Investigation of Linux.Mirai Trojan family
u97CXm
u97CXm
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
44<br />
44<br />
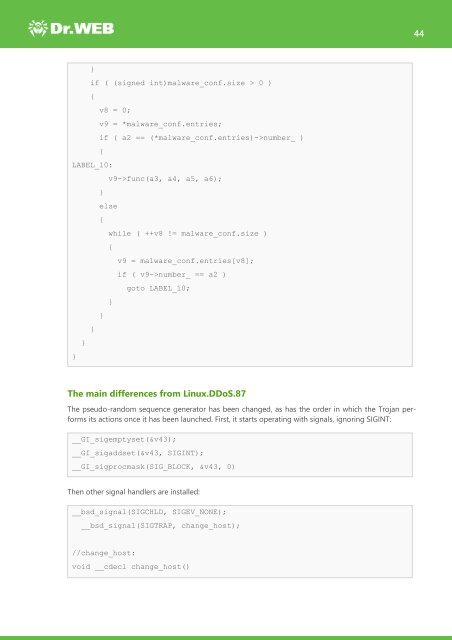
}<br />
if ( (signed int)malware_conf.size > 0 )<br />
{<br />
v8 = 0;<br />
v9 = *malware_conf.entries;<br />
if ( a2 == (*malware_conf.entries)->number_ )<br />
{<br />
LABEL_10:<br />
v9->func(a3, a4, a5, a6);<br />
}<br />
else<br />
{<br />
while ( ++v8 != malware_conf.size )<br />
{<br />
v9 = malware_conf.entries[v8];<br />
if ( v9->number_ == a2 )<br />
goto LABEL_10;<br />
}<br />
}<br />
}<br />
}<br />
}<br />
The main differences from <strong>Linux</strong>.DDoS.87<br />
The pseudo-random sequence generator has been changed, as has the order in which the <strong>Trojan</strong> performs<br />
its actions once it has been launched. First, it starts operating with signals, ignoring SIGINT:<br />
__GI_sigemptyset(&v43);<br />
__GI_sigaddset(&v43, SIGINT);<br />
__GI_sigprocmask(SIG_BLOCK, &v43, 0)<br />
Then other signal handlers are installed:<br />
__bsd_signal(SIGCHLD, SIGEV_NONE);<br />
__bsd_signal(SIGTRAP, change_host);<br />
//change_host:<br />
void __cdecl change_host()