MASTER THESIS Video Watermarking - Computer Graphics Group ...
MASTER THESIS Video Watermarking - Computer Graphics Group ...
MASTER THESIS Video Watermarking - Computer Graphics Group ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
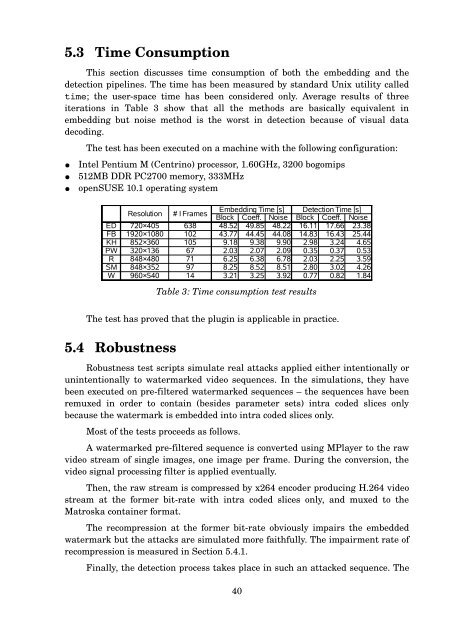
5.3 Time Consumption<br />
This section discusses time consumption of both the embedding and the<br />
detection pipelines. The time has been measured by standard Unix utility called<br />
time; the user-space time has been considered only. Average results of three<br />
iterations in Table 3 show that all the methods are basically equivalent in<br />
embedding but noise method is the worst in detection because of visual data<br />
decoding.<br />
The test has been executed on a machine with the following configuration:<br />
Intel Pentium M (Centrino) processor, 1.60GHz, 3200 bogomips<br />
512MB DDR PC2700 memory, 333MHz<br />
openSUSE 10.1 operating system<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
Table 3: Time consumption test results<br />
The test has proved that the plugin is applicable in practice.<br />
5.4 Robustness<br />
Robustness test scripts simulate real attacks applied either intentionally or<br />
unintentionally to watermarked video sequences. In the simulations, they have<br />
been executed on pre-filtered watermarked sequences – the sequences have been<br />
remuxed in order to contain (besides parameter sets) intra coded slices only<br />
because the watermark is embedded into intra coded slices only.<br />
Most of the tests proceeds as follows.<br />
A watermarked pre-filtered sequence is converted using MPlayer to the raw<br />
video stream of single images, one image per frame. During the conversion, the<br />
video signal processing filter is applied eventually.<br />
Then, the raw stream is compressed by x264 encoder producing H.264 video<br />
stream at the former bit-rate with intra coded slices only, and muxed to the<br />
Matroska container format.<br />
The recompression at the former bit-rate obviously impairs the embedded<br />
watermark but the attacks are simulated more faithfully. The impairment rate of<br />
recompression is measured in Section 5.4.1.<br />
Finally, the detection process takes place in such an attacked sequence. The<br />
40