DoD Implementation Guide for CAC PIV End-Point - Common ...
DoD Implementation Guide for CAC PIV End-Point - Common ...
DoD Implementation Guide for CAC PIV End-Point - Common ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>DoD</strong> <strong>Implementation</strong> <strong>Guide</strong> <strong>for</strong> <strong>CAC</strong> <strong>PIV</strong> <strong>End</strong>-<strong>Point</strong><br />
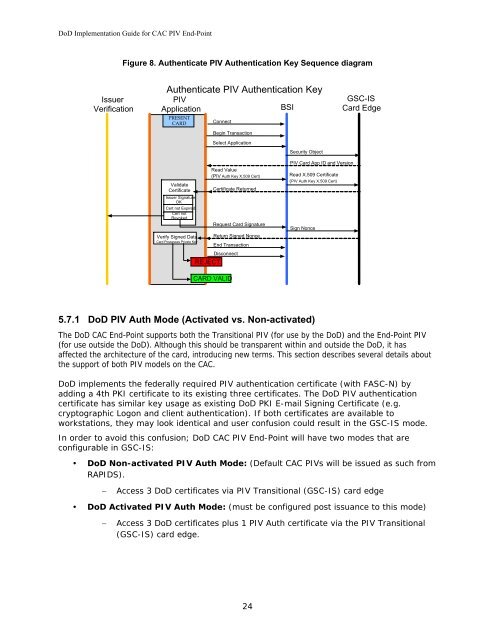
Issuer<br />
Verification<br />
Figure 8. Authenticate <strong>PIV</strong> Authentication Key Sequence diagram<br />
Authenticate <strong>PIV</strong> Authentication Key<br />
<strong>PIV</strong><br />
Application<br />
BSI<br />
PRESENT<br />
CARD<br />
Validate<br />
Certificate<br />
Issuer Signature<br />
OK<br />
Cert not Expired<br />
Cert not<br />
Revoked<br />
Connect<br />
Begin Transaction<br />
Select Application<br />
Read Value<br />
(<strong>PIV</strong> Auth Key X.509 Cert)<br />
Certificate Returned<br />
Request Card Signature<br />
Verify Signed Data Return Signed Nonce<br />
Card Possesses Private Key<br />
<strong>End</strong> Transaction<br />
Disconnect<br />
REJECT<br />
CARD VALID<br />
5.7.1 <strong>DoD</strong> <strong>PIV</strong> Auth Mode (Activated vs. Non-activated)<br />
The <strong>DoD</strong> <strong>CAC</strong> <strong>End</strong>-<strong>Point</strong> supports both the Transitional <strong>PIV</strong> (<strong>for</strong> use by the <strong>DoD</strong>) and the <strong>End</strong>-<strong>Point</strong> <strong>PIV</strong><br />
(<strong>for</strong> use outside the <strong>DoD</strong>). Although this should be transparent within and outside the <strong>DoD</strong>, it has<br />
affected the architecture of the card, introducing new terms. This section describes several details about<br />
the support of both <strong>PIV</strong> models on the <strong>CAC</strong>.<br />
<strong>DoD</strong> implements the federally required <strong>PIV</strong> authentication certificate (with FASC-N) by<br />
adding a 4th PKI certificate to its existing three certificates. The <strong>DoD</strong> <strong>PIV</strong> authentication<br />
certificate has similar key usage as existing <strong>DoD</strong> PKI E-mail Signing Certificate (e.g.<br />
cryptographic Logon and client authentication). If both certificates are available to<br />
workstations, they may look identical and user confusion could result in the GSC-IS mode.<br />
In order to avoid this confusion; <strong>DoD</strong> <strong>CAC</strong> <strong>PIV</strong> <strong>End</strong>-<strong>Point</strong> will have two modes that are<br />
configurable in GSC-IS:<br />
� <strong>DoD</strong> Non-activated <strong>PIV</strong> Auth Mode: (Default <strong>CAC</strong> <strong>PIV</strong>s will be issued as such from<br />
RAPIDS).<br />
− Access 3 <strong>DoD</strong> certificates via <strong>PIV</strong> Transitional (GSC-IS) card edge<br />
� <strong>DoD</strong> Activated <strong>PIV</strong> Auth Mode: (must be configured post issuance to this mode)<br />
− Access 3 <strong>DoD</strong> certificates plus 1 <strong>PIV</strong> Auth certificate via the <strong>PIV</strong> Transitional<br />
(GSC-IS) card edge.<br />
24<br />
Security Object<br />
<strong>PIV</strong> Card App ID and Version<br />
Read X.509 Certificate<br />
( <strong>PIV</strong> Auth Key X.509 Cert)<br />
Sign Nonce<br />
GSC-IS<br />
Card Edge