FileMaker and HIPAA—A Tool of Compliance
FileMaker and HIPAA—A Tool of Compliance
FileMaker and HIPAA—A Tool of Compliance
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
<strong>FileMaker</strong> <strong>and</strong> <strong>HIPAA—A</strong> <strong>Tool</strong> <strong>of</strong> <strong>Compliance</strong> 2<br />
The regulations are brief, but the implementation is not. The validation process itself is an arduous<br />
adventure—not for the impatient or disorganized. For the developer working on a Part 11-compliant<br />
system, it will be helpful to keep in mind that your contributions toward obtaining FDA validation <strong>of</strong><br />
the completed system may be as critical as your role in providing its core functionality.<br />
45 CFR Parts 160, 162 & 164—HIPAA<br />
Most anyone who’s been to a medical facility lately has heard <strong>of</strong> HIPAA (<strong>of</strong>ten misspelled “HIPPA”),<br />
but few underst<strong>and</strong> its meaning or impact. So what exactly does health insurance portability <strong>and</strong><br />
accountability have to do with <strong>FileMaker</strong>? Nothing directly, but systems developed using <strong>FileMaker</strong><br />
may fall under the HIPAA umbrella. So if you use or develop <strong>FileMaker</strong>-based solutions intended for<br />
use within the medical industry, you need to know about HIPAA.<br />
In their entirety, the HIPAA regulations are sizable. The focus <strong>of</strong> this document is to assist you in<br />
meeting the requirements <strong>of</strong> a very specific portion <strong>of</strong> HIPAA known as the Security Rule (45 CFR<br />
Part 164). A brief review <strong>of</strong> the overall rule—while not essential to development—will enable you to<br />
intelligently converse on the topic with colleagues <strong>and</strong> clients.<br />
HIPAA is an extensive set <strong>of</strong> regulations enacted by Congress in 1996 <strong>and</strong> administered by the U.S.<br />
Department <strong>of</strong> Health <strong>and</strong> Human Services. HIPAA consists <strong>of</strong> five titles. Title I protects health<br />
insurance coverage for workers <strong>and</strong> their families when they change or lose their jobs (hence the<br />
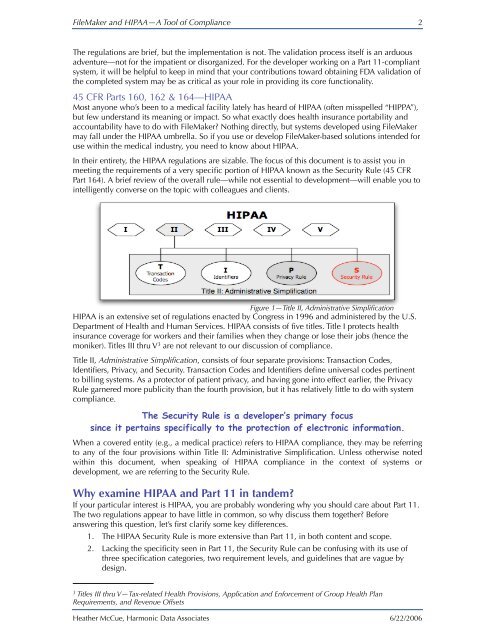
moniker). Titles III thru V3 Figure 1—Title II, Administrative Simplification<br />
are not relevant to our discussion <strong>of</strong> compliance.<br />
Title II, Administrative Simplification, consists <strong>of</strong> four separate provisions: Transaction Codes,<br />
Identifiers, Privacy, <strong>and</strong> Security. Transaction Codes <strong>and</strong> Identifiers define universal codes pertinent<br />
to billing systems. As a protector <strong>of</strong> patient privacy, <strong>and</strong> having gone into effect earlier, the Privacy<br />
Rule garnered more publicity than the fourth provision, but it has relatively little to do with system<br />
compliance.<br />
The Security Rule is a developer’s primary focus<br />
since it pertains specifically to the protection <strong>of</strong> electronic information.<br />
When a covered entity (e.g., a medical practice) refers to HIPAA compliance, they may be referring<br />
to any <strong>of</strong> the four provisions within Title II: Administrative Simplification. Unless otherwise noted<br />
within this document, when speaking <strong>of</strong> HIPAA compliance in the context <strong>of</strong> systems or<br />
development, we are referring to the Security Rule.<br />
Why examine HIPAA <strong>and</strong> Part 11 in t<strong>and</strong>em?<br />
If your particular interest is HIPAA, you are probably wondering why you should care about Part 11.<br />
The two regulations appear to have little in common, so why discuss them together? Before<br />
answering this question, let’s first clarify some key differences.<br />
1. The HIPAA Security Rule is more extensive than Part 11, in both content <strong>and</strong> scope.<br />
2. Lacking the specificity seen in Part 11, the Security Rule can be confusing with its use <strong>of</strong><br />
three specification categories, two requirement levels, <strong>and</strong> guidelines that are vague by<br />
design.<br />
3 Titles III thru V—Tax-related Health Provisions, Application <strong>and</strong> Enforcement <strong>of</strong> Group Health Plan<br />
Requirements, <strong>and</strong> Revenue Offsets<br />
Heather McCue, Harmonic Data Associates 6/22/2006