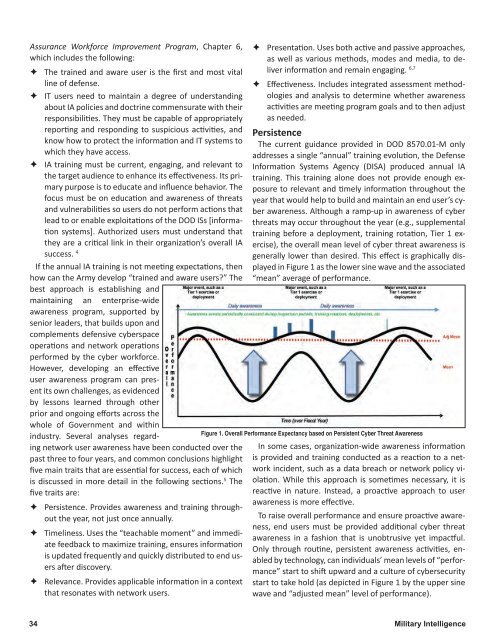
Assurance Workforce Improvement Program, Chapter 6,which includes the following:ÊÊThe trained and aware user is the first and most vitalline of defense.ÊÊIT users need to maintain a degree of understandingabout IA policies and doctrine commensurate with theirresponsibilities. They must be capable of appropriatelyreporting and responding to suspicious activities, andknow how to protect the information and IT systems towhich they have access.ÊÊIA training must be current, engaging, and relevant tothe target audience to enhance its effectiveness. Its primarypurpose is to educate and influence behavior. Thefocus must be on education and awareness of threatsand vulnerabilities so users do not perform actions thatlead to or enable exploitations of the DOD ISs [informationsystems]. Authorized users must understand thatthey are a critical link in their organization’s overall IAsuccess. 4If the annual IA training is not meeting expectations, thenhow can the Army develop “trained and aware users?” Thebest approach is establishing andmaintaining an enterprise-wideawareness program, supported bysenior leaders, that builds upon andcomplements defensive cyberspaceoperations and network operationsperformed by the cyber workforce.However, developing an effectiveuser awareness program can presentits own challenges, as evidencedby lessons learned through otherprior and ongoing efforts across thewhole of Government and withinindustry. Several analyses regardingnetwork user awareness have been conducted over thepast three to four years, and common conclusions highlightfive main traits that are essential for success, each of whichis discussed in more detail in the following sections. 5 Thefive traits are:ÊÊPersistence. Provides awareness and training throughoutthe year, not just once annually.ÊÊTimeliness. Uses the “teachable moment” and immediatefeedback to maximize training, ensures informationis updated frequently and quickly distributed to end usersafter discovery.ÊÊRelevance. Provides applicable information in a contextthat resonates with network users.ÊÊPresentation. Uses both active and passive approaches,as well as various methods, modes and media, to deliverinformation and remain engaging. 6,7ÊÊEffectiveness. Includes integrated assessment methodologiesand analysis to determine whether awarenessactivities are meeting program goals and to then adjustas needed.PersistenceThe current guidance provided in DOD 8570.<strong>01</strong>-M onlyaddresses a single “annual” training evolution, the DefenseInformation Systems Agency (DISA) produced annual IAtraining. This training alone does not provide enough exposureto relevant and timely information throughout theyear that would help to build and maintain an end user’s cyberawareness. Although a ramp-up in awareness of cyberthreats may occur throughout the year (e.g., supplementaltraining before a deployment, training rotation, Tier 1 exercise),the overall mean level of cyber threat awareness isgenerally lower than desired. This effect is graphically displayedin Figure 1 as the lower sine wave and the associated“mean” average of performance.Figure 1. Overall Performance Expectancy based on Persistent Cyber Threat AwarenessIn some cases, organization-wide awareness informationis provided and training conducted as a reaction to a networkincident, such as a data breach or network policy violation.While this approach is sometimes necessary, it isreactive in nature. Instead, a proactive approach to userawareness is more effective.To raise overall performance and ensure proactive awareness,end users must be provided additional cyber threatawareness in a fashion that is unobtrusive yet impactful.Only through routine, persistent awareness activities, enabledby technology, can individuals’ mean levels of “performance”start to shift upward and a culture of cybersecuritystart to take hold (as depicted in Figure 1 by the upper sinewave and “adjusted mean” level of performance).34 Military Intelligence
