EXPLOITING EMBEDDED SYSTEMS THE SEQUEL!
Exploitation - CanSecWest
Exploitation - CanSecWest
SHOW LESS
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
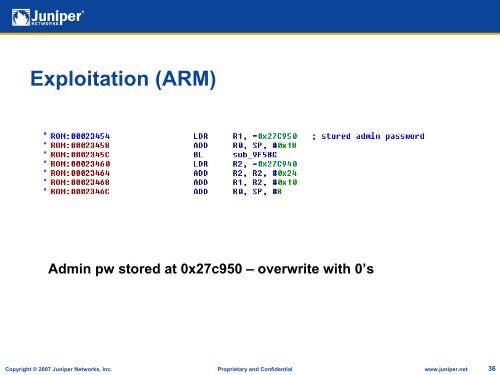
Exploitation (ARM)Admin pw stored at 0x27c950 – overwrite with 0’sCopyright © 2007 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 36