Using ICMP to Coordinate Systems
Using ICMP to Coordinate Systems
Using ICMP to Coordinate Systems
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
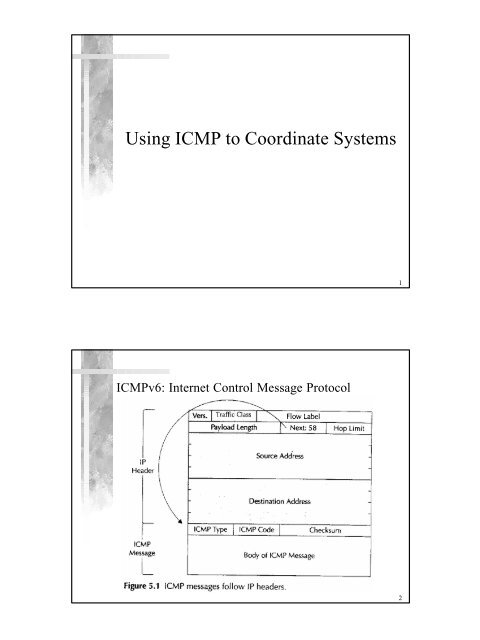
<strong>Using</strong> <strong>ICMP</strong> <strong>to</strong> <strong>Coordinate</strong> <strong>Systems</strong>1<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>col2
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colErrormessages(1-127)Informationalmessages3<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colChecksumcalculation4
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colBy including the pseudo header in its checksum, <strong>ICMP</strong>protects against more than simple data corruption in transit.It also ensures that the systems’ pro<strong>to</strong>colimplementations interface correctly. Suppose IPmistakenly delivers a UDP message <strong>to</strong> <strong>ICMP</strong>. Since thepseudo header includes the IP next header value and thisvalue differs for <strong>ICMP</strong> and UDP, the checksum will detectthis error.If the checksum is invalid, <strong>ICMP</strong> immediately discards suchdatagrams without further processing.5<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colSelecting a Source IP AddressRouterWhich interfaceaddress <strong>to</strong> use?<strong>ICMP</strong> standard provides four specific rules forselecting the source address.6
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colSelecting a Source IP AddressFirstThe first two rules consider <strong>ICMP</strong> replies. The sourceaddress of the reply should be the same as thedestination address of the original (request) message.SecondIf the original message was sent <strong>to</strong> a multicast or anycastgroup, then the response should use as its source the IPaddress of the interface on which the request arrived.7<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colSelecting a Source IP AddressThe third rule applies <strong>to</strong> <strong>ICMP</strong> error messages.Error messages are often generated by systems that are notthe ultimate destination of the datagram in error.Therefore, it cannot use the original destination as theerror’s source. Instead, they should use a source addressthat provides the most information about error beingreported.For example, if the <strong>ICMP</strong> message is a Packet Too Bigerror, then its source should be the IP address of theinterface over which the original datagram would notfit.8
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colSelecting a Source IP AddressUnsolicited <strong>ICMP</strong> messages, as well as those not coveredpreviously, follow the fourth rule. The source address forsuch messages should be an IP address of the link on whichthe message is transmitted.Neighbor discovery also constrains the destinationaddress of its <strong>ICMP</strong> messages. That destination must be alink-local address. (If the destination is multicast, then themulticast address must be of link-local scope.) Therestriction confines neighbor discovery <strong>to</strong> the local link,protecting against an accidental (or deliberate) “leaking” ofneighbor discovery beyond its intended scope.9<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colNeighbor Discovery (ND)Neighbor discovery lets a system identify other hostsand routers on its links.<strong>Systems</strong> learn about hosts on their links so that they canforward datagrams addressed <strong>to</strong> those hosts. Hosts learnof at least one router so they can forward datagrams <strong>to</strong>systems not on their links.Nodes use the pro<strong>to</strong>col <strong>to</strong> actively keep track of whichneighbors are reachable and which are not, and <strong>to</strong> detectchanged link-layer addressesReplace ARP, <strong>ICMP</strong> Router discovery, and <strong>ICMP</strong> Redirectused in IPv410
