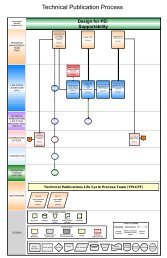
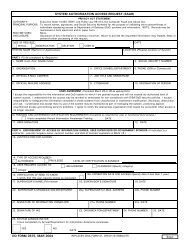
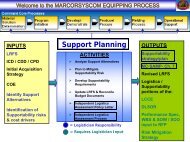
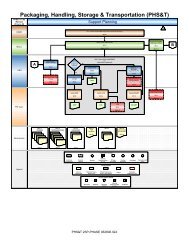
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
NAVSO P-5239-04SEPTEMBER 1995NCSC-TG-001 , A Guide to Understanding Audit in Trusted <strong>Systems</strong>, Version 2, 1 June1988.This document provides a set of good practices related to the use of auditing in automatic dataprocessing systems employed for processing classified and other sensitive information.*NCSC-TG-003 , A Guide To Understanding Discretionary Access Control In Trusted<strong>Systems</strong>, Version 1, 30 September 1987.This document discusses issues involved in designing, implementing, and evaluating DACmechanisms. Its primary purpose is to provide guidance to manufacturers on how to selectand build effective DAC mechanisms.NCSC-TG-005 , Trusted Network Interpretation of the Trusted Computer System EvaluationCriteria, National Computer <strong>Security</strong> Center, Version 1 , July 1987.The TNI or "Red" Book" was issued by the National Computer <strong>Security</strong> Center (NCSC) aspart of its program to promulgate technical computer security guidelines. The interpretationextends the evaluation classes of the "Orange Book" to trusted network systems andcomponents.NCSC-TG-017 , A Guide To Understanding Identification And Authentication In Trusted<strong>Systems</strong>, Version 1, September 1991.This document provides guidance to vendors on how to design and incorporate effectiveidentification and authentication (I&A) mechanisms into their systems. It also aids vendorsand evaluators in understanding I&A requirements.*NCSC-TG-027 , A Guide to Understanding <strong>Information</strong> System <strong>Security</strong> OfficerResponsibilities for Automated <strong>Information</strong> <strong>Systems</strong>, National Computer <strong>Security</strong> Center,Version 1, May 1992.This document helps ISSOs understand their responsibilities for implementing andmaintaining security in a system. This guideline also discusses the roles and responsibilitiesof other individuals who are responsible for security and their relationship to the ISSO, asdefined in various component regulation and standards.NCSC-TG-028 , Assessing Controlled Access Protection, Version 1, 25 May 1992.This document explains the controlled access protection requirements of the TrustedComputer System Evaluation Criteria.A-6