Working with Data in ASP.NET 2.0 :: Protecting Connection Strings ...
Working with Data in ASP.NET 2.0 :: Protecting Connection Strings ...
Working with Data in ASP.NET 2.0 :: Protecting Connection Strings ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
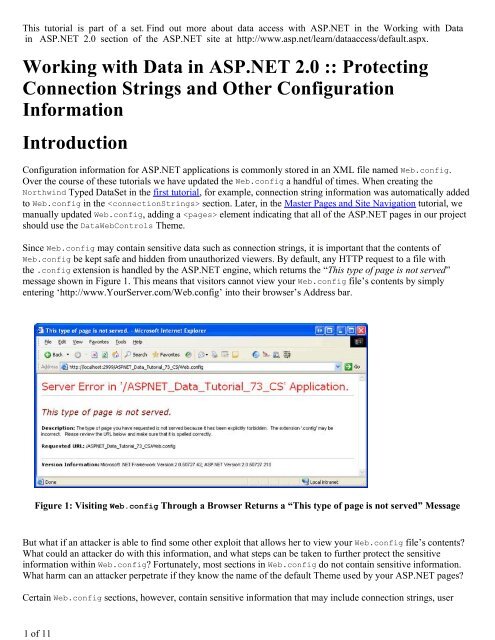
1 of 11This tutorial is part of a set. F<strong>in</strong>d out more about data access <strong>with</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>in</strong> the <strong>Work<strong>in</strong>g</strong> <strong>with</strong> <strong>Data</strong><strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> section of the <strong>ASP</strong>.<strong>NET</strong> site at http://www.asp.net/learn/dataaccess/default.aspx.<strong>Work<strong>in</strong>g</strong> <strong>with</strong> <strong>Data</strong> <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> :: Protect<strong>in</strong>g<strong>Connection</strong> Str<strong>in</strong>gs and Other ConfigurationInformationIntroductionConfiguration <strong>in</strong>formation for <strong>ASP</strong>.<strong>NET</strong> applications is commonly stored <strong>in</strong> an XML file named Web.config.Over the course of these tutorials we have updated the Web.config a handful of times. When creat<strong>in</strong>g theNorthw<strong>in</strong>d Typed <strong>Data</strong>Set <strong>in</strong> the first tutorial, for example, connection str<strong>in</strong>g <strong>in</strong>formation was automatically addedto Web.config <strong>in</strong> the section. Later, <strong>in</strong> the Master Pages and Site Navigation tutorial, wemanually updated Web.config, add<strong>in</strong>g a element <strong>in</strong>dicat<strong>in</strong>g that all of the <strong>ASP</strong>.<strong>NET</strong> pages <strong>in</strong> our projectshould use the <strong>Data</strong>WebControls Theme.S<strong>in</strong>ce Web.config may conta<strong>in</strong> sensitive data such as connection str<strong>in</strong>gs, it is important that the contents ofWeb.config be kept safe and hidden from unauthorized viewers. By default, any HTTP request to a file <strong>with</strong>the .config extension is handled by the <strong>ASP</strong>.<strong>NET</strong> eng<strong>in</strong>e, which returns the “This type of page is not served”message shown <strong>in</strong> Figure 1. This means that visitors cannot view your Web.config file’s contents by simplyenter<strong>in</strong>g ‘http://www.YourServer.com/Web.config’ <strong>in</strong>to their browser’s Address bar.Figure 1: Visit<strong>in</strong>g Web.config Through a Browser Returns a “This type of page is not served” MessageBut what if an attacker is able to f<strong>in</strong>d some other exploit that allows her to view your Web.config file’s contents?What could an attacker do <strong>with</strong> this <strong>in</strong>formation, and what steps can be taken to further protect the sensitive<strong>in</strong>formation <strong>with</strong><strong>in</strong> Web.config? Fortunately, most sections <strong>in</strong> Web.config do not conta<strong>in</strong> sensitive <strong>in</strong>formation.What harm can an attacker perpetrate if they know the name of the default Theme used by your <strong>ASP</strong>.<strong>NET</strong> pages?Certa<strong>in</strong> Web.config sections, however, conta<strong>in</strong> sensitive <strong>in</strong>formation that may <strong>in</strong>clude connection str<strong>in</strong>gs, user