TimelinessPrior analyses of awareness and training programs havehighlighted that many opportunities for immediate feedbackto an IA/cybersecurity incident are missed. For example,if a person was involved in an incident, that person maynot immediately understand how his action(s) caused theincident, and by the time feedback is provided (if at all), the“teachable moment” has passed.Therefore, cyber awareness and training should incorporateimmediate feedback and training to maximize the potentialfor learning. For instance, in a phishing awarenessand training campaign, simply collecting data about howmany users clicked on a link, or opened an executable filewithin the phishing awareness email, may provide a statisticfor a brief to senior leadership, but would not support theend goal of shifting culture. However, providing an end userwho “took the bait” with immediate feedback and trainingwould help to maximize the learning retention of thatindividual.In addition, the information presented as part of theawareness and training campaign must be current. Giventhat cyber threats are constantly changing and becomingmore sophisticated the MI community, working with trainingspecialists, IA personnel, and network operations staff,among others, can provide valuable support by collecting,processing, assessing and disseminating informationthat will have same-day impact. For example, informationregarding a discovered vulnerability in an Adobe product,widely used by many at home and at work, could quicklybe made available to end-users for their awareness. A currentscam targeting Army personnel could reach end usersquickly and via multiple sources. The key to success isin establishing the means and processes for quickly gettingthreat information and recommended mitigation measuresout to the entire force, enabling end users to take timely actionswhich bolster cybersecurity and support operationaleffectiveness.RelevanceRelevance, or providing information in a context whichresonates and connects with end users, is in many waystied to timeliness. Although the cyber threat is constantlychanging and becoming more sophisticated, many userawareness programs have not kept pace, relying on staticinformation that might be updated once annually at most.Over time, much of the information presented is irrelevantand does not discuss the current threat.Even more of an issue, however, is that most threat informationpresented to end users is focused on threats togovernment systems and data, many times using scenariosthat are more applicable to the enterprise than to the userthemselves. While protection of government systems, data,and ultimately, operations, is the ultimate goal, this “insidethe fences” approach does not have the desired effect onlearning simply because many end users do not feel the relevanceto themselves as individuals. In order to inculcate aculture of cybersecurity across the force, end users need tobe provided awareness of how they can personally make apositive impact.From a threat awareness perspective, the MI community,working with U.S. Army Cyber Command and the Signalcommunity, can help to improve relevance to end users bycollecting and providing “outside the fences” informationthat end users can more readily relate to, that they feel apersonal stake in, and that they understand has potentialimpact to their personal lives and resources. Simply put,“make it personal.” That means including more informationwithin awareness training and activities that focuses on usersin home and travel settings. In those cases, the end userbecomes the de facto network operations center, responsiblefor those things that ultimately impact the equipmentthey are using, and therefore having a greater (perceived)stake in cybersecurity.Given that many Army personnel use their personalequipment to access government web mail, it becomeseven more critical that they understand how their actionsat home and on travel can impact government systems andmissions. Relevant information provided to end users mightinclude:ÊÊThreats related to cyber crime, including online scams.ÊÊVulnerabilities in common operating systems and applications,so that users can update/protect their personalequipment against potential backdoors into governmentsystems.ÊÊMitigation measures, such as considerations forhome router settings and methods for securing one’ssmart-phone.ÊÊSteps one can take to be more secure on social networkingsites.ÊÊConsiderations for operations security when using socialnetworking and emails.By using a balanced “inside the fences/outside the fences”approach, end users will feel more personally involved andresponsible. The effectiveness of awareness efforts willthen start to increase and provide greater value and returnon investment. Ultimately, a shift in culture toward a moreJanuary - March <strong>2<strong>01</strong>4</strong>35