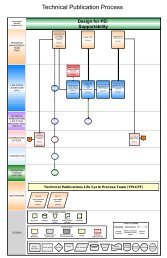
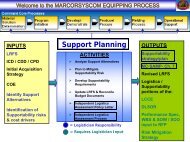
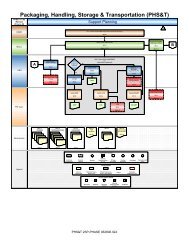
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
NAVSO P-5239-04SEPTEMBER 19953.9 <strong>Security</strong> Configuration ManagementAfter security is established for an IS, strict measures must be enforced to ensure thatchanges to the IS do not disrupt this balance. Even seemingly minor changes may result insevere implications to the security of the system. Configuration management controlschanges to system software, firmware, hardware, and documentation throughout the life of theIS. This includes the design, development, testing, distribution, and operation ofmodifications and enhancements to the existing IS.ResponsibilityIn accordance with the DAA’s policies and procedures forcontrolling changes to the IS, the <strong>ISSM</strong> provide s input to ISconfiguration management activities to ensure that implementedchanges do not compromise the security of the system. In thiscapacity, the <strong>ISSM</strong> provides security oversight, guidance, andinput to system and network administrators, SSAs, ISEAs, andother activities responsible for implementing changes to the IS.The <strong>ISSM</strong> may delegate security-related configurationmanagement activities to ISSOs or NSOs as appropriate for thespecific Command.ImplementationThe <strong>ISSM</strong> is responsible for ensuring that the following tasks areconducted:· IS inventory is reviewed regularly. Although the systemor network administrator usually develops and maintainsthe inventory of the IS, the <strong>ISSM</strong> must closely monitorthis effort to ensure that system components have notchanged, been moved, or otherwise been tampered within any way that may impact the overall security of the IS· Documentation detailing the IS hardware, software, andfirmware configuration and security features ismaintained· IS change proposals are reviewed according to thefollowing criteria:- How will the change impact the security of the IS?- If new software is proposed, is it from an authorizedsource?- Have security features and mechanisms beenconsidered and included in system change plans?- Do system support personnel know how to install andmaintain new security features/mechanisms?- Will reaccreditation be necessary?36