2 of 11names, passwords, server names, encryption keys, and so forth. This <strong>in</strong>formation is typically found <strong>in</strong> the follow<strong>in</strong>gWeb.config sections:• • • • In this tutorial we will look at techniques for protect<strong>in</strong>g such sensitive configuration <strong>in</strong>formation. As we will see,the .<strong>NET</strong> Framework version <strong>2.0</strong> <strong>in</strong>cludes a protected configurations system that makes programmaticallyencrypt<strong>in</strong>g and decrypt<strong>in</strong>g selected configuration sections a breeze.Note: This tutorial concludes <strong>with</strong> a look at Microsoft’s recommendations for connect<strong>in</strong>g to a database froman <strong>ASP</strong>.<strong>NET</strong> application. In addition to encrypt<strong>in</strong>g your connection str<strong>in</strong>gs, you can help harden your systemby ensur<strong>in</strong>g that you are connect<strong>in</strong>g to the database <strong>in</strong> a secure fashion.Step 1: Explor<strong>in</strong>g <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong>’s Protected Configuration Options<strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> <strong>in</strong>cludes a protected configuration system for encrypt<strong>in</strong>g and decrypt<strong>in</strong>g configuration <strong>in</strong>formation.This <strong>in</strong>cludes methods <strong>in</strong> the .<strong>NET</strong> Framework that can be used to programmatically encrypt or decryptconfiguration <strong>in</strong>formation. The protected configuration system uses the provider model, which allows developers tochoose what cryptographic implementation is used.The .<strong>NET</strong> Framework ships <strong>with</strong> two protected configuration providers:• RSAProtectedConfigurationProvider uses the asymmetric RSA algorithm for encryption anddecryption.• DPAPIProtectedConfigurationProvider uses the W<strong>in</strong>dows <strong>Data</strong> Protection API (DPAPI) for encryptionand decryption.S<strong>in</strong>ce the protected configuration system implements the provider design pattern, it is possible to create your ownprotected configuration provider and plug it <strong>in</strong>to your application. See Implement<strong>in</strong>g a Protected ConfigurationProvider for more <strong>in</strong>formation on this process.The RSA and DPAPI providers use keys for their encryption and decryption rout<strong>in</strong>es, and these keys can be storedat the mach<strong>in</strong>e or userlevel. Mach<strong>in</strong>elevel keys are ideal for scenarios where the web application runs on its owndedicated server or if there are multiple applications on a server that need to share encrypted <strong>in</strong>formation. Userlevelkeys are a more secure option <strong>in</strong> shared host<strong>in</strong>g environments where other applications on the same servershould not be able to decrypt your application’s protected configuration sections.In this tutorial our examples will use the DPAPI provider and mach<strong>in</strong>elevel keys. Specifically, we will look atencrypt<strong>in</strong>g the section <strong>in</strong> Web.config, although the protected configuration system can beused to encrypt most any Web.config section. For <strong>in</strong>formation on us<strong>in</strong>g userlevel keys or us<strong>in</strong>g the RSA provider,consult the resources <strong>in</strong> the Further Read<strong>in</strong>gs section at the end of this tutorial.Note: The RSAProtectedConfigurationProvider and DPAPIProtectedConfigurationProviderproviders are registered <strong>in</strong> the mach<strong>in</strong>e.config file <strong>with</strong> the provider namesRsaProtectedConfigurationProvider and <strong>Data</strong>ProtectionConfigurationProvider, respectively.When encrypt<strong>in</strong>g or decrypt<strong>in</strong>g configuration <strong>in</strong>formation we will need to supply the appropriate providername (RsaProtectedConfigurationProvider or <strong>Data</strong>ProtectionConfigurationProvider) rather thanthe actual type name (RSAProtectedConfigurationProvider andDPAPIProtectedConfigurationProvider). You can f<strong>in</strong>d the mach<strong>in</strong>e.config file <strong>in</strong> the$WINDOWS$\Microsoft.<strong>NET</strong>\Framework\version\CONFIG folder.