IPv6 ND Processes• Router discovery– Discover the local hosts on an attached link– Equivalent <strong>to</strong> <strong>ICMP</strong>v4 Router discovery• Prefix discovery– Discovery the network prefix– Equivalent <strong>to</strong> <strong>ICMP</strong>v4 address mask request/reply• Parameter discovery– Discovery additional parameter (ex: link MTU,default hop limit for outgoing packet)• Address au<strong>to</strong>configuration– Configure IP address for interfaces• Address resolution– Equivalent <strong>to</strong> ARP in IPv411IPv6 ND Processes (cont.)• Next-hop determination– Destination address, or– Address of an on-link default router• Neighbor unreachable detection (NUD)• Duplicate address detection (DAD)– Determine that an address considered for use in notalready in use by a neighboring node• First-hop redirect function– Inform a host of a better first-hop IPv6 address <strong>to</strong>reach a destination– Equivalent <strong>to</strong> <strong>ICMP</strong>v4 redirect12
ND messages• 5 ND messages:– Router solicitation– Router advertisement– Neighbor solicitation– Neighbor advertisement– Redirect• All ND message are send with hop limit = 255– If it is not set <strong>to</strong> 255, the message is silentlydiscarded– Provide protection from ND-based network attackslaunched from off-link nodes– Router can not have forwarded the ND message froman off-link node13<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colNeighbor Discovery14
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colNeighbor DiscoveryLink-local address15<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colAddress ResolutionNeighbordiscovery comesin<strong>to</strong> play withthe first IPdatagram sentacross thenetwork (do theARP function).Suppose that theworkstationmust send adatagram <strong>to</strong> thePC.multicasti.e. ARP function16
<strong>ICMP</strong>v6: Internet Control Message Pro<strong>to</strong>colAddress ResolutionIf the workstation fails <strong>to</strong> get a response <strong>to</strong> its solicitation, itmay repeat the request an many as nine additional times. Toavoid straining the network, though, successive requests mustbe at least one second apart.(Fig. 5.5 The Neighbor solicitation message,the Hops = 255, if received the message which Hops lessthan 255 è the message has processed by router. i.e. Themessage go out of local link range, discard itDA IP is multicast address which appends the last 32-bit ofthe PC IP address <strong>to</strong> the 96-bit prefix FF02::1:0:0.)17<strong>ICMP</strong>v618
R=1: sent by routerS=1: responding <strong>to</strong> asolicitationO=1: Override cacheentry and update thecached link-layeraddress<strong>ICMP</strong>v6OTarget linkaddress optionReply <strong>to</strong> the neighbor solicitation19<strong>ICMP</strong>v6Router Discovery (Router sends router advertisementpacket <strong>to</strong> the hosts on the link20
Router Advertisement MessageUse DHCP forIP address(Managedaddressconfiguration)Link-local multicastConfiguration for otherinformation21Router’s22
Possible options for router advertisementsSource link-layer addressThe link-layer address of the interface fromwhich the Router Advertisement is sent. Only used on linklayers that have addresses.MTU SHOULD be sent on links that have a variableMTU (as specified in the document that describes how <strong>to</strong>run IP over the particular link type). MAY be sent onother links.Prefix InformationThese options specify the prefixes that are onlink(net-ID) and/or are used for address au<strong>to</strong>configuration.23<strong>ICMP</strong>v6Router advertisement formatMax hops (255): recommend a maximum hop limit for anydatagram a host transmits, 0 means unspecifiedreachability timeout: suggest a time limit <strong>to</strong> place on neighborinformation that a host learns, If a host fails <strong>to</strong> hear from aneighbor within this time period, it can suspect that theneighbor is no longer reachable (time in milliseconds)reachability retransmission interval: limit the frequency ofneighbor solicitations for a destination (time in milliseconds)router lifetime: determine how long hosts should consider thesource of this message available (time in seconds). If this timeinterval passes without another router advertisement, hostsview the router as unavailable24
