Investigation of Linux.Mirai Trojan family
u97CXm
u97CXm
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
16<br />
16<br />
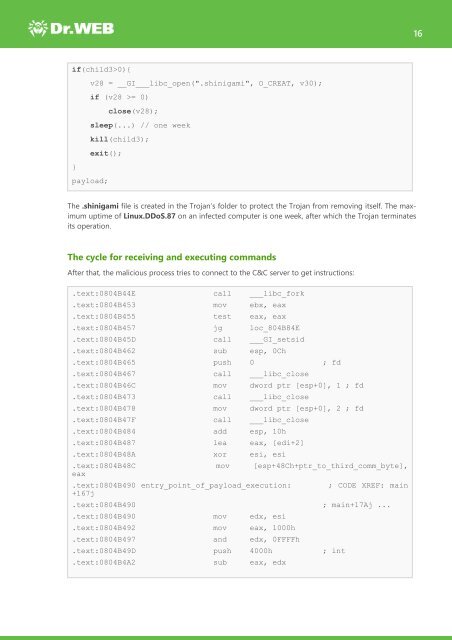
if(child3>0){<br />
v28 = __GI___libc_open(".shinigami", O_CREAT, v30);<br />
if (v28 >= 0)<br />
close(v28);<br />
sleep(...) // one week<br />
kill(child3);<br />
exit();<br />
}<br />
payload;<br />
The .shinigami file is created in the <strong>Trojan</strong>’s folder to protect the <strong>Trojan</strong> from removing itself. The maximum<br />
uptime <strong>of</strong> <strong>Linux</strong>.DDoS.87 on an infected computer is one week, after which the <strong>Trojan</strong> terminates<br />
its operation.<br />
The cycle for receiving and executing commands<br />
After that, the malicious process tries to connect to the C&C server to get instructions:<br />
.text:0804B44E call ___libc_fork<br />
.text:0804B453 mov ebx, eax<br />
.text:0804B455 test eax, eax<br />
.text:0804B457 jg loc_804B84E<br />
.text:0804B45D call ___GI_setsid<br />
.text:0804B462 sub esp, 0Ch<br />
.text:0804B465 push 0 ; fd<br />
.text:0804B467 call ___libc_close<br />
.text:0804B46C mov dword ptr [esp+0], 1 ; fd<br />
.text:0804B473 call ___libc_close<br />
.text:0804B478 mov dword ptr [esp+0], 2 ; fd<br />
.text:0804B47F call ___libc_close<br />
.text:0804B484 add esp, 10h<br />
.text:0804B487 lea eax, [edi+2]<br />
.text:0804B48A xor esi, esi<br />
.text:0804B48C mov [esp+48Ch+ptr_to_third_comm_byte],<br />
eax<br />
.text:0804B490 entry_point_<strong>of</strong>_payload_execution:<br />
+167j<br />
; CODE XREF: main<br />
.text:0804B490 ; main+17Aj ...<br />
.text:0804B490 mov edx, esi<br />
.text:0804B492 mov eax, 1000h<br />
.text:0804B497 and edx, 0FFFFh<br />
.text:0804B49D push 4000h ; int<br />
.text:0804B4A2 sub eax, edx