3 of 11Step 2: Programmatically Encrypt<strong>in</strong>g and Decrypt<strong>in</strong>g ConfigurationSectionsWith a few l<strong>in</strong>es of code we can encrypt or decrypt a particular configuration section us<strong>in</strong>g a specified provider.The code, as we will see shortly, simply needs to programmatically reference the appropriate configuration section,call its ProtectSection or UnprotectSection method, and then call the Save method to persist the changes.Moreover, the .<strong>NET</strong> Framework <strong>in</strong>cludes a helpful command l<strong>in</strong>e utility that can encrypt and decrypt configuration<strong>in</strong>formation. We will explore this command l<strong>in</strong>e utility <strong>in</strong> Step 3.To illustrate programmatically protect<strong>in</strong>g configuration <strong>in</strong>formation, let’s create an <strong>ASP</strong>.<strong>NET</strong> page that <strong>in</strong>cludesbuttons for encrypt<strong>in</strong>g and decrypt<strong>in</strong>g the section <strong>in</strong> Web.config.Start by open<strong>in</strong>g the Encrypt<strong>in</strong>gConfigSections.aspx page <strong>in</strong> the AdvancedDAL folder. Drag a TextBox controlfrom the Toolbox onto the Designer, sett<strong>in</strong>g its ID property to WebConfigContents, its TextMode property toMultiL<strong>in</strong>e, and its Width and Rows properties to 95% and 15, respectively. This TextBox control will display thecontents of Web.config allow<strong>in</strong>g us to quickly see if the contents are encrypted or not. Of course, <strong>in</strong> a realapplication you would never want to display the contents of Web.config.Beneath the TextBox, add two Button controls named EncryptConnStr<strong>in</strong>gs and DecryptConnStr<strong>in</strong>gs. Set theirText properties to “Encrypt <strong>Connection</strong> Str<strong>in</strong>gs” and “Decrypt <strong>Connection</strong> Str<strong>in</strong>gs”.At this po<strong>in</strong>t your screen should look similar to Figure 2.
4 of 11Figure 2: Add a TextBox and Two Button Web Controls to the PageNext, we need to write code that loads and displays the contents of Web.config <strong>in</strong> the WebConfigContentsTextBox when the page is first loaded. Add the follow<strong>in</strong>g code to the page’s codebeh<strong>in</strong>d class. This code adds amethod named DisplayWebConfig and calls it from the Page_Load event handler when Page.IsPostBack isfalse:protected void Page_Load(object sender, EventArgs e){// On the first page visit, call DisplayWebConfig methodif (!Page.IsPostBack)DisplayWebConfig();}private void DisplayWebConfig(){// Reads <strong>in</strong> the contents of Web.config and displays them <strong>in</strong> the TextBoxStreamReader webConfigStream =File.OpenText(Path.Comb<strong>in</strong>e(Request.PhysicalApplicationPath, "Web.config"));str<strong>in</strong>g configContents = webConfigStream.ReadToEnd();webConfigStream.Close();}WebConfigContents.Text = configContents;The DisplayWebConfig method uses the File class to open the application’s Web.config file, the StreamReaderclass to read its contents <strong>in</strong>to a str<strong>in</strong>g, and the Path class to generate the physical path to the Web.config file.These three classes are all found <strong>in</strong> the System.IO namespace. Consequently, you will need to add a us<strong>in</strong>gSystem.IO statement to the top of the codebeh<strong>in</strong>d class or, alternatively, prefix these class names <strong>with</strong>“System.IO.”.Next, we need to add event handlers for the two Button controls’ Click events and add the necessary code toencrypt and decrypt the section us<strong>in</strong>g a mach<strong>in</strong>elevel key <strong>with</strong> the DPAPI provider. Fromthe Designer, doubleclick each of the Buttons to add a Click event handler <strong>in</strong> the codebeh<strong>in</strong>d class and then addthe follow<strong>in</strong>g code:protected void EncryptConnStr<strong>in</strong>gs_Click(object sender, EventArgs e){// Get configuration <strong>in</strong>formation about Web.configConfiguration config =WebConfigurationManager.OpenWebConfiguration(Request.ApplicationPath);// Let's work <strong>with</strong> the sectionConfigurationSection connectionStr<strong>in</strong>gs = config.GetSection("connectionStr<strong>in</strong>gs");if (connectionStr<strong>in</strong>gs != null)// Only encrypt the section if it is not already protectedif (!connectionStr<strong>in</strong>gs.SectionInformation.IsProtected){// Encrypt the section us<strong>in</strong>g the// <strong>Data</strong>ProtectionConfigurationProvider providerconnectionStr<strong>in</strong>gs.SectionInformation.ProtectSection("<strong>Data</strong>ProtectionConfigurationProvider");config.Save();
