MASTER THESIS Video Watermarking - Computer Graphics Group ...
MASTER THESIS Video Watermarking - Computer Graphics Group ...
MASTER THESIS Video Watermarking - Computer Graphics Group ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
At the beginning of the entire process, the same pure watermark as in the<br />
embedding process is generated. The pure watermark is further used for<br />
correlation with the detected watermark to retrieve hidden information.<br />
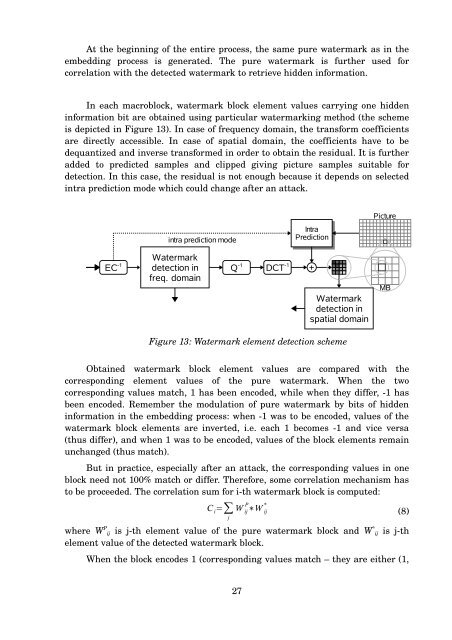
In each macroblock, watermark block element values carrying one hidden<br />
information bit are obtained using particular watermarking method (the scheme<br />
is depicted in Figure 13). In case of frequency domain, the transform coefficients<br />
are directly accessible. In case of spatial domain, the coefficients have to be<br />
dequantized and inverse transformed in order to obtain the residual. It is further<br />
added to predicted samples and clipped giving picture samples suitable for<br />
detection. In this case, the residual is not enough because it depends on selected<br />
intra prediction mode which could change after an attack.<br />
<br />
<br />
<br />
<br />
<br />
Figure 13: Watermark element detection scheme<br />
Obtained watermark block element values are compared with the<br />
corresponding element values of the pure watermark. When the two<br />
corresponding values match, 1 has been encoded, while when they differ, -1 has<br />
been encoded. Remember the modulation of pure watermark by bits of hidden<br />
information in the embedding process: when -1 was to be encoded, values of the<br />
watermark block elements are inverted, i.e. each 1 becomes -1 and vice versa<br />
(thus differ), and when 1 was to be encoded, values of the block elements remain<br />
unchanged (thus match).<br />
But in practice, especially after an attack, the corresponding values in one<br />
block need not 100% match or differ. Therefore, some correlation mechanism has<br />
to be proceeded. The correlation sum for i-th watermark block is computed:<br />
<br />
<br />
<br />
<br />
<br />
<br />
where W P ij is j-th element value of the pure watermark block and W * ij is j-th<br />
element value of the detected watermark block.<br />
When the block encodes 1 (corresponding values match – they are either (1,<br />
27<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
(8)