<strong>ICMP</strong>v6Router advertisement formatAn option defines a prefix address for the link. Links mayhave multiple prefixes, and thus router advertisementsmay include several options of this type.Routers advertise prefixes for two different reasons. First,they indicate which IP addresses refer <strong>to</strong> systems on thelink. If a destination IP address does not match a link’sprefix, the system is not on the link. Reaching thisdestination requires the services of a router. Prefixextensions used <strong>to</strong> indicate this information have the L bitset. Prefixes may also play a role in addressau<strong>to</strong>configuration. These prefixes have the A bit set.25<strong>ICMP</strong>v6Router advertisement formatvalid lifetime: determine how long the prefix will remainvalid, in the absence of further advertisements.preferred lifetime: used only for address au<strong>to</strong>configuration,indicate the number of seconds before a prefix becomeobsolete. An obsolete prefix may still be used so long as itsvalid lifetime has not expired.(Use 0xFFFFFFFF for infinite lifetime.)26
<strong>ICMP</strong>v6Router solicitation message27<strong>ICMP</strong>v6RoutersolicitationmessageWhen a routerresponds <strong>to</strong> asolicitation, itdoes so bysending a routeradvertisementdirectly <strong>to</strong> thesystem makingthe request (useunicast, notmulticast .All routers address28
<strong>ICMP</strong>v6RedirectionRouters solicitations and advertisements let a host find arouter, but they do not guarantee that a host finds thebest router for a particular destination.?29<strong>ICMP</strong>v6RedirectionMake the wrong choiceThe left router can most easily detect the problem. Thissituation calls for an <strong>ICMP</strong> redirect message, which tells thehost of a more efficient path <strong>to</strong> a particular destination.30
<strong>ICMP</strong>v6Redirection31<strong>ICMP</strong>v6Redirection32
<strong>ICMP</strong>v6RedirectionCopy oforiginaldatagramincluded128033<strong>ICMP</strong>v6Neighbor discovery : address resolution, routerdiscovery, and redirectionDetection the loss of a neighborEven on healthy networks, neighbors do not remainpresent indefinitely. Hardware can fail, a system maychange its interface card, or a mobile system can move <strong>to</strong> anew link. When these changes occur, systems mustrecognize the new <strong>to</strong>pology and react appropriately. Theprocess by which systems learn of these changes isneighbor unreachability detection (NUD).34
<strong>ICMP</strong>v6Detection the loss of a neighborAs long as the local system has traffic <strong>to</strong> send <strong>to</strong> aneighbor, <strong>ICMP</strong> periodically probes the neighbor bysending it neighbor solicitations. If the neighbor respondswith a neighbor advertisement, and the advertisement hasthe S bit set (reply <strong>to</strong> solicitation), the neighbor remainsreachable. If the bit is clear, then the advertisement isunsolicited, and there is no guarantee that the neighboractually heard the solicitation (the path may be one-way).35<strong>ICMP</strong>v6Detection the loss of a neighborThe other bit in neighbor advertisements, the R bit, alsohas a role in NUD. When a host hears a neighboradvertisement from a system it believes <strong>to</strong> be a router, itshould check this bit. If the bit is clear, then theneighbor is no longer acting as a router. The localsystem should refrain from using this neighbor <strong>to</strong> forwardtraffic <strong>to</strong> distant destinations.36
<strong>ICMP</strong>v6Address Au<strong>to</strong>configurationIPv6 provides two ways <strong>to</strong> ease the administration of IPaddresses. The standards name them stateless addressau<strong>to</strong>configuration and stateful address configuration.The stateful approach relies on the Dynamic HostConfiguration Pro<strong>to</strong>col. Stateless configuration is<strong>ICMP</strong>’s responsibility.37<strong>ICMP</strong>v6Address Au<strong>to</strong>configurationTo insure that all configured addresses are likely <strong>to</strong> beunique on a given link, nodes run a "duplicate addressdetection" algorithm on addresses before assigning them <strong>to</strong>an interface. The Duplicate Address Detection algorithm isperformed on all addresses, independent of whether they areobtained via stateless or stateful au<strong>to</strong>configuration.38
<strong>ICMP</strong>v6Address Au<strong>to</strong>configuration39<strong>ICMP</strong>v6Address Au<strong>to</strong>configurationFlags in Router AdvertisementsM If set, hosts should not use address au<strong>to</strong>configuration,instead, they should rely on DHCP <strong>to</strong> determinetheir IP addressOIf set, hosts can use address au<strong>to</strong>configuration, butshould use DHCP for other configuration information40
<strong>ICMP</strong>v6Group Membership (Multicast Listener Query messages,like IGMP for IPv4)In addition <strong>to</strong> administering unicast IP addresses, <strong>ICMP</strong>also manages group addresses. It provides a way forsystems <strong>to</strong> announce (and later renounce) their membershipin groups. Routers listen <strong>to</strong> these messages <strong>to</strong> trackgroup membership on the link. They can then knowwhether <strong>to</strong> forward datagrams addresses <strong>to</strong> specific groups.All group membership messages have the same format,but each message has its own <strong>ICMP</strong> type.41<strong>ICMP</strong>v6GroupMembershipType:130: Query131: Report (join,reply <strong>to</strong> query)132: Termination(leave)42
<strong>ICMP</strong>v6Group MembershipIn most cases, the messages are sent <strong>to</strong> the group address inquestion. The destination IP address will then be the same asthe multicast IP address in the message body. It is alsopossible <strong>to</strong> query for membership in all groups. In suchcases, the destination address is the All nodes address(FF02::1, local-link multicast), and the IP multicast addressis set <strong>to</strong> zero.maximum response delay (milliseconds): the maximumamount of time that a system may delay beforeresponding <strong>to</strong> the query. To prevent every group memberfrom responding simultaneously, each should delay arandom amount of time ranging from zero <strong>to</strong> the MRD.43<strong>ICMP</strong>v6Error ReportingHops:3Hops:2Hops:144
<strong>ICMP</strong>v6Error Reporting<strong>ICMP</strong> timeexceeded error45<strong>ICMP</strong>v6Error ReportingTo avoid choking a network with error messages, <strong>ICMP</strong> hasspecific rules that define when error messages arepermissible.46
<strong>ICMP</strong>v6Error Reporting:DestinationUnreachable128047<strong>ICMP</strong>v6Error Reporting: Destination UnreachableRouting table can’t find a routeEX: firewallLayer 2 unreachableLayer 4 unreachable48
<strong>ICMP</strong>v6Error Reporting: Packet Too Big8000 bytesPacket <strong>to</strong>o bigUnlike IPv4, fragmentation in IPv6 is performed only bysource nodes, not by routers along a packet's delivery path.49<strong>ICMP</strong>v6ErrorReporting:Packet TooBigActual MTU ofthe link thatcaused theproblem128050
<strong>ICMP</strong>v6Error Reporting: Time ExceededSystem generate Time Exceeded messages for tworeasons:1. Exhaustion of a datagram’s hop limit2. A system fails <strong>to</strong> complete reassembly of datagramfragments in a reasonable amount of time. This time limitshould range between 60 and 120 seconds. To avoidgenerating a lot of error messages for the same datagram,systems should only generate this error if the fragmentsthey have received include the fragment at offset zero.Once a system returns this Time Exceeded error, it shoulddiscard the fragments that it has been retaining.51<strong>ICMP</strong>v6ErrorReporting:TimeExceeded0: hop limitexhausted1: reassemblytime expired128052
<strong>ICMP</strong>v6Parameter Problemsend by router ordestination host whenerrors of IPv6 header orextension header0: invalidheader field1: unrecognizednext headervalue2: unrecognizedoption128053<strong>ICMP</strong>v6NetworkDiagnostics54
<strong>ICMP</strong>v6NetworkDiagnostics55