5 of 11}}// Refresh the Web.config displayDisplayWebConfig();protected void DecryptConnStr<strong>in</strong>gs_Click(object sender, EventArgs e){// Get configuration <strong>in</strong>formation about Web.configConfiguration config =WebConfigurationManager.OpenWebConfiguration(Request.ApplicationPath);// Let's work <strong>with</strong> the sectionConfigurationSection connectionStr<strong>in</strong>gs =config.GetSection("connectionStr<strong>in</strong>gs");if (connectionStr<strong>in</strong>gs != null)// Only decrypt the section if it is protectedif (connectionStr<strong>in</strong>gs.SectionInformation.IsProtected){// Decrypt the sectionconnectionStr<strong>in</strong>gs.SectionInformation.UnprotectSection();config.Save();}}// Refresh the Web.config displayDisplayWebConfig();The code used <strong>in</strong> the two event handlers is nearly identical. They both start by gett<strong>in</strong>g <strong>in</strong>formation about the currentapplication’s Web.config file via the WebConfigurationManager class’s OpenWebConfiguration method. Thismethod returns the web configuration file for the specified virtual path. Next, the Web.config file’s section is accessed via the Configuration class’s GetSection(sectionName) method,which returns a ConfigurationSection object.The ConfigurationSection object <strong>in</strong>cludes a SectionInformation property that provides additional<strong>in</strong>formation and functionality regard<strong>in</strong>g the configuration section. As the code above shows, we can determ<strong>in</strong>ewhether the configuration section is encrypted by check<strong>in</strong>g the SectionInformation property’s IsProtectedproperty. Moreover, the section can be encrypted or decrypted via the SectionInformation property’sProtectSection(provider) and UnprotectSection methods.The ProtectSection(provider) method accepts as <strong>in</strong>put a str<strong>in</strong>g specify<strong>in</strong>g the name of the protectedconfiguration provider to use when encrypt<strong>in</strong>g. In the EncryptConnStr<strong>in</strong>g Button’s event handler we pass“<strong>Data</strong>ProtectionConfigurationProvider” <strong>in</strong>to the ProtectSection(provider) method so that the DPAPI provideris used. The UnprotectSection method can determ<strong>in</strong>e the provider that was used to encrypt the configurationsection and therefore does not require any <strong>in</strong>put parameters.After call<strong>in</strong>g the ProtectSection(provider) or UnprotectSection method, you must call the Configurationobject’s Save method to persist the changes. Once the configuration <strong>in</strong>formation has been encrypted or decryptedand the changes saved, we call DisplayWebConfig to load the updated Web.config contents <strong>in</strong>to the TextBoxcontrol.Once you have entered the above code, test it by visit<strong>in</strong>g the Encrypt<strong>in</strong>gConfigSections.aspx page through abrowser. You should <strong>in</strong>itially see a page that lists the contents of Web.config <strong>with</strong> the section displayed <strong>in</strong> pla<strong>in</strong>text (see Figure 3).
6 of 11Figure 3: Add a TextBox and Two Button Web Controls to the PageNow click the “Encrypt <strong>Connection</strong> Str<strong>in</strong>gs” button. If request validation is enabled, the markup posted back fromthe WebConfigContents TextBox will produce an HttpRequestValidationException, which displays themessage, “A potentially dangerous Request.Form value was detected from the client.” Request validation, whichis enabled by default <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong>, prohibits postbacks that <strong>in</strong>clude unencoded HTML and is designed to helpprevent script<strong>in</strong>jection attacks. This check can be disabled at the page or applicationlevel. To turn it off for thispage, set the ValidateRequest sett<strong>in</strong>g to false <strong>in</strong> the @Page directive. The @Page directive is found at the top ofthe page’s declarative markup.For more <strong>in</strong>formation on request validation, its purpose, how to disable it at the page and applicationlevel, as wellas how to HTML encode markup, see Request Validation Prevent<strong>in</strong>g Script Attacks.After disabl<strong>in</strong>g request validation for the page, try click<strong>in</strong>g the “Encrypt <strong>Connection</strong> Str<strong>in</strong>gs” button aga<strong>in</strong>. Onpostback, the configuration file will be accessed and its section encrypted us<strong>in</strong>g the DPAPIprovider. The TextBox is then updated to display the new Web.config content. As Figure 4 shows, the <strong>in</strong>formation is now encrypted.
