EXPLOITING EMBEDDED SYSTEMS THE SEQUEL!
Exploitation - CanSecWest
Exploitation - CanSecWest
SHOW LESS
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
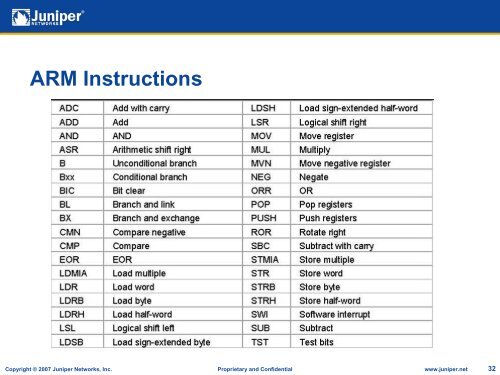
ARM InstructionsCopyright © 2007 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 32