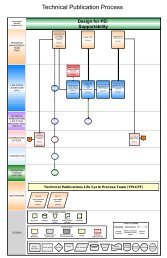
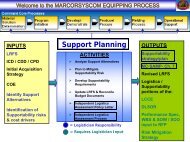
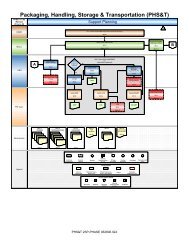
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
Information Systems Security Manager (ISSM) - Marine Corps ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
NAVSO P-5239-04SEPTEMBER 1995TABLE OF CONTENTS<strong>Security</strong> Awareness........................................................................................................................... 263.6 Physical <strong>Security</strong>............................................................................................................ 28Responsibility ....................................................................................................................................... 28Implementation ..................................................................................................................................... 28Facility Access.................................................................................................................................. 28User Identification and Authentication ............................................................................................. 29Data Access ...................................................................................................................................... 29Environmental Hazards Protection ................................................................................................... 29TEMPEST ........................................................................................................................................ 303.7 Auditing ......................................................................................................................... 32Responsibility ....................................................................................................................................... 32Implementation ..................................................................................................................................... 32Audit Procedures .............................................................................................................................. 32Audit Trail ........................................................................................................................................ 323.8 Incident and Violations Reporting ................................................................................. 34Responsibility ....................................................................................................................................... 34Implementation ..................................................................................................................................... 34Incident Reporting Mechanism ......................................................................................................... 34Incident Analysis .............................................................................................................................. 35<strong>Security</strong> Vulnerabilities and Problems .............................................................................................. 353.9 <strong>Security</strong> Configuration Management ............................................................................. 36Responsibility ....................................................................................................................................... 36Implementation ..................................................................................................................................... 363.10 Contingency Planning ..................................................................................................38Responsibility ....................................................................................................................................... 38Implementation ..................................................................................................................................... 383.11 <strong>Security</strong> Documentation............................................................................................... 40Activity INFOSEC Plan (ISSP) ............................................................................................................. 40System <strong>Security</strong> Plan............................................................................................................................. 40Risk Assessment ................................................................................................................................... 41ST&E Documentation ........................................................................................................................... 41Activity Accreditation Schedule (AAS) ................................................................................................ 43IS Incident Report ................................................................................................................................. 43Authorized User List ............................................................................................................................. 43<strong>Security</strong> Operating Procedures .............................................................................................................. 43Training and Awareness Documentation ............................................................................................... 43Contingency Plan .................................................................................................................................. 44APPENDIX -- <strong>Security</strong> Policy, Procedure, and Guidance DocumentationA-1iv