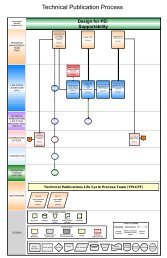
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
NAVSO P-5239-04SEPTEMBER 1995working effectively.The <strong>ISSM</strong> is responsible for ensuring that the ST&Erequirements to support the DAA’s IS accreditation decision foreach Command IS processing classified or otherwise sensitiveinformation are satisfied. This entails the following activities:· Identifying qualified individuals to perform the ST&Eactivities· Coordinating the IS Risk Assessment review to ensure thecurrency and accuracy of risks and identifiedcountermeasures· Identifying how the effectiveness of each countermeasurewill be determined. Countermeasures will need to beindicated as well as the method of testing (e.g., scenarios,inspections, documentation and procedure review) to beimplemented for each countermeasure· Executing the ST&E plan and documenting the results inan ST&E report. This report should include either:- A recommendation to the DAA to accredit or notaccredit the IS or network or grant an interim authorityto operate based on the level of risk identified by theST&E team- A recommendation regarding security deficiencies, ifnonaccreditation is recommended.Reference: For more information concerning ST&Edocumentation see section 11, Documentation. Also seeNAVSO P-5239-18, <strong>Security</strong> Test and Evaluation Guidebook.IS ModificationsThe IS environment requires constant review to ensure thesecurity features are providing the required protection. Changesto any IS affect security. Changes to security can affect theaccreditation status of the IS.The <strong>ISSM</strong> ensures the review of any planned changes ormodifications to the IS to assess the impact to the overallsecurity of the system. Types of changes that can affect securityinclude, but are not limited to:· Changes in the level and type of data being processed· Redesigns of the application software16