7 of 11Figure 4: Click<strong>in</strong>g the “Encrypt <strong>Connection</strong> Str<strong>in</strong>gs” Button Encrypts the SectionThe encrypted section generated on my computer follows, although some of the content <strong>in</strong>the element has been removed for brevity:AQAAANCMnd8BFdERjHoAwE/...zChw==Note: The element specifies the provider used to perform the encryption(<strong>Data</strong>ProtectionConfigurationProvider). This <strong>in</strong>formation is used by the UnprotectSection methodwhen the “Decrypt <strong>Connection</strong> Str<strong>in</strong>gs” button is clicked.When the connection str<strong>in</strong>g <strong>in</strong>formation is accessed from Web.config either by code we write, from aSql<strong>Data</strong>Source control, or the autogenerated code from the TableAdapters <strong>in</strong> our Typed <strong>Data</strong>Sets it isautomatically decrypted. In short, we do not need to add any extra code or logic to decrypt the encrypted section. To demonstrate this, visit one of the earlier tutorials at this time, such as the SimpleDisplay tutorial from the Basic Report<strong>in</strong>g section (~/BasicReport<strong>in</strong>g/SimpleDisplay.aspx). As Figure 5shows, the tutorial works exactly as we would expect it, <strong>in</strong>dicat<strong>in</strong>g that the encrypted connection str<strong>in</strong>g <strong>in</strong>formationis be<strong>in</strong>g automatically decrypted by the <strong>ASP</strong>.<strong>NET</strong> page.
8 of 11Figure 5: The <strong>Data</strong> Access Layer Automatically Decrypts the <strong>Connection</strong> Str<strong>in</strong>g InformationTo revert the section back to its pla<strong>in</strong>text representation, click the “Decrypt <strong>Connection</strong>Str<strong>in</strong>gs” button. On postback you should see the connection str<strong>in</strong>gs <strong>in</strong> Web.config <strong>in</strong> pla<strong>in</strong>text. At this po<strong>in</strong>t yourscreen should look like it did when first visit<strong>in</strong>g this page (see <strong>in</strong> Figure 3).Step 3: Encrypt<strong>in</strong>g Configuration Sections Us<strong>in</strong>g aspnet_regiis.exeThe .<strong>NET</strong> Framework <strong>in</strong>cludes a variety of command l<strong>in</strong>e tools <strong>in</strong> the$WINDOWS$\Microsoft.<strong>NET</strong>\Framework\version\ folder. In the Us<strong>in</strong>g SQL Cache Dependencies tutorial, for<strong>in</strong>stance, we looked at us<strong>in</strong>g the aspnet_regsql.exe command l<strong>in</strong>e tool to add the <strong>in</strong>frastructure necessary forSQL cache dependencies. Another useful command l<strong>in</strong>e tool <strong>in</strong> this folder is the <strong>ASP</strong>.<strong>NET</strong> IIS Registration tool(aspnet_regiis.exe). As its name implies, the <strong>ASP</strong>.<strong>NET</strong> IIS Registration tool is primarily used to register an<strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> application <strong>with</strong> Microsoft’s professionalgrade Web server, IIS. In addition to its IISrelatedfeatures, the <strong>ASP</strong>.<strong>NET</strong> IIS Registration tool can also be used to encrypt or decrypt specified configuration sections<strong>in</strong> Web.config.The follow<strong>in</strong>g statement shows the general syntax used to encrypt a configuration section <strong>with</strong> theaspnet_regiis.exe command l<strong>in</strong>e tool:aspnet_regiis.exe pef section physical_directory prov provider
9 of 11section is the configuration section to encrypt (like “connectionStr<strong>in</strong>gs”), the physical_directory is the full,physical path to the web application’s root directory, and provider is the name of the protected configurationprovider to use (such as “<strong>Data</strong>ProtectionConfigurationProvider”). Alternatively, if the web application is registered<strong>in</strong> IIS you can enter the virtual path <strong>in</strong>stead of the physical path us<strong>in</strong>g the follow<strong>in</strong>g syntax:aspnet_regiis.exe pe section app virtual_directory prov providerThe follow<strong>in</strong>g aspnet_regiis.exe example encrypts the section us<strong>in</strong>g the DPAPIprovider <strong>with</strong> a mach<strong>in</strong>elevel key:aspnet_regiis.exe pef"connectionStr<strong>in</strong>gs" "C:\Websites\<strong>ASP</strong><strong>NET</strong>_<strong>Data</strong>_Tutorial_73_CS"prov "<strong>Data</strong>ProtectionConfigurationProvider"Similarly, the aspnet_regiis.exe command l<strong>in</strong>e tool can be used to decrypt configuration sections. Instead ofus<strong>in</strong>g the pef switch, use pdf (or <strong>in</strong>stead of pe, use pd). Also, note that the provider name is not necessarywhen decrypt<strong>in</strong>g.aspnet_regiis.exe pdf section physical_directory or aspnet_regiis.exe pd section app virtual_directoryNote: S<strong>in</strong>ce we are us<strong>in</strong>g the DPAPI provider, which uses keys specific to the computer, you must runaspnet_regiis.exe from the same mach<strong>in</strong>e from which the web pages are be<strong>in</strong>g served. For example, ifyou run this command l<strong>in</strong>e program from your local development mach<strong>in</strong>e and then upload the encryptedWeb.config file to the production server, the production server will not be able to decrypt the connectionstr<strong>in</strong>g <strong>in</strong>formation s<strong>in</strong>ce it was encrypted us<strong>in</strong>g keys specific to your development mach<strong>in</strong>e. The RSAprovider does not have this limitation as it is possible to export the RSA keys to another mach<strong>in</strong>e.Understand<strong>in</strong>g <strong>Data</strong>base Authentication OptionsBefore any application can issue SELECT, INSERT, UPDATE, or DELETE queries to a Microsoft SQL Server database,the database first must identify the requestor. This process is known as authentication and SQL Server providestwo methods of authentication:• W<strong>in</strong>dows Authentication the process under which the application is runn<strong>in</strong>g is used to communicate <strong>with</strong>the database. When runn<strong>in</strong>g an <strong>ASP</strong>.<strong>NET</strong> application through Visual Studio 2005’s <strong>ASP</strong>.<strong>NET</strong> DevelopmentServer, the <strong>ASP</strong>.<strong>NET</strong> application assumes the identity of the currently logged on user. For <strong>ASP</strong>.<strong>NET</strong>applications on Microsoft Internet Information Server (IIS), <strong>ASP</strong>.<strong>NET</strong> applications usually assume theidentity of doma<strong>in</strong>Name\Mach<strong>in</strong>eName or doma<strong>in</strong>Name\<strong>NET</strong>WORK SERVICE, although this can be customized.• SQL Authentication a user ID and password values are supplied as credentials for authentication. WithSQL authentication, the user ID and password are provided <strong>in</strong> the connection str<strong>in</strong>g.W<strong>in</strong>dows authentication is preferred over SQL authentication because it is more secure. With W<strong>in</strong>dowsauthentication the connection str<strong>in</strong>g is free from a username and password and if the web server and databaseserver reside on two different mach<strong>in</strong>es, the credentials are not sent over the network <strong>in</strong> pla<strong>in</strong>text. With SQLauthentication, however, the authentication credentials are hardcoded <strong>in</strong> the connection str<strong>in</strong>g and are transmittedfrom the web server to the database server <strong>in</strong> pla<strong>in</strong>text.These tutorials have used W<strong>in</strong>dows authentication. You can tell what authentication mode is be<strong>in</strong>g used by<strong>in</strong>spect<strong>in</strong>g the connection str<strong>in</strong>g. The connection str<strong>in</strong>g <strong>in</strong> Web.config for our tutorials has been:<strong>Data</strong> Source=.\SQLEXPRESS; AttachDbFilename=|<strong>Data</strong>Directory|\NORTHWND.MDF; Integrated
10 of 11Security=True; User Instance=TrueThe “Integrated Security=True” and lack of a username and password <strong>in</strong>dicate that W<strong>in</strong>dows authentication isbe<strong>in</strong>g used. In some connection str<strong>in</strong>gs the term “Trusted <strong>Connection</strong>=Yes” or “Integrated Security=SSPI” is used<strong>in</strong>stead of “Integrated Security=True”, but all three <strong>in</strong>dicate the use of W<strong>in</strong>dows authentication.The follow<strong>in</strong>g example shows a connection str<strong>in</strong>g that uses SQL authentication. Note the credentials embedded<strong>with</strong><strong>in</strong> the connection str<strong>in</strong>g:Server=serverName; <strong>Data</strong>base=Northw<strong>in</strong>d; uid=userID; pwd=passwordImag<strong>in</strong>e that an attacker is able to view your application’s Web.config file. If you use SQL authentication toconnect to a database that is accessible over the Internet, the attacker can use this connection str<strong>in</strong>g to connect toyour database through SQL Management Studio or from <strong>ASP</strong>.<strong>NET</strong> pages on their own website. To help mitigatethis threat, encrypt the connection str<strong>in</strong>g <strong>in</strong>formation <strong>in</strong> Web.config us<strong>in</strong>g the protected configuration system.Note: For more <strong>in</strong>formation on the different types of authentication available <strong>in</strong> SQL Server, see Build<strong>in</strong>gSecure <strong>ASP</strong>.<strong>NET</strong> Applications: Authentication, Authorization, and Secure Communication. For furtherconnection str<strong>in</strong>g examples illustrat<strong>in</strong>g the differences between W<strong>in</strong>dows and SQL authentication syntax,refer to <strong>Connection</strong>Str<strong>in</strong>gs.com.SummaryBy default, files <strong>with</strong> a .config extension <strong>in</strong> an <strong>ASP</strong>.<strong>NET</strong> application cannot be accessed through a browser.These types of files are not returned because they may conta<strong>in</strong> sensitive <strong>in</strong>formation, such as database connectionstr<strong>in</strong>gs, usernames and passwords, and so on. The protected configuration system <strong>in</strong> .<strong>NET</strong> <strong>2.0</strong> helps further protectsensitive <strong>in</strong>formation by allow<strong>in</strong>g specified configuration sections to be encrypted. There are two built<strong>in</strong> protectedconfiguration providers: one that uses the RSA algorithm and one that uses the W<strong>in</strong>dows <strong>Data</strong> Protection API(DPAPI).In this tutorial we looked at how to encrypt and decrypt configuration sett<strong>in</strong>gs us<strong>in</strong>g the DPAPI provider. This canbe accomplished both programmatically, as we saw <strong>in</strong> Step 2, as well as through the aspnet_regiis.execommand l<strong>in</strong>e tool, which was covered <strong>in</strong> Step 3. For more <strong>in</strong>formation on us<strong>in</strong>g userlevel keys or us<strong>in</strong>g the RSAprovider <strong>in</strong>stead, see the resources <strong>in</strong> the Further Read<strong>in</strong>g section.Happy Programm<strong>in</strong>g!Further Read<strong>in</strong>gFor more <strong>in</strong>formation on the topics discussed <strong>in</strong> this tutorial, refer to the follow<strong>in</strong>g resources:• Build<strong>in</strong>g Secure <strong>ASP</strong>.<strong>NET</strong> Application: Authentication, Authorization, and Secure Communication• Encrypt<strong>in</strong>g Configuration Information <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> Applications• Encrypt<strong>in</strong>g Web.config Values <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong>• How To: Encrypt Configuration Sections <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> Us<strong>in</strong>g DPAPI• How To: Encrypt Configuration Sections <strong>in</strong> <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> Us<strong>in</strong>g RSA• The Configuration API <strong>in</strong> .<strong>NET</strong> <strong>2.0</strong>• W<strong>in</strong>dows <strong>Data</strong> ProtectionAbout the Author
11 of 11Scott Mitchell, author of seven <strong>ASP</strong>/<strong>ASP</strong>.<strong>NET</strong> books and founder of 4GuysFromRolla.com, has been work<strong>in</strong>g <strong>with</strong>Microsoft Web technologies s<strong>in</strong>ce 1998. Scott works as an <strong>in</strong>dependent consultant, tra<strong>in</strong>er, and writer. His latestbook is Sams Teach Yourself <strong>ASP</strong>.<strong>NET</strong> <strong>2.0</strong> <strong>in</strong> 24 Hours. He can be reached at mitchell@4GuysFromRolla.com. orvia his blog, which can be found at http://ScottOnWrit<strong>in</strong>g.<strong>NET</strong>.Special Thanks To…This tutorial series was reviewed by many helpful reviewers. Lead reviewers for this tutorial were Teresa Murphyand Randy Schmidt. Interested <strong>in</strong> review<strong>in</strong>g my upcom<strong>in</strong>g MSDN articles? If so, drop me a l<strong>in</strong>e atmitchell@4GuysFromRolla.com.