Communication Theory of Secrecy Systems - Network Research Lab
Communication Theory of Secrecy Systems - Network Research Lab
Communication Theory of Secrecy Systems - Network Research Lab
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
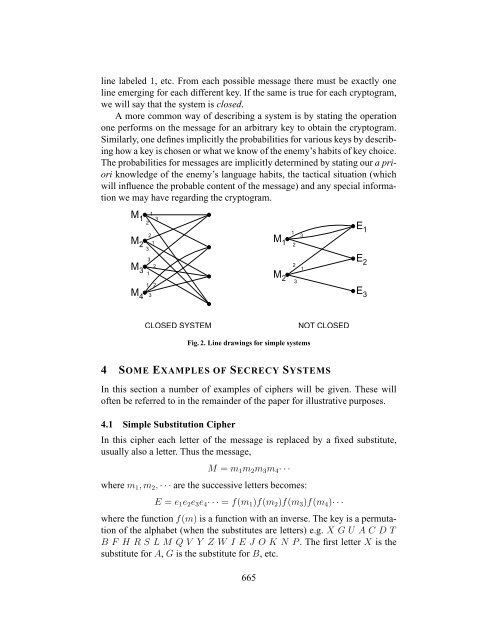
line labeled 1, etc. From each possible message there must be exactly one<br />
line emerging for each different key. If the same is true for each cryptogram,<br />
we will say that the system is closed.<br />
A more common way <strong>of</strong> describing a system is by stating the operation<br />
one performs on the message for an arbitrary key to obtain the cryptogram.<br />
Similarly, one defines implicitly the probabilities for various keys by describing<br />
how a key is chosen or what we know <strong>of</strong> the enemy’s habits <strong>of</strong> key choice.<br />
The probabilities for messages are implicitly determined by stating our a priori<br />
knowledge <strong>of</strong> the enemy’s language habits, the tactical situation (which<br />
will influence the probable content <strong>of</strong> the message) and any special information<br />
we may have regarding the cryptogram.<br />
M1<br />
M2<br />
M3<br />
M4<br />
2<br />
1 3<br />
2<br />
1<br />
3<br />
3<br />
2<br />
1<br />
1<br />
3<br />
2<br />
M1<br />
M2<br />
CLOSED SYSTEM NOT CLOSED<br />
1<br />
2<br />
2 1<br />
Fig. 2. Line drawings for simple systems<br />
4 SOME EXAMPLES OF SECRECY SYSTEMS<br />
In this section a number <strong>of</strong> examples <strong>of</strong> ciphers will be given. These will<br />
<strong>of</strong>ten be referred to in the remainder <strong>of</strong> the paper for illustrative purposes.<br />
4.1 Simple Substitution Cipher<br />
In this cipher each letter <strong>of</strong> the message is replaced by a fixed substitute,<br />
usually also a letter. Thus the message,<br />
M = m1m2m3m4· · ·<br />
where m1, m2, · · · are the successive letters becomes:<br />
E = e1e2e3e4· · · = f(m1)f(m2)f(m3)f(m4)· · ·<br />
where the function f(m) is a function with an inverse. The key is a permutation<br />
<strong>of</strong> the alphabet (when the substitutes are letters) e.g. X G U A C D T<br />
B F H R S L M Q V Y Z W I E J O K N P . The first letter X is the<br />
substitute for A, G is the substitute for B, etc.<br />
665<br />
3<br />
3<br />
E 1<br />
E 2<br